
Cloudeight InfoAve Premium
Issue #698
Volume 14 Number 19
February 24, 2017
Dear Friends.
Thank you very much for subscribing and for being a part of our Cloudeight family. We appreciate your membership and support very much!

Cloudie has some big news for you - he'll be sending you a special email tomorrow morning (Saturday). So, keep your eyes open for Cloudie's big announcement. He wanted to make sure you'll all be looking for it. So, we promised him we'd tell you.
Cloudie will be visiting your inbox tomorrow morning!
Here are
some important links for you: Here are
some important links for you: Barbara wants to help a friend Our answer 1. She could download Windows 10 create an installation USB or DVD and
install it as a Windows 10 upgrade. Since Windows 10 was at one time installed
on her PC then she would not need an Windows Product key to upgrade to Windows
10 free. This would allow her to keep her programs and files. 2. She could do a factory reset. This would be restore her computer to the
state it was in the day it was purchased. While this would be the surest way to
make sure the PC was "as good as new", it would also mean she would lose any
files she did not have backed up on an external drive. While we could not install Windows 10 for her, we could help her make the
Windows 10 installation media and guide her through the process. When Windows 10
is reinstalled, we could come back and do a Windows 10 customization for her so
that her Windows 10 computer would look and work more like Windows 7. If she's interested, she can purchase a Cloudeight Direct Computer Care key
from http://thundercloud.net/direct/
. Elaine asks about defragging SSDs Our answer The warning you're getting is probably warning you not to defrag you SSD. Richard has a question about ransomware Our answer Best advice? Don't get ransomware in the first place.
Be careful, use good common sense, use good security software like
Emsisoft, and always be
wary.. but never be paranoid. Roy wants to find some passwords Our answer If you want to find passwords for email, you'll want to
read this article about MailPassView. And if you're looking to recover passwords for Web logins stored in your
browser, you'll
want to check out this page. We'd be remiss if we didn't remind you that you and everyone else needs a
good password manager to create, manage and store passwords. With a free
password manager like LastPass, you'll
never lose your passwords again. Not only that, but you can store any kind of
private or personal data in Last Pass' "Secure notes". Everything you keep
in "Secure Notes" is encrypted. We have come to the point where our security,
privacy, and safety requires a good password manager like LastPass. And there
are many other good free password managers available too. We prefer LastPass,
but it is not the only good one. The important thing is that you have one and
use it. We want you to stay safe!
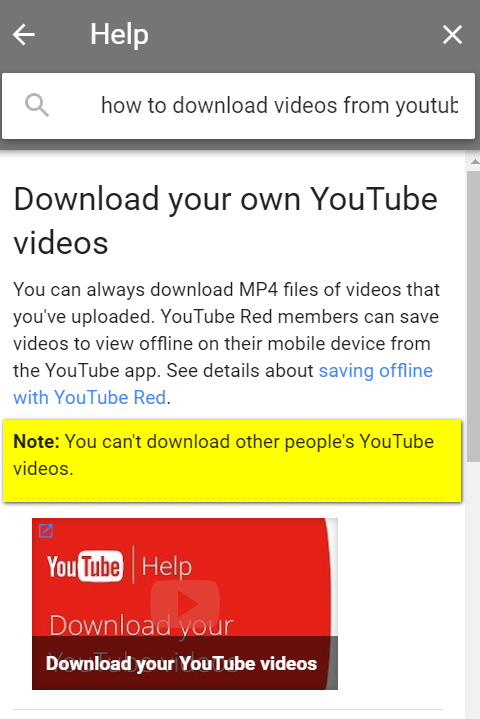
Annabelle asks us to re-check a site we once recommended Our answer We've done some digging and it seems that YouTube does
not allow you to download videos, unless they are your own. Downloading videos
other than your own is a copyright violation. In the future we will not be
reviewing or discussing any more YouTube downloaders because of this. If you
like a video, the best thing to do is send yourself the shortcut (link) to view
it, or log in and create channels and add any videos you like for quick access.
Because downloading videos other than your own is a copyright violation, we will
not be recommending any YouTube downloaders in the future. This is a good time to remind everyone that we have over 3000 posts on our
InfoAve web site. If you find something that was posted a year or more ago and
find something wrong, outdated or you have a question about it, please do tell us so we
can investigate. We want to be vigilant and keep everything on our site safe and
updated... but with so many articles, spanning so many years, we need your help.
Beware of the Google Chrome ‘Missing Font’ Hack
PLEASE NOTE:
Emsisoft
users are protected from this threat!
So DO NOT FALL FOR THIS TRICK. Your PC will be infected..
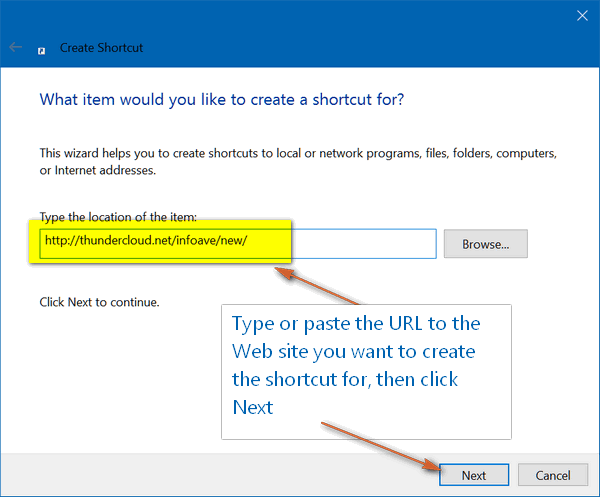
Create a Desktop Shortcut to
Your Favorite Web Site(s) If you have a web site or two that you visit often, you
might find it convenient to create a shortcut or shortcuts on your desktop. It's
easy to do and it only takes a minute or two. If you use Google Chrome or Firefox, you can drag
the "i" in a circle (or the "lock" if it's a secure site) next to the web
site's address to your desktop to create a shortcut to that site:
If you use Internet Explorer, you can drag the
site's icon (or the generic icon) to the desktop or pin it to your
taskbar.
If you're using Microsoft Edge, you can pin any
site to your Start menu or Start Screen. Just click on the menu (three
horizontal dots) and then click or tap "Pin this page to Start"
Or, you can do it the old fashioned way that
works with any browser. In fact, to create a shortcut this way, you don't
even need to have a browser open. 1. Right-click on an empty area of your desktop and
click New ---> Shortcut.
2. In the shortcut dialog that appears, type or paste
the URL (web address) of the site you want to open when you click your new
shortcut.
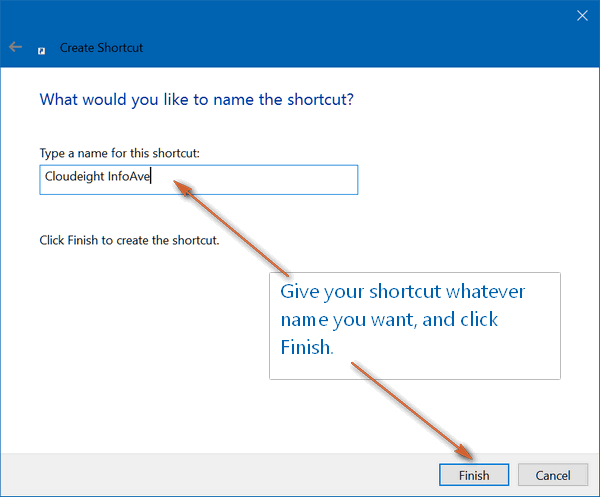
3. In the next dialog, you'll have a chance to name
your shortcut. This is the name that will appear under the shortcut icon on your
desktop. Name it whatever you like.
And that's all there is to it. Shortcut created. Can
you see the one I just created below?
Three Easy
Tips For All Windows Users Look above. If you click on "Delete searches & browsing
activity, you'll see this: " Delete searches & browsing activity You can delete your past searches or other activity
from your Web & App Activity page. Learn more about what's saved in your Web &
App Activity.
"Remove information from Google You can change your settings, filter search
results and do all kinds of things your probably didn't know you could do. Above: Google has some interesting videos to help
you... plus some educational resources as well.
All this is on one arcane page that most people never
knew existed. But now you do! Visit
this page out right now learn more about Google Search and take control. What's the Best Way
to Get Rid of Ransomware? There is no one way that will keep you 100% safe from ransomware, but if you
follow some simple guidelines, your chances of being infected with
ransomware will be much less than average.
Here are our guidelines to
help keep you safe from ransomware: NEVER open attachments in email. Not even if you think you know who sent it. If
someone wants to send you an attachment by email, make arrangements with them
before hand - so you're expecting it and you know what it is they're sending. NEVER click links in email unless you are sure who sent the email. Don't assume
if you get an email from uncle Larry that it's really from uncle Larry. If it
seems odd or unlike something you normally receive from him... be wary. His
email address may have been compromised and he is not even aware that the mail
was sent. It's easy to forge email addresses and headers. If you're not sure.
who sent an MAKE SURE. If you're not sure, it only takes a minute to write the
sender and ask - or if they're a friend of yours, call and ask them. ALWAYS make sure you're using a top-rated antivirus/anti-malware like Emsisoft.
One than can help protect you from many of more prevalent ransomware. No
software can ever keep you 100% safe from 100% of all threats, because hundreds,
even thousands of new, perhaps more sophisticated malware/ransomware appear
every day. With millions of dollars in profits awaiting distributors of
ransomware, a lot of new miscreants get in the game every day. NEVER use outdated operating systems or outdated browsers. Always keep your
browsers and email programs updated. Never use outdated version of Adobe Flash.
Be careful when installing browser add-ons. Always keeps you add-ons up-to-date.
If you're using Windows XP or Windows Vista, you're vulnerable. If you're using
a browser that is not updated, your vulnerable. Don't install any browser
add-ons or plug-ins you really don't need. NEVER visit sites where porn, illegal software, or software "cracks" are
distributed. These sites are rife with scripts and potential
drive-by-downloads... not to mention poisoned links and advertisements. Steer
clear of the back alleys of the Internet. ALWAYS try to keep one back up of your personal files that is on media that's
not constantly attached to your computer. Dropbox, OneDrive, iDrive and external
drives are great for keeping backups, but if you become infected with
ransomware, it's highly likely that files you have stored in the cloud and/or on
external drives which are plugged into your computer at the time of infection,
will be infected as well. Keep several USB flash drives handy, and every week
backup your personal files - then unplug the USB(s) from your computer. ALWAYS use common sense. ALWAYS THINK before you click. If you follow these
simple guidelines, your chances of getting ransomware will be much
less than average.
A Quick and Easy Browser Security Tip When it comes to browser add-ons / extensions - the less you have, the faster
and safer your browsing experience will be.
Donations help us continue our mission to keep you informed, separate
the truth from the hyperbole, and help you stay safer online. We provide
support to thousands of people. Every week we help dozens of people via
email at no charge. Thanks to donations, we do a lot more than provide
this free newsletter. We help you recognize online threats, fight for
your online privacy, and provide you with the knowledge you need to
navigate the Web safely, and help you get more out of your PC.
Help us keep up the good
fight with a small donation.
It's the beginning of a new year, and we really need your support.
We hope you'll
take a few minutes today and help us with a small donation.
Help us keep up
the good fight with a small donation.
We would really appreciate it.
What Email Program Do You Use?
Let us know what email program you use by voting in this week's poll!
Getting Old
Read the rest of this essay here.
Takeafile Take a file... any file, and share it with anyone, anywhere, anytime. Fast,
free, safe, and convenient. That's what we all want. And with our site /
freeware pick, we found the best file sharing service we've ever seen. Some of you might already know that Gmail will not let you share certain
types of files that could be used to send dangerous payloads. Other web mail
services may have restrictions on the types of files you can share by email.
Plus, we continually warn everyone not to click or open files that come via
attachment unless you are positive who sent them, what they are, and you've
double-checked them with your security software before opening the
attachment(s). Takeafile makes it easy to share files with
anyone - no worries about attachments! You can share a singe file or a
folder of files up to 500MB.
You can see from the screenshots above that we really
do test this stuff! Here's some of the things we like about Takeafile Easy Fast Safe Cloud or Not No Sign up Required The developers are not
laconic, they would love to tell you more about their site and free service: "No size limitations. While other services such as
Gmail may have size limits of 25MB Takeafile can send any file of any size as
long as the receiver has enough free disk space of course. "How anonymous is it? "How safe is it? "How easy is it to use? "How does it work? "How to send multiple files? And they have tons more to tell you ... and I'm not
kidding! If you're looking to share or send files to friends,
business associates, family members, or anyone else, you're going to like our
site /freeware pick called Takeafile. You can read a lot more about Takeafile
by visiting Takeafile right now. So don't
takeuptime, takeafile,
I tells ya! NOTE: *** Because we are careful about what we
recommend, when we didn't see how this site was supported (no ads, no
fees, no paid services), we wrote to Takeafile to see if they could tell
us anything. We got an answer within 20 minutes - a really good sign. This
is what they told us: We think you'll find
Takeafile a great way to
share files with anyone.***
Donations help us continue our mission to keep you informed, separate
the truth from the hyperbole, and help you stay safer online. We provide
support to thousands of people. Every week we help dozens of people via
email at no charge. Thanks to donations, we do a lot more than provide
this free newsletter. We help you recognize online threats, fight for
your online privacy, and provide you with the knowledge you need to
navigate the Web safely, and help you get more out of your PC.
Help us keep up the good
fight with a small donation.
It's the beginning of a new year, and we really need your support.
We hope you'll
take a few minutes today and help us with a small donation.
What is Bitcoin? Bitcoin used to confined to the realm of the super geeks, but not anymore. It's big
business and we think you should have a basic understanding of bitcoin. That's
why we're including it in today's Back to Basics!
![]()

A comment from Don
TC. I must tell you that Emsisoft , along with Cloudeight, is
perhaps the best thing that ever happened to my computer and my computing.
Add to that Windows 10 and I simply have zero problems with my computer.
It used to be I was constantly having to restore, fix, repair, reboot,
reinstall, etc., etc., etc. Now I seldom have any kind of problems. I give
you, Cloudeight, much credit for this. You guys are absolutely the best
thing since iced tea, and I am in your debt for even telling us all about
Emsisoft. What a great program very reasonably priced. Many thanks for all
you do for all of us. God bless.
A comment from Dick
That tip about all the conversion capabilities of the Calculator was very
helpful All these years I had no idea that it did anything other than add,
subtract, multiply and divide. I'll bet that 90% of Windows users have any
inkling of this tip! I've also benefited from many other tips of
yours...for which, sincerest Thanks!
A commend from Becky
Thank you, Darcy for a great job on my PC and my husband's laptop.
Installed Emsisoft on both and got my PC up to speed - FINALLY!. Great
job. Cannot thank you enough.
A comment from Frank
Thank you for fixing my computer, TC. I didn't really think anyone could
fix it, but you did. When I offered you extra money for going the extra
mile for me, you refused. You told me I had already paid for your service.
There are not many companies left in the world like Cloudeight. I want to
thank you again for a super job well done.
A comment from May
I agree with Debbie C. In fact she is the one who recommended you guys to
me! I just have not been with you since you began, but everything else she
said is certainly true!
Thanks so much to Don, Dick, Becky, Frank, May and everyone
who wrote to us last week. And thanks all those who used our Cloudeight Direct
Computer Care services . TC & EB

![]()
![]()

Hi TC/EB, I don't recall seeing this question in your newsletter before
and it might be relevant to a few out there. A friend's son bought her a new
computer with Win 10 on it. She didn't like it so paid someone $200 to remove it
and install Win 7! She is continually having issues with it. My question is
this: Can Win 10 be installed on that computer again without doing a clean
install or does it have to be wiped clean and reinstall Win 10 and from where
would she get it? I don't think she has a hard disk nor a back up. Is this
something C8 could do and set it up so it would look more like Win 7 so she
would enjoy it and leave it alone? Thanks for your expert advise. Barbara
Hi Barbara. Wow ... she spent $200 for this? Hard to believe. If
her computer came with Windows 10 and have it downgraded to Windows, she's
probably got a mess. The computer's drivers and hardware were most likely
certified for Windows 10. She has a couple of choices and they are:![]()
I have a Dell desktop with a 930 GB HDD. It was upgraded from 8.1 November 2015.
I never bothered with defrag as I read it was automatic in Windows 10. I
defragged an external HDD January 2017 and must have selected drive C as well.
Now the defrag window reads "no optimization available" and the HDD is now an
SSD. Reading what I could find on the web it seems this can only be reversed
with a clean install of windows. That I'm not prepared to do. Have run winsat
format (command) with no success. Have now installed and run Defraggler but
would prefer to use the built-in programme. Can you help please? Thank you.
Elaine
Hi Elaine. SSD drives are solid state drives; they have no moving parts... and
never need defragging. HDD is a simple hard drive without fixed sectors; it has
rotating platters. They're the hard drives that have been around for a long,
long time - and they're cheaper than SSD.
An SSD does not and cannot change to HDD, and vice versa. Both SSD and HDD are
hardware not software. Never defrag an SSD - it's not necessary and may damage
the drive. And defragging HDDs is done automatically in Windows 7, Windows 8.1
and Windows 10. Normally there is no need to do a manual defrag - and certainly
no need for 3rd party defrag software.![]()
Regarding ransomware: If I copy my documents, Excel files, word files and other
flash drive data to a flash drive and immediately unplug it, will I be protected
as Ransomware doesn't encrypt programs ? Please advise and thank you.
Hi Richard. The files you copied to your USB flash drive would be safe, but your
computer would not necessarily be safe. If you did get infected with ransomware,
any personal files (pics, docs, music files, etc.) would be vulnerable to
ransomware. But the files you copied would be safe. You're correct in
saying that ransomware does not encrypt programs.![]()
You featured an article regarding" finding passwords", can you please
tell me how to find it again. Thank you
Hi Roy. There are many ways to find password. You can use Asterisk Key
to find passwords hidden beneath ******* asterisks. We wrote an article about
Asterisk Key several years ago, and
you can read that article here.![]()
Hello to you both and hopefully Spring is around the corner! I have a
question? Could you please check this site and see if it is still safe. It is
saying we have to install and download some extension to Chrome before I can
download a video from YouTube. I didn’t do it… I figured I’d bring it to your
attention and ask your experts opinion. Thanks and hope you see this.
Hi Annabelle. We went back and double-checked and you're right. The
site featured in our post from November 2015 now requires a questionable
download and we no longer recommend you use that service. We have removed the
content and links from that post - thanks to you.
![]()

![]()

Everyone who uses Chrome
This week a very well executed malware attack aimed at Chrome users who
visit compromised web sites was found by Mahmoud Al-Qudsi of NeoSmart
Technologies. The hack tries to trick users into believing the reason why
the font on the page they’re visiting is garbled and unreadable, is
because the their PC is missing a font.
Before we post the article that explains this hack, let us warn you that
no site is going to warn you that you’re missing a font. The way Web sites
work is – if a site uses a font that is not installed on your PC, you’ll
see the site’s font in whatever your default font is – you won’t see a
garbled, unreadable mess.![]()
Windows 7, Windows 8.1, Windows 10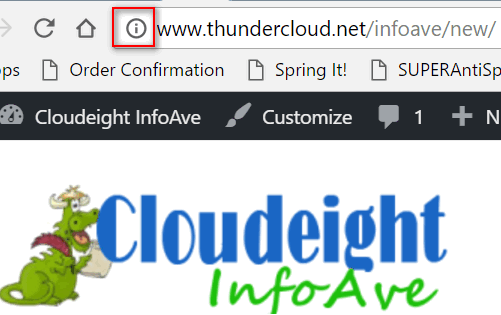
Above - Chrome browser - Firefox looks essentially the same.
Above: Internet Explorer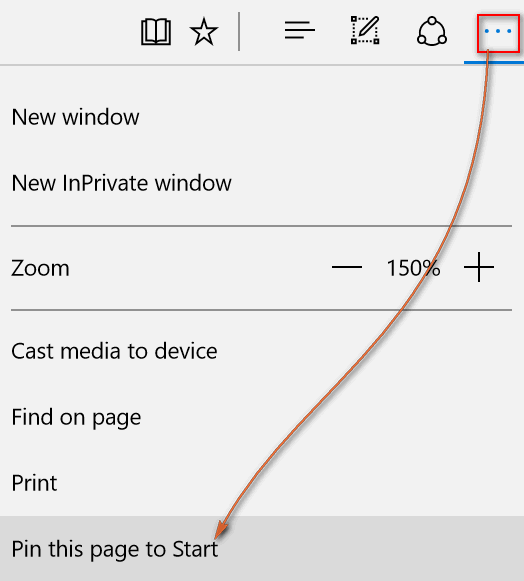
Above: Microsoft Edge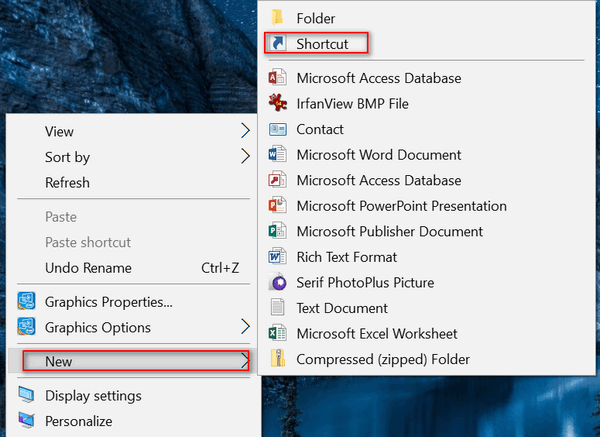
![]()
Windows 7, Windows 8.1, Windows 10
Spaced Out
You can highlight a word, a sentence, a paragraph or a page and delete the
entire block of selected text by pressing the “Space” bar. Yes you can, and now
you know!
Tabby Treats
Pressing the “Alt” “Tab” keys in sequence allows you to browse through your open
windows.
A New Mail Message
Did you know that in most Email programs you can start a new message by simply
pressing the Ctrl + “N” keys?
Open a new browser Window
If your browser is open, pressing CTRL + N will open a new browser window.
No EB, that's not 4 tips - that's 3 tips. CTRL+N only counts as one. I'm
nothing if not fair!
![]()
Google Help, Resources, User Controls and More
Windows, Android, Apple
Google has a help center that is really helpful. Did you know when you search
using Google, when you're signed in to your Google, your searches are saved
online. Indeed they are, and clearing your browser's history won't clear the
stuff on online, but you can clear it and also prevent it, but you have to know
where to go and what to do. That's where Google's Help Center comes in.
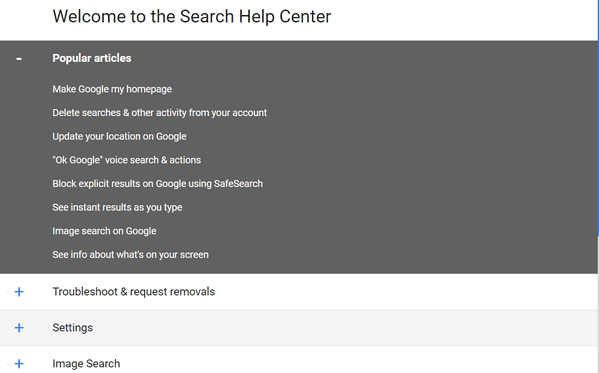
Your searches and browsing activity are saved in your Web & App Activity when
it's turned on and you're signed in to your Google Account. You're in control of
what's saved, and you can delete it or turn the setting off whenever you like.
Delete your searches & browsing activity
Computer
Android
iPhone & iPad..."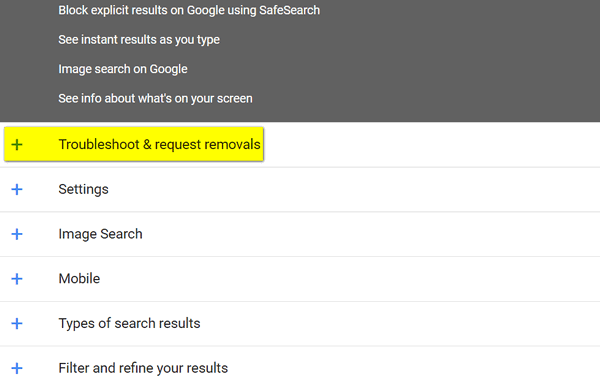
Above you can troubleshoot and request removals...
You can ask Google to remove your sensitive personal information, like your bank
account number, or an image of your handwritten signature, or a nude or sexually
explicit image or video of you that’s been shared without your consent, from
Google search results.
What Google will remove
See our Removals Policies to learn what information Google will remove..."

![]()
Windows 7, Windows 8.1, Windows 10
The best way to get rid of ransomware is not to get
it in the first place.
Ransomware is now the biggest threat you face. Back in the 1990's viruses and
Trojans were the big threats. In the early 2000's, it was spyware, but soon
malware became an all-encompassing term for viruses, rootkits, Trojans, spyware,
PUPs, etc. Ransomware is also malware - and it's at the top of the list because
of the damage and financial losses it causes.
We're living in an age where the miscreants, hackers, and criminals that target
our computers, are becoming much more sophisticated. Most ransomware is spread
by spam and phishing emails. And, unlike the old Nigerian Prince emails of the
past, you can no longer easily and quickly identify spam because of ridiculously flawed spelling
or grammar. The criminals who spread ransomware - and who are now making
millions of dollars doing it - are much more sophisticated than good, old Prince
Pnumbla from Nigeria. While it's true that most
spam and phishing emails containing ransomware are sent from developing nations, many times they're
written in nearly perfect English. It's amazing what you can do when you have a
lot of money like some of the criminals that distribute ransomware.
Ransomware is spreading wildly not only because of the sophistication of the
miscreants who propagate it, but because of the wall of anonymity they can hide
behind. Things like Bitcoin and encryption make those behind ransomware almost
impossible to trace. When ransoms are collected
in Bitcoin (Bitcoin is a cryptocurrency.
Learn more about it here.), it's nearly
impossible to trace the payment back to the criminal. This makes the chances of
catching the villains who distribute ransomware, very slim. And that makes it a
very attractive way for criminals to make a lot of money with
very little risk of getting caught.
If your computer becomes infected with ransomware, some or all of your personal
files will be encrypted... and you won't be able to access them without the
encryption key. The criminals who distribute ransomware, will provide you with the
correct key to decrypt your files... for a price. The average price is about
$300 (USD). If you don't pay the ransom, you won't to be able to
access personal files such as pictures, documents, music, etc. Even if you have
backups in Dropbox, OneDrive or on external drives, the files you have backed up
may also be encrypted.
The best way to get rid of ransomware, isn't to follow complicated removal
instructions, or trying to find the right decryptor, or paying a ransom to the
criminals who hold your files hostage. The best way to get rid of ransomware is
to not get it in the first place.![]()
For everyone
There's no doubt that add-ons and extensions can be fun, useful, and add
functionality to any browser. However, add-ons and extensions can also be
vectors for exploits, and browser hacks.
This weekend, take a few minutes and look at the number of browser extensions /
add-ons you have. Disable the ones you seldom use and remove the ones you never
use. ![]()

After you donate, you will receive info on how you can become a
Cloudeight Booster.
![]()

![]()

It's been an amazingly warm winter this year. In fact, today is February
23, and it's 70 degrees. Now, you might think I'm sitting at some
outdoor cafe in Key Largo, but actually I'm up here in the northern part
of the Midwest. Crazy warm!
Because it's been so warm lately, I've been thinking about gardens, and
summer, and that kind of thing. This afternoon, being that it felt like
the month May outside, I decided to move the logs I had once toted
--from Heaven knows where -- to use as a border around the garden that I
painstakingly laid out decades ago. I wanted to get old rotting logs out
of the way - they have become nothing but a grass-mowing obstacle course
and a home for ugly, slimy bugs. I don't need the hassle.
Well, let me tell you those logs were heavy. They were much heavier
today, taking them out, than they were putting them in forty years ago.
I’d like to tell you there were they were water-logged and actually
heavier, but the fact is, I’ve getting old. Those logs I hauled in and
laid around the garden as a border four decades ago, went in much easier
than they came out today.
After decades of planting gardens, weeding gardens, tending gardens,
fighting bugs, plant diseases and too-much-rain, not-enough-rain, too
cold, too hot, frost, floods and drought, I decided that I had had
enough of gardens. Enough! I said to myself.
Every year I’ve threatened not to till up the garden and just mow over
the weeds with the lawn mower and be done with it. This year I decided
to actually go through with it. Why? Because I am old and I am wise.
I figured out that last year I spent about $500 growing about $50 worth
of tomatoes...![]()
Reg
Organizer - A Swiss
Army Knife of Windows Utilities and Tools
Reg Organizer works on Windows 7, Windows 8, Windows 8.1 and Windows
10. The newest version of Reg Organizer has newly added special tweaks
for Windows 10 - including a Windows 10 Start menu fix.
Get more information and
or order Reg Organizer today and SAVE!
![]()

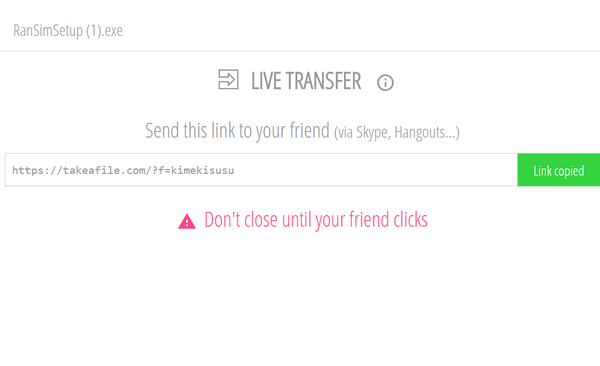
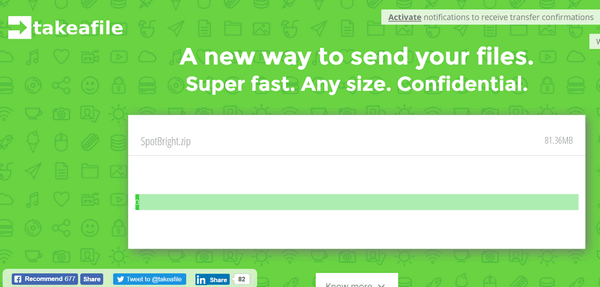
You can send file direct to anyone you like. You don't have to upload to a cloud
drive (like iCloud, Dropbox or OneDrive). You choose the file or folder of files
you want to send, drag it to the Takeafile web page. You share your file or
folder directly, in just a few seconds.
Takeafile claims that file transfer speeds are up to ten times faster than cloud
drives. They explain that he reason is that the file is not uploaded to the
cloud, it's sent directly to the recipients. I tested it -- and I don't have the
fastest internet connection, and I transferred a 2.2 GB file using Takeafile in just a few
minutes.
When you transfer files directly, your files are not stored on any server. That
means no one but you and the person you're sending them to will ever see them.
Your files are encrypted and sent directly to whomever you choose. If you're
sharing files directly, there's no size limit. However, sharing files directly
means you'll have to leave the page open in your browser until the recipient has
downloaded your file or files. Additionally, direct transfer can only be used
with Chrome and Firefox browsers -- as of right not.
If you want to share files with several people, you can use their cloud feature.
You can upload a file or folder up to 500 MB when using the cloud feature then
share your files with several people at the same time. Files are encrypted and
will automatically be deleted after 7 days.
You don't have to sign up or give you email address to anyone to use Takeafile.
"Why is it better than Dropbox or Google Drive?
"These services have a space quota. Once it is full you have to remove files by
hand or pay for more space. With Takeafile your file is not stored in any
server, only in the receiver computer. Send the file and forget about it, no
worries!
"Ok, but what are the drawbacks?
"The only drawbacks include having to keep the webpage open until the file is
transferred and compatibility is limited to Chrome and Firefox at the moment.
"To send a file, neither the receiver or the sender have to provide any
information. Further more the file you are sending goes straight to the
receiver’s computer without any extra servers involved.
"All files are encrypted and sent straight to the receiver’s computer. As such,
even if a malicious user gets the file by sniffing the network, they will not be
able to open it. Only the person you share the URL with will have access.
"You don’t need to install anything; all you need is a browser (right now we only
support Chrome and Firefox). The receiver just clicks on the link and the
download will automatically start. Easy Peasy.
"We use the WebRTC capabilities to send data in a peer-to-peer fashion (from one
computer to another) through the Internet without using any intermediate
servers. To temporarily store the file in your hard drive instead of in main
memory, we use the FileSystem API for Chrome and FileHandle API for Firefox. We
first download the file to this temporary storage and when the download is
complete we move the file to your downloads directory.
In Chrome you can drag and drop a folder or several files and they will be
zipped instantly (the zip will be streamed so it will not create a copy of the
flies). You can also click to open the file browser and make a multi-selection of
files. The receiver will get a regular zipped file (the receiver can also use a
different browser such as firefox)...Right now our platform is completely free,
and it will be like this forever. This has an explanation: when a user
sends a file to another user, data goes directly from the sender to the
receiver, without using intermediate servers (unlike other platforms like
WeTransfer, Dropbox, etc.). As we do not have to pay for these servers, we
can offer the service free of charge.
We are now understanding the needs of our customers and refining our
platform. In the mid term, we will offer a desktop version of Takeafile, a
desktop app for professionals. It will work as the Takeafile webpage but
with extra productivity features.
After you donate, you will receive info on how you can become a
Cloudeight Booster.
![]()

Bitcoin is a form of cryptocurrency that is not printed or minted or controlled
by any entity. It's an exchange form that is controlled by no one. More and more
online stores and financial institutions are accepting Bitcoin as payment.
Because bitcoin is traded anonymously you can buy thing or accept payment in
bitcoin without revealing your identity. This makes bitcoin the payment form of
choice for criminals and miscreants who develop malware and ransomware.
Who accepts bitcoin as payment? As of today, February 23, 2017 here are some:
Overstock.com, Target, CVS, WordPress.com, Subway, Victoria Secret, PayPal,
Expedia, Home Depot, Kmart, Sears, the Apple App Store, Grooveshark, Dell and
Zappos. Additionally, products from several other companies, such as Whole Foods,
The Gap, Game Stop, and JC Penney, are available through BitCoin by using the
cryptocurrency to buy gift cards from sites like Gyft and eGifter.com.
Some sites accept only bitcoin payments exclusively. Bitcoin.Travel is a site
for making travel reservations with bitcoin. Meanwhile Domino’s Pizza set up
PizzaForCoins.com. Bitcoincoffee.com is another example of a site catering
specifically to Bitcoin users. Even the Republican Party of Louisiana accepts
Bitcoin donations.
As of today, one bitcoin is worth $1159.37 USD according to
CoinDesk.com.
The following information is also from
Coindesk.com
"Bitcoin can be used to buy things electronically. In that sense, it’s like
conventional dollars, euros, or yen, which are also traded digitally.
Where can you buy bitcoin?
"However, bitcoin’s most important characteristic, and the thing that makes it
different to conventional money, is that it is decentralized. No single
institution controls the bitcoin network. This puts some people at ease, because
it means that a large bank can’t control their money.
"Who created it?
"A software developer called Satoshi Nakamoto proposed bitcoin, which was an
electronic payment system based on mathematical proof. The idea was to produce a
currency independent of any central authority, transferable electronically, more
or less instantly, with very low transaction fees..."
www.coindesk.com
www.localbitcoins.com
www.bitquick.co
www.coincorner.com
www.bitbargain.co.uk
www.xapo.com
To name just a few. You can buy and sell bitcoin like commodities or stocks.
Bitcoin value varies greatly. If you would have bought 100 bitcoin in 2010 for
$27, it would be worth about $116,000.00 today.
See EB, I told you we should have
bought bitcoin instead of stock in Soda Stream! You never listen to me!![]()
![]()

- Premium Subscribers' Home Page You'll find the last few weeks of Premium archived on this page.
- To change your subscription address, see "Manage your subscription" at the bottom of this newsletter.
- Submit your questions, comments, and suggestions for possible inclusion in our newsletters here. This form is for questions, comments and suggestions for this newsletter, not for product support, stationery questions, or general questions concerning our products or services.
- Submit your Windows tips and tricks here.
- Send us your suggestions and recommendation for future freeware picks and/or sites of the week.
- Follow us on Twitter
- Help us Grow! Forward this email newsletter to a friend or family member - and have them sign-up for InfoAve Premium here!
- Get our free daily newsletter! Each evening we send a short newsletter with a tip or trick or other computer-related article - it's short and sweet - and free. Sign-up right now.
- Have a question about a Cloudeight Software program, service, stationery, or need to ask about an order? Let us know!
- If you need help with one of our software programs, have a question about an order, or have a question about any of our email stationery, screen savers, or other products - please don't use our InfoAve Questions/Answers/Tips form. Please use our general Cloudeight support form instead.
- If you want to help us by telling your friends about our Cloudeight Direct Computer Care service, you can download a printable flyer you can handout or post on bulletin boards, etc. Get the printable PDF Cloudeight Direct Computer Care flyer here.

These products and services are recommended and endorsed by Cloudeight:
Emsisoft Anti-Malware- The best anti-malware you'll find anywhere. Great protection -- both proactive and reactive. Learn more here.
Reg Organizer-- A Swiss Army knife of PC tools. Easy for beginners to use -- with advanced features for experienced users too. Learn more here.
Cloudeight Direct Computer Care - Computer Repair Service-- And for computer repair, you can't beat our remote repair service. You never have to leave your home, take your computer anywhere or leave it with someone you don't know or trust. We can fix most computer problems and all you have to do is sit back and relax. Learn more here.
Thunderbird Email Setup - we'll set up Thunderbird for you - works great with Windows 7, Windows 8 and Windows 10. Get the details here.
Windows 10 Customization - Make Windows 10 look and work the way you want it to. Get more info here.
Also.. don't forget:
We're offering something we think most of you will enjoy. We have a daily tips and tricks summary newsletter that is sent six days a week. It features daily tips, freeware picks, and site picks and interesting computer tips, tricks and more. It's short and sweet - very brief and lightweight. If you'd like to receive or daily tips and tricks newsletter (completely free, of course). You can subscribe here.
You can also help us by using our Start Page.
We have over 100 free games to our Start Page too - come and play all day. It costs nothing to use our Start Page--and helps us a lot.
Your Premium Members' Home Page is located here.
![]()
We'd love to hear from you!
If you have comments, questions, a tip, trick, a freeware pick, or just want to tell us off for something,, please visit this page.
If you need to change your newsletter subscription address, please see "Manage your subscription" at the bottom of your newsletter.
We received hundreds of questions for possible use in IA news. Please keep in mind we cannot answer all general computer questions. We choose a few to use in each week's newsletter, so keep this in mind. If you have a support question about a service or product we sell, please contact us here.
We hope you have enjoyed this issue of
InfoAve Premium.
Thanks so much for your support and for being a Premium subscriber.
Have a great weekend! Darcy & TC
Cloudeight InfoAve Premium - Issue #698
Volume 14 Number 19
February 24, 2017
Subscribe to our InfoAve
Premium Newsletter![]()
DISCLAIMER ABOUT THE TIPS
& SOFTWARE RECOMMENDED IN THIS NEWSLETTER-- PLUS OTHER
IMPORTANT INFO:
All software recommendations we make in this newsletter are based on
our own experience and testing of the programs that we recommend. This
does NOT guarantee they will work on YOUR computer. We assume you will
read the program documentation and use the program according to the
instructions. We make no guarantees about any program recommended in
this newsletter or its suitability for any particular purpose. We will
not be responsible for any problems you may have. We do not and cannot
provide support for any products other than our own Cloudeight products
and we will not answer email concerning any product which is not a
Cloudeight product. We urge you to use good judgment when downloading
and installing software and to use a program only after reading the
program's documentation. And, all Tips & Tricks in this
newsletter have been tested by us on several different computers and
were found to work as indicated. They may not work on yours. We make no
guarantees. Anything we recommend you try and use at your own risk. We
will not be responsible for any problems caused by any software
programs recommended in this newsletter or any of the tips and tricks
in this newsletter.. Readers' comments are their own and Cloudeight
Internet LLC is not responsible for comments of our readers. All
readers' comments, suggestions, questions, and tips and tricks sent to
us become the property of Cloudeight Internet LLC. You understand that
we may use your comments without your explicit permission.
"Cloudeight InfoAve Premium" newsletter is published by:
Cloudeight Internet LLC
PO BOX 73
Middleville, Michigan USA 49333-0073
