
Issue #864
Volume 17 Number 28
May 1, 2020
Dear Friends,
Welcome to Cloudeight InfoAve Weekly Issue #864. Thank you very much for subscribing and for being a part of our Cloudeight family. We appreciate your friendship and support very much! Please share our newsletters and our Website with your family and all your friends.
We wish you all the best during the global pandemic. Our prayers and good wishes go out to all of you during this difficult time. We are all in this together.

We need your help! Please help us keep on helping you!
When you support us with a small gift, you help us continue our mission to keep you informed, separate the truth from the hyperbole, and help you stay safer online. Plus, our computer tips make your computer easier to use.
Did you know that we provide support to thousands of people? Every week we help dozens of people via email at no charge. The questions and answers you see in our newsletters are from the email answers and help we provide to everyone free of charge.
Thanks to your gifts, we do a lot more than provide this free newsletter. We help you recognize online threats, fight for your online privacy, provide you with the knowledge you need to navigate the Web safely, provide you with suggestions for safe, free software and websites, and help you get more out of your PC.
Please Help us keep up the good fight with a small gift.
Interested in making an automatic monthly gift? Visit this page. Help us keep helping you... and helping you stay safe on the Web![]()

A comment from Doug
I just used Cloudeight Direct for the first time and I can tell you
these people know what they're doing. They explain what they are doing
and I sat there amazed as the cursor moved all over the screen. When
Cloudeight was done, my computer problems were done! It's amazing to
watch them work and my computer works so much better. Before my laptop
was horribly slow and now it's fast and a pleasure to use! Thanks,
Cloudeight!
A comment from Leza
For several weeks I tried to fix my computer that I had messed but to
no avail. So I asked for help and Darcy came to my rescue, in five
minutes she had fixed me up. Thanks so much, Darcy, you and TC are the
greatest. With most places shut down I would have been stuck with my
messed up Computer... Thanks Leza.
A comment from Nick
A big THANKS to TC for checking out my laptop. It was giving me
trouble since doing the most recent Windows 10 update. After TC
connected to my computer and whizzed around checking and optimizing
things, all is running well now. Thank you. I want to mention that I
had Darcy work on my desktop last winter and she was amazing too! I am
so glad we have TC and Darcy to help us with our computers! Thank you
so much! Nick
A comment from Janice
Thanks, TC & EB for making it even simpler to renew Emsisoft!! Once
paid for, you handle EVERYTHING!! I was simply amazed to find I didn't
have to even type in one thing like before--WOW! Sure doesn't get any
easier than that. You two are TOPS and so is Emsisoft! Janice.
A big Cloudeight "Thank you!" to Doug, Leza, Nick, Janice and everyone who took time out to write to us, share a comment and/or share us on Facebook! We appreciate your kind words and your support very much! EB & TC.
![]()
Your Purchase Helps Us!
When you purchase any Cloudeight Direct Computer Care Service, you get the best computer care and repair, at the lowest possible price. Plus, each Cloudeight Direct Computer Care service you purchase goes a long way in helping to support our small business.
Your computer fixed - while you watch!
With our Cloudeight Computer Care, we'll fix your computer while you watch. You'll be getting the best computer repair service available, at the best price, from people you trust. Our Cloudeight Direct Computer Care single repair keys are a great deal. They are good until you use them.
For more information see our Cloudeight Direct Computer Care home page! ![]()
Robert received an email attempting to blackmail him
I received an e-mail from someone calling himself Johnny Dobens.
The e-mail is requesting I send him $2000 in bitcoin. His e-mail
indicates that he has a password of mine that I can't remember any site other
than MySpace that I never ever use. I do use the same passcode when
questions are asked to Identify myself.
In the e-mail I received from this person and he's indicating that he
placed malware in my computer having my Facebook contact list, mobile
phone contacts - plus 173 days of online activity on my computer. He
indicated he has videos showing me doing ( private things)... Because of
some stories I read about being able to view images through the webcam I
usually place a covering over my computer webcam. I have a technical
support group through System Mechanic Professional Iolo Technology. I
have been trying to call them about this issue but because of the
Coronavirus it's almost impossible to get hold of them so they can
access my computer. The same is true with my e-mail internet provider. I
guess I should go online to their help support group and present this to
them via e-mail as well.
Anyway, I know this is a scam and all the things you can do with
photographs by placing a persons face on distasteful activity. Can You
give me some advice on what I should do? Should I ignore the e-mail?
Also, I scan my computer with System Mechanic regularly, and they have a
malware scan I use and there is no indication that when I scan through
them that there is any malware on my computer. I, also use
SuperAntispyware to scan my computer and they usually find tracking
cookies that are deleted... Your expedient response will be appreciated.
Our answer
Hi Robert. Don't worry. Delete the email and forget it. We get at least
10 of these - or more- every week - they come to our business accounts
and personal accounts. We have been getting these for years. I bet by
now Darcy and I have gotten more than 1000 of these. We just delete them
and we STRONGLY recommend you delete the email and forget about it.
These emails are sent out by the billions looking for vulnerable people
who actually pay these miscreants.
While you may think there are personal items in that email, there are
not. We have written about blackmailing by email before. For instance,
read our article here. After you read that you'll realize you're not
alone and you'll learn that these kinds of emails, attempting to
blackmail people, are just spam sent by the billions looking for
gullible people who actually do pay these criminals.
Delete that email and forget it. Nothing is going to happen to you.
Note: Regarding System Mechanic. System Mechanic is not even rated in
the top 20 antivirus on any independent testing laboratory we know of.
It's not a very good way to protect your computer. Also, we have not
recommend SuperAntiSpyware since it changed hands many years ago.
We recommend Emsisoft
Anti-Malware (and antivirus). It's always rated among the top
antivirus programs and in our opinion it's the best anti-malware
solution available. However, it is our responsibility to tell you that
no
antivirus or antimalware is going to protect you from getting these
kinds of emails.
![]()
Terry wants to know how to clear browsing history in the New
Microsoft Edge
I recently installed the new Microsoft Edge browser and I really like it. But
I need your help. How do I clear the browsing history in the new Edge?
Here's hoping you can help this novice! Thanks for all you do. Terry
Our answer
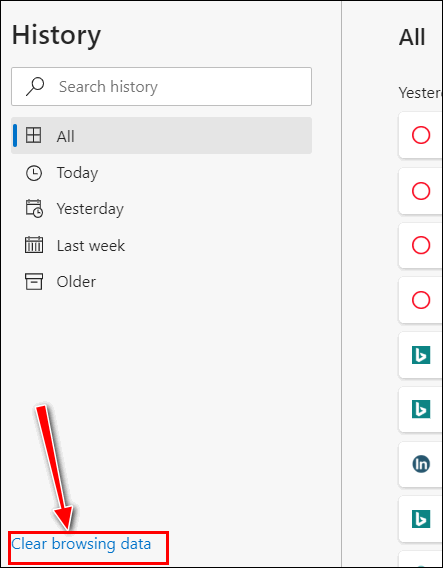
Hi Terry. Thanks! It's really easy to clear browsing history in the new
Edge.
1. Open Edge
2. Press Ctrl + H (or type edge://history/all in the address bar)
3. At the bottom of the menu on the left click "Clear browsing data"
That's all there is to it, Terry!
![]()
Brenda is looking for fonts she can safely download and install
I am using Windows 10. I would like to add some script fonts - handwriting
fonts to my computer. Can you tell me where I can find some handwriting
fonts I can download without getting malware or causing problems. I would
like to find safe free fonts, but I would be willing to pay for fonts if I
can't find any safe free ones.
Our answer
Hi Brenda.
Here is an article that we wrote we wrote some time ago that features
three very nice fonts sites (mostly free fonts) All were safe to use at the
time we tested them.
Also included in the article is how to preview and install fonts in Windows
10.
I hope this helps you.
![]()
Cathy wants to know about Slimware Utilities
All of a sudden I keep getting popups Slimware Utilities telling me to
update my drivers. I'm not having any computer problems other than this
popup. Can you tell me what Slimware Utilities is? How did I get
it? Should I remove it? Thanks! Cathy
Our answer
Hi Cathy. Slimware Utilities is scamware which is installed as a
standalone program. But most often it comes bundled with other software.
You should definitely uninstall. Driver updater programs are one of the
most useless and harmful applications you can install on your computer.
They can cause major problems requiring repair and possibly even
requiring a reset or reinstallation of Windows. Unnecessarily updating
drivers, especially video drivers, is one of the biggest causes of major
Window problems.
When you uninstall it, it may find it listed as one or more of the
following:
DriverUpdate
Driver Updater
Slimware Utilities
Make sure you uninstall them all. We suggest you use an uninstaller like
Geek
Uninstaller (free) or
HiBit Uninstaller (free) to completely remove Slimware Utilities.
![]()
Bonnie has problems with Task Manager
Hi guys. I have a problem. When I open Task Manager it won't stay open.
It flashes for a second or two and then closes. I have looked all over
for a fix for this but I'm reluctant to edit the registry. Help! Bonnie
Our answer
Hi Bonnie. Before you do anything else, try this:
1. Shut down your computer (power it off)
2. Make sure no lights are on and everything is off
3. Wait 5 minutes.
4. Power on (turn on) your computer.
Wait for Windows to fully load, then try opening Task Manager.
Let me know if that fixes Task Manager.
------
Bonnie wrote back: "THANK YOU! It worked! Thanks
so much for the easy "fix". Bonnie"
![]()
A question from Vic
Hi Guys, it's me again with another dumb question; I am currently
running Windows 10 version 2004 which you tell me will be coming soon so I guess
I am lucky. Anyway, your weekly newsletter mentioned icon renewal in
this version. How do I get to see them on my PC i.e. quick keys, or
search?
Our answer
Hi Vic. As of today, May 1, 2020, the only way you could be running
Windows 10 Version 2004 is if you have signed up for the Windows Insider
program. Insiders do not yet have the final released (public) version of
version 2004. That means that you have a beta version (test version).
Windows 10 version 2004 will not be released until some time this month
(May 2020). You can always check the current version of Windows 10 by
going to this page:
https://www.microsoft.com/en-gb/software-download/windows10
As of today, the current version of Windows 10 is version 1909 (November
2019 Update).
The icons that Microsoft designed for Windows 10 version 2004 are slowly
being added to the final version of Windows 10 version 2004 which is
still about a month away. Also keep in mind icons for programs not
produced by Microsoft will not change... for instance Chrome, Firefox,
Thunderbird, etc.
![]()
Wilma wants to know about PrivacyMate
Just wondering if you can tell me something about this PrivacyMate
thing... is it legit, reliable? I get gobs of junk mail and phone calls
that I would like to stop. Thanks in advance.
Our answer
Hi Wilma. I hope all is well with you.
I don't know if you're talking about junk email or junk snail
mail. So, we'll start with email.
All of these so-called miracle apps are not
necessary. In fact, spam blockers have almost become extinct because so often
they could not tell good emails from spam emails. We use Gmail to filter
spam.
See this Cloudeight article to learn more.
As for phone calls, if you have a cell phone you can block numbers. And
if
don't answer calls unless you know the number you can, over time, reduce
the number of spam calls you get. Don't worry about not answering
numbers you don't recognize - if it's something
important they'll leave a message. If you stop answering junk calls
you'll eventually stop getting so many of them.
There is no snake oil that's going to protect you from the age-old
problems of junk mail and junk calls. And junk snail mail? I just toss
it... not a big problem.
There are literally dozens of snake oil companies - including some
well-known brand names like "Norton Lifelock" promising you privacy. But
there is no privacy anymore. And everyone is going to have to get used
to the brave new world.
If you:
1. Use the internet
2. Drive a car
3. Own a house
4. Have a credit card
5. Have a bank account
6. Have a driver's license
7. Own a cellphone
Then your data is on the Internet and some of it is public. Privacy is
not something we can count on anymore, and no program or service is
going to change that.
My advice? Don't pay someone to protect your privacy, because it's not
going to happen. Just be careful with links in email. If you get
criminals your email password or passwords to banking/credit card sites
and the like, you could lose a lot of money.
I know this is not what you were hoping to hear - everyone wants a pill
to fix whatever ails, but there isn't any magic privacy software you can
buy that's going to protect your privacy.
Being careful with links in email, common sense, and using the software
between your ears, are then only things that can really help protect
your privacy.
I hope this gives you some food for thought.
![]()
A question and a tip from Frederick
A Question and possible tip. I went to the Western Digital website and
it seems good. They have FREE recycling program to safely dispose of
your old internal and external HDDs and SSDs, from any manufacturer.
https://shop.westerndigital.com/campaign/landing/easy-recycle.
They'll even give you $5 OFF on your next purchase from the Western
Digital Store.
I know there is a program to re-format or wipe a HDD safely clean where
information cannot be accessed. You have mentioned it before, but I just
cannot remember it. Help please?
Our answer
Hi Frederick. First, if you're talking about an external hard drive, if
it were me, I'd format the disk using Windows formatting. Right-click on
the drive in File Explorer then click "Format" in the menu that appears.
And yes, it's true, someone with file recovery software may still be
able to glean some information from that drive, but it's highly unlikely
someone your sending your drive to for recycling is going to take the
time to scour your drive for personal information, considering the odds
of recovering any personal data isn't all that great... unless their
using forensics-grade recovery software and assuming that would be a
stretch.
If you're really concerned about someone recovering some personal data
from that drive you can use a program like KillDisk (Free version)
available at
http://killdisk.com/killdisk-freeware.htm.
If you're talking about your internal hard drive (main hard drive),
since you're using Windows 10, there's a very easy way to remove
everything from your hard drive using nothing but Windows 10.
You can find the instructions here.
Using Windows 10 as described in our article, you can wipe your hard
drive completely and reinstall Windows 10. While you may not care if
Windows 10 is reinstalled if your giving recycling the drive, it won't
matter, but what does matter is that using that method there no personal
data can be recovered from that drive.
It's a lot better and easier than using a disk erasing program that
requires you to create a separate boot disk and then format the drive
using the Linux or DOS boot disk.
Thanks for the tip, too. When we answer your question in the newsletter,
your tip will be there too!
------
Frederick wrote back: "Thank you so much. I have been with you guys
for many years. You do great work!"
![]()
Mary wants to know if a program can make Windows XP safe
My apologies for my carelessness. I am a long time fan of your site and
have the icon on desktop as a startup page. What I was referring to was
an article that I was reading off the RSS feed and linked through a
Yahoo News page. Unfortunately I clean out trash when I close my XP at
night. It was an article saying that there was now a site that one could
access and download an MS update that would protect your computer, no
matter the version, from virus attacks. It sounded too good to be true.
And now I can't even find the article. Sorry for my incompetence
But I love your site and will continue reading your sound advice to
others. Sincerely, Mary
Our answer
Hi Mary. Thanks for your kind words. You should not blame yourself, the
news items change continually as the reflect the news as it happens. We
don't control what appears in the newsfeed on are start page they are automatically fed
into the page from the news source.
That being said, there are no programs or MS Updates that will
make a Windows XP computer safe. Windows XP has not received critical
updates or security patches from Microsoft for a very long time. Without
even seeing the article to which you refer, I can tell you with
certainty that is no magical program or "MS Update" that will make a
Windows XP computer safe to use. The only way you can safely use a
Windows XP computer is by disconnecting it from the Internet.
![]()

Attention Cloudeight SeniorPass Holders! Announcing our new SeniorPass Telephone Hotline Service
Don't have a Cloudeight SeniorPass? It's a great deal. Learn more here.
During this global crisis, we are offering a special telephone hotline service to all SeniorPass holders. There are reports of many COVID19 scams targeting seniors. If you are approached by a scammer or encounter something suspicious, you can use our hotline to discuss your situation with us. We check into it for you and do all we can to help you.If currently have a SeniorPass, all you need to do is contact us. Send us your telephone number and a brief message describing your problem and we'll call you back during normal business hours.
If you don't yet have a Cloudeight SeniorPass and you'd like to know more about our SeniorPass, please see this page.
Please note: Currently, our telephone hotline service is only available to SeniorPass holders in the U.S.A.due to international call restrictions.
Tools You Can Use to Uninstall Popular Antivirus/Security
Software
Windows 7, Windows 8.1, Windows 10 (all versions)
Most security software companies will tell you it’s as easy as using
Control Panel/Programs/Uninstall a program to remove their
antivirus/security software. That’s what they’d like you to believe, but
the truth is that if you uninstall most security software using Control
Panel, you’ll end up with a lot of leftovers and even running services
you don’t need or want. These "leftovers' can bog down you system and
even cause you problems when you want to install a different security
program.
We’ve compiled a list of programs offered by the security software
companies that will help you completely remove antivirus/security
software from your computer.
Avast Removal
Tool
Note: Avast claims you must run this in safe mode, but we’ve
successfully uninstall Avast from many computers just running it in
normal Windows.
AVG
Removal Tool
Avira Removal Tool
BitDefender
Kaspersky Removal Tool
McAfee
Removal Tool
Removes most McAfee security products
Norton Remove and Reinstall Tool
Removes most Norton Security products.
Note: This is called the Norton Remove and Reinstall Tool
and that’s just what it will do if you’re not careful: It will remove
Norton and reinstall Norton unless you do this:
1. Double-click the NRnR icon. Read the license agreement, and click
Agree.
2. Click Advanced Options.
3. Click Remove Only.
4. Click Remove.
5. Click Restart Now.
Panda
Removal Tool
Trend Micro Removal Tool
Vipre Removal Tool
Would you like to switch to Emsisoft?
We use and recommend Emsisoft. When you purchase an
Emsisoft license from this page, we’ll remove your old security
software and set up Emsisoft correctly – all for the price of the
Emsisoft license.
![]()
Guest Mode and Incognito Mode in Chrome
Windows 8.1 and Windows 10 / Google Chrome installed
Both Guest mode and Incognito mode are temporary browsing modes you can use in Google Chrome. Guest mode was originally found only in Chrome in the Chrome OS (operating system), but Guest mode is now available in Chrome for Windows. Guest Mode and incognito mode are similar, but there are basic differences between them.
Guest mode
Guest mode provides a completely blank profile for someone who is using Chrome temporarily. Like Incognito mode, it doesn’t save any record of the browsing history and doesn’t use extensions. However, in Guest mode, the user can’t change any Chrome settings aside from the search engine. A guest user also can’t see any of the browsing history of the main user. When you exit Guest mode, your browsing activity is deleted from the computer.
According to Google:
“Guest mode is ideal for:
Letting others borrow your computer, or borrowing someone else’s computer.
Using a public computer, like one at a library or cafe.”
You can open Guest mode in Chrome by clicking on the user’s name or icon on the right side of the toolbar and then clicking on “Open Guest window”.

Incognito mode

All browsers have a form of incognito mode. In Edge (and IE) it's called "In-Private browsing", in Firefox it's "Private browsing" Chrome calls its private browsing mode "incognito". You can open a new incognito window in Chrome by clicking on the 3-vertical dots icon (settings) and clicking “New incognito window” or using the shortcut CTRL+SHIFT+N. You can also right-click on your Chrome icon on your desktop or taskbar and choose “New incognito window”.
When using incognito mode you have full access to Chrome bookmarks, existing history, passwords, Autofill data, and other Chrome settings, but you won’t leave any browsing history or cookies on your computer during the incognito session.
Many people mistakenly think that incognito mode makes them invisible on the web and prevents them from being tracked or identified, but it does not. Your ISP, Web advertisers and the Web sites you visit can still see and log (record) your IP address and your browsing activity.
While it does not make you invisible on the Web, it does allow you to browse without saving any history or cookies on your computer. And though it does not make you invisible on the web, incognito mode has plenty of uses.
For instance, if you have more that one Gmail account, you can use incognito mode to log into your other Gmail account without signing out of (or joining) your other Gmail account.
If you have more than one Facebook account for example, one for your business and one for personal use, with incognito mode you can sign into the second Facebook account without signing out of the other Facebook account.
You can check for price discrimination using incognito mode. Some websites show different prices to different people based on their browsing and search history. Examples of this kind of price discrimination include airline ticket websites and Amazon. Amazon and several airline/travel sites have been found guilty of price discrimination.
Price discrimination is accomplished by the site saving a cookie in the user’s browser that may have a higher price for an airline ticket or an Amazon item. This price is based on the user’s history of pages they’ve visited while they previously shopped for the best price on an item.
Using incognito mode lets you check airfares or price items without any discrimination, because in incognito mode there aren’t any cookies, history, and therefore no prior bias.
Incognito mode lets you compare prices between the ones you’ve already gotten and the prices a person searching for an item for the first time would see. In other words, you’ll find out if there is a lower price than the one you’ve been quoted. By using incognito mode, you can check for the lowest price with no discrimination based on your browsing and search history.
Guest mode is great if you’re using someone else’s computer, you’re using a public computer or you want to let someone else use your computer. But If you want to browse privately on your own computer, use Incognito mode. You’ll see your info and settings without saving any cookies or browsing history.
Always remember that neither incognito mode nor Guest mode makes you invisible on the web. Your ISP, the Websites you visit, advertisers on the web and/or your employer can still see all of your browsing activity.
![]()
Let’s Protect Your Webcam
Windows 8.1 and Windows 10 (all versions)
With just about all of us under some sort of “stay-at-home” orders, many of us are using web conferencing software and webcams to stay in touch with our loved ones and friends. And let’s not forget about the current rise of “telehealth” for which webcams come in handy. While not nearly as good as a real get together, a virtual get together is a great way for us to stay connected with our family members, friends, and health care providers.
Whether you use Zoom, Skype, Microsoft Teams, or other conferencing software, your webcam has probably never been as busy as it is right now during this pandemic.
And almost all of us have a camera built into our computer, laptop, smartphone, or tablet. And whether we use it for work, school, connecting with our doctors, family members, or friends, those cameras can leave us vulnerable to an online attack known as camfecting.
Camfecting is a term used when hackers take control of your webcam remotely. They do this without attracting attention by disabling the “on” light which usually lets us know the camera is active. Camfecting makes unprotected cameras vulnerable since the “on” light will remain off if a hacker has control of it. The hacker can “see” with your webcam. Read more about camfecting here.
There are search engines (Shodan, for example) that can find any unprotected device connected to the Internet, including webcams. So it’s not hard for hackers to locate any unprotected devices connected to the Internet of Things
But remember that an attacker cannot hack your webcam if your device is turned off. However, they can access your device’s camera if it’s in sleep mode or if your screen is dimmed but the device is still active So many of us (I plead guilty) don’t turn our devices off very often.
Using a webcam password, other than its default password, is one way to protect your webcam from being hacked. But most of us aren’t going to do that.
So here’s a simple, easy, low-tech way to prevent anyone from accessing your webcam when you’re not using it.
Our low-tech but very effective tip on how to keep your webcam safe…
Put a piece of black (or other opaque tapes) over your camera lens when you’re not using it. It’s a good idea to cut a small square of paper to place between the lens and the tape to keep the sticky adhesive from the tape from getting on the camera lens. It’s rumored that the director of the FBI uses this low-tech method because it works.
And yes, you can even use a Band-Aid (bandage) to cover your camera lens.
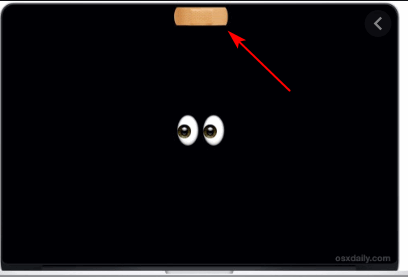
It may be low tech, but it will prevent hackers from accessing your webcam.
Slow to Start? Here’s a Time-Saving Tip For You
Windows 10 (all supported versions)
One of the biggest complaints we hear about Windows 10 – besides the continuing litany of botched updates – is how long it takes to start up. Well, it’s true, you can disable some startups and decrease Windows 10’s startup times, but still, most Windows 10 computers will take between 2 minutes and 5 minutes to start up. And something else to remember is that boot times vary depending on the computer. Systems with more RAM (memory) and SSDs (Solid State Drives) boot faster than those with less RAM and HDDs (Standard Hard Drives).
When we say 2 minutes to 5 minutes to start up, we don’t mean 2 to 5 minutes until you can see Windows on your screen — we mean 2 to 5 minutes from the time you start Windows 10 until the time you can actually use it. In other words from the time you start Windows 10 until the time it is fully loaded.
And a bit about Windows 10 Sleep mode: If you’re one of the many people who have used Widnows10 sleep mode only to find that Windows 10 takes forever to wake up from sleep — this tip is for you too.
Now we are going to share a tip that both of us have used for many years. Both of us love to get up in the morning and have our Windows 10 PCs ready to use. We don’t want to waste 2, 3, 4, or more minutes to use our computers. We want to right to work!
So, despite the controversy that this tip will probably evoke, we’re going to share our homemade time-saving tip with you. Please remember: Every computer is different, just like everyone who uses a computer is different. If you’d like to have your computer instantly ready to use every time you want to use it, this tip may be just what you’re looking for.
Here’s our time-saving tip
Here is how we set up our Power Options on our Windows 10 computers.
Press and hold down the Windows key & tap the x key (or right-click the Start button) and select “Power Options” from the menu which appears.
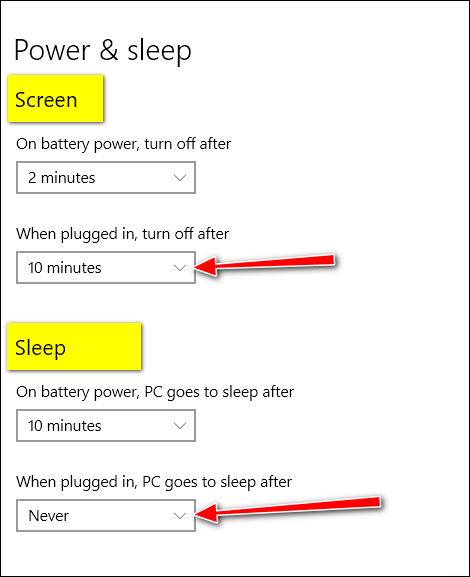
If you don’t have a laptop, and you want to try these just use the settings we have selected for “When plugged in…”.
Under “Screen”
Set it to turn off after 10 minutes
This means that after 10 minutes of inactivity (no keyboard, mouse, or touchpad activity) your screen will turn off.
Under “Sleep”
“PC goes to sleep after”.. should be set to “Never”.
You may be wondering about how much extra electricity you’ll use if you don’t turn your computer off every night or put it to sleep. It depends on your PC. Newer desktops, all-in-ones, and desktops are a lot more energy efficient than old ones.
Desktops and all-in-ones use more electricity than laptops. It’s impossible to say how much more electricity your computer will use if you leave it turned on using the settings as suggested here. Our best guess is about 10-20 watts for a laptop (a nightlight or two), and 30- 60 watts for all-in-ones and desktops.
Using these settings guarantees instant access to your computer the minute you need it. To wake the screen just touch a key, move your mouse or tap the touchpad if you’re using a laptop.
Oh, and one more thing…
Leaving your computer turned on with these settings does not -at
least not in our 22+ years of experience — shorten the life of your
computer. The computer on which this tip was written is an 8-year-old
Dell laptop – and it’s still going strong. It originally came with
Windows 7 and I upgraded it to Windows 10 a couple of years ago.
![]()
Want more tips, tricks, and information?
We have thousands of Windows tips, tricks and more on our InfoAve web site.
Subscribe to our free InfoAve Daily newsletter.![]()

It's springtime and it's time to get your computer ready for summer. With our new Spring Cleanup service, we'll make that EASY for you.
We'll check your PC, clean it up, optimize it and get it ready for summer...
Here's what we'll do for you:
- We'll connect to your computer and do a deep scan for malware
- We'll check your computer for suspicious programs
- We'll check your browser for problematic extensions/add-ons
- We'll optimize your startups.
- We will check your hard drive
- If you choose, we'll remove your current security software and install Emsisoft and give you a FREE 3-month license
*Our Spring Cleanup Service does not
include repairs. If repairs are needed, we'll give you a special price
on our Cloudeight Direct Computer Care repair service.
![]()

Enhance Blurry Images and More With Smart Upscaler
Have you had pictures that were out-of-focus, grainy, or generally just poor quality? Most of us have.
We found an online program that can help make blurry, grainy, poor quality images clearer. The online app is called Smart Upscaler. It’s a free, easy, and quick way to enhance and clarify images. Plus, it can automatically enlarge images up to 4 times.
Smart Upscaler sharpens, enhances, clarifies, and – if you wish – enlarges images quickly and easily using automatic intelligence or – ya know – that dreaded acronym AI.
There is no account needed, no sign-up needed, and no money needed I tells ya! Just upload your image by dragging it onto the page or browse to upload it. You can use any image in JPG or PNG format up to 5 MB. Images you upload are enlarged or “Upscaled” 2x by default. Images you upload can be enlarged 4x up to 3000 x 3000 pixels.
After you upload an image, Smart Upscaler gets to work enhancing your image using AI. When it is finished, it displays the original image and the enhanced image side by side. The difference is sometimes subtle but noticeable with most images.
I found an old photograph of my ancestors – all have by now left their earthly coils. It’s the only picture of these folks I have. It is a black & white, out-of-focus (probably taken with a Kodak Brownie!) photograph. And while the difference between the before and after images is slight, you can see the difference. In the before picture you can barely discern the faces of these fine folks, in the after picture you can. Here, take a look.
Click on the image to see the full-size photograph.
If you have blurry, out-of-focus, blah image, why not see what Smart Upscaler can do for your pictures. Once Smart Upscaler has enhanced your photos you can download the enhanced to your computer. All the images you upload are stored securely and are deleted from the Smart Upscaler server as soon as you complete your session.
So… if you’ve got blurry, out-of-focus, or grainy images – or you want to enlarge –“Upscale” — images without losing quality, then our site pick “Smart Upscaler” might be just what you are looking for. Why now give it a try? All you have to lose are blurry, fuzzy, pictures!
Visit Smart Upscaler and see what it can do for you.
![]()

VERSION 8.43 NOW AVAILABLE!
If you purchased or renewed Reg Organizer through Cloudeight within the last 12 months, you're entitled to a free version upgrade to Reg Organizer 8.43.
Save $14 on Reg Organizer right now!
Reg Organizer - A Swiss Army Knife of Windows Tools - Works Great on Windows 10!
![]()

15 Years Later and Your Computer Still Won’t Bite
The world has changed more in the last 2 months than it has our
lifetimes. No one saw the COVID-19 pandemic coming – but many people
predicted it. Our computers have because more important to us than
ever as we stay in our homes during the pandemic.
But some things have hardly changed at all. We wrote our first “Your
Computer Won’t Bite” e-book back in 2005. Windows XP was just a few
years old and some folks were still hanging on to Windows 98 and
Windows ME.
Nearly fifteen years ago we told you that your computer won’t bite,
and though technology and the world have changed a lot in those
fifteen years, the basic theme of our old, outdated e-book is still
true even though almost 15 years have passed. Sometimes the adage
that the more things change, the more they stay the same is true.
The following excerpt originally appeared in the introduction to our
2005 “Your Computer Won’t Bite” e-book. Let’s take a look back
nearly 15 years to what we wrote in July 2005,,,
Read
the rest of this essay here.![]()
Attention Cloudeight SeniorPass Holders! Announcing our new SeniorPass Telephone Hotline Service
Don't have a Cloudeight SeniorPass? It's a great deal. Learn more here.
During this global crisis, we are offering a special telephone hotline service to all SeniorPass holders. There are reports of many COVID19 scams targeting seniors. If you are approached by a scammer or encounter something suspicious, you can use our hotline to discuss your situation with us. We check into it for you and do all we can to help you.If currently have a SeniorPass, all you need to do is contact us. Send us your telephone number and a brief message describing your problem and we'll call you back during normal business hours.
If you don't yet have a Cloudeight SeniorPass and you'd like to know more about our SeniorPass, please see this page.
Please note: Currently, our telephone hotline service is only available to SeniorPass holders in the U.S.A.due to international call restrictions.
![]()
Pipes and Tildes
We both used to smoke cigarettes. But we gave them up for cigars.
Then we switched to pipes. Finally, we gave those up for tildes. But
tildes are take too long to light. Actually most of that is sort of
not true.
Anyway... Do you know what tildes and pipes are? We'll show you:
~ ~ ~ ~ ~ ~
| | | | | | | |
The top row contains six tildes (til'des), the bottom row contains
eight pipes.
~ is called a tilde (til'de). We don't know why, it just is. You
used to see it more when short file names were common on Windows. A
tilde is also (according to
www.dictionary.com ), is "A diacritical mark ( ~ ) placed over
the letter n in Spanish to indicate the palatal nasal sound as
in cañon, or over a vowel in Portuguese to indicate nasalization, as
in lã, pão."
This thing | is called a pipe. It is used in science, mathematics,
and, of course, in computers and computer programming. The pipe or
vertical line | can be a separator like TC|EB or it can be part of a
DOS or Unix command. You can type a pipe by holding down the shift
key and pressing the \ (backslash key).
And now you know what tildes and pipes are. Hey, EB, where's my
pipe? What do you mean No Smoking?
![]()

We need your help! Please help us keep on helping you!
When you support us with a small gift, you help us continue our mission to keep you informed, separate the truth from the hyperbole, and help you stay safer online. Plus, our computer tips make your computer easier to use.
Did you know that we provide support to thousands of people? Every week we help dozens of people via email at no charge. The questions and answers you see in our newsletters are from the email answers and help we provide to everyone free of charge.
Thanks to your gifts, we do a lot more than provide this free newsletter. We help you recognize online threats, fight for your online privacy, provide you with the knowledge you need to navigate the Web safely, provide you with suggestions for safe, free software and websites, and help you get more out of your PC.
Please Help us keep up the good fight with a small gift.
Interested in making an automatic monthly gift? Visit this page. Help us keep helping you... and helping you stay safe on the Web.
![]()
Sales of the following products and services help support our newsletters, websites, and free computer help services we provide.
Cloudeight Direct Computer Care: Single Keys, SeniorPass or Season Tickets - always a great deal. Cloudeight Direct Computer Care is like having PC insurance. Get more information here.
Emsisoft Anti-Malware: Emsisoft is the only Cloudeight endorsed and recommend Windows security program. It provides users with a complete antivirus, antimalware, anti-ransomware, anti-PUPs solution. We offer single Emsisoft licenses and multi-computer licenses at discount prices. Also, we offer our exclusive Emsisoft with Cloudeight installation & setup. Get more information here.
Thunderbird Email Setup: Thunderbird is a great email program that you can use with your Gmail and Outlook.com (Hotmail) webmail accounts as well as with your Internet provider's email. We'll set it up correctly you. Our set up includes configuring up to 3 email accounts and setting up Thunderbird to use stationery (if desired). Our Thunderbird Email Setup Service is always a great deal. For more information visit this page.
Reg Organizer 8.43: Reg Organizer is the Swiss Army Knife of Windows tools. It's far more than just a registry optimizer and cleaner... it's a Windows all-in-one toolkit. Reg Organizer helps you keep your computer in tip-top shape and helps you solve annoying Windows problems. Reg Organizer works great with Windows 10! Get more information about Reg Organizer (and get our special discount prices) here.![]()



These products and services are recommended and endorsed by Cloudeight:
Also... don't forget: 
We'd love to hear from you!
If you have comments, questions, a tip, trick, a freeware pick, or just want to tell us off for something, let us know.
If you need to change your newsletter subscription address, please see "Manage your subscription" at the very bottom of your newsletter.
We received hundreds of questions for possible use in IA news. Please keep in mind we cannot answer all general computer questions. We try to personally answer as many as we can. We can only use a few to in each week's newsletter, so keep this in mind. If you have a support question about a service or product we sell, please contact us here.
Subscribe to our Daily Newsletter!
Get computer tips & tricks every night. Our daily newsletter features a computer tip/trick or two every day. We send it out every night around 9 PM Eastern Time (USA). It's short and sweet, easy-to-read, and FREE.
Subscribe to our Cloudeight InfoAve Daily Newsletter!
Print our Cloudeight Direct Computer Care Flyer!
Print our Cloudeight Direct Computer Care Flyer and spread the word about our Cloudeight Direct Computer Care repair services. Get our ready-to-print flyer here.
We hope you have enjoyed this issue of Cloudeight InfoAve
Weekly. Thanks so much for your support and for being an InfoAve Weekly subscriber.
With hope and prayers, may you and your loved ones stay safe and well.
Your friends at Cloudeight,
Darcy and TC
Cloudeight InfoAve Weekly - Issue #864
Volume 17 Number 28
May 1, 2020
Not a subscriber? Subscribe to our FREE Cloudeight InfoAve
Weekly Newsletter here.
Subscribe to our Cloudeight InfoAve Daily Newsletter!
Share Us on Facebook!
We'd love for you to share us with your family and friends on Facebook. Help us by sharing us on Facebook! 

"Cloudeight InfoAve
Weekly" newsletter is published by:
Cloudeight Internet LLC
PO Box 73
Middleville, Michigan USA 49333-0073
Read our disclaimer about the tips, tricks, answers, site picks and freeware picks featured in this newsletter.
Copyright ©2020 by Cloudeight Internet

