Emsisoft Protects You From the Current WCry Ransomware Pandemic
The WCry or WannaCry ransomware is wreaking havoc on tens of thousands of computers around the world including the giant Spanish telecom Telefonica and the National Health Service in the United Kingdom.
WCry is also known as WNCry, WannaCry, WanaCrypt0r or Wana Decrypt0r. It was found in early February 2017. It spread to a some computers in March, but now, this week has spread around the globe.
WCry will search for and encrypt all user files with the following extensions on all available drives: connected external drives, internal hard drives, connected USB flash drives, and network drives.
.der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .ott, .sxw, .stw, .uot, .3ds, .max, .3dm, .ods, .ots, .sxc, .stc, .dif, .slk, .wb2, .odp, .otp, .sxd, .std, .uop, .odg, .otg, .sxm, .mml, .lay, .lay6, .asc, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .db, .dbf, .odb, .frm, .myd, .myi, .ibd, .mdf, .ldf, .sln, .suo, .cs, .cpp, .pas, .asm, .js, .cmd, .bat, .ps1, .vbs, .vb, .pl, .dip, .dch, .sch, .brd, .jsp, .php, .asp, .rb, .java, .jar, .class, .sh, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .3gp, .mkv, .3g2, .flv, .wma, .mid, .m3u, .m4u, .djvu, .svg, .ai, .psd, .nef, .tiff, .tif, .cgm, .raw, .gif, .png, .bmp, .jpg, .jpeg, .vcd, .iso, .backup, .zip, .rar, .7z, .gz, .tgz, .tar, .bak, .tbk, .bz2, .PAQ, .ARC, .aes, .gpg, .vmx, .vmdk, .vdi, .sldm, .sldx, .sti, .sxi, .602, .hwp, .snt, .onetoc2, .dwg, .pdf, .wk1, .wks, .123, .rtf, .csv, .txt, .vsdx, .vsd, .edb, .eml, .msg, .ost, .pst, .potm, .potx, .ppam, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xlsb, .xlsm, .xlsx, .xls, .dotx, .dotm, .dot, .docm, .docb, .docx, .doc, .c, .h
Once the files are encrypted, the user will have to pay $300 (or more) to get access to their files. As of now, there is no known free decryptor available for WCry. Infected computer will display this warning:
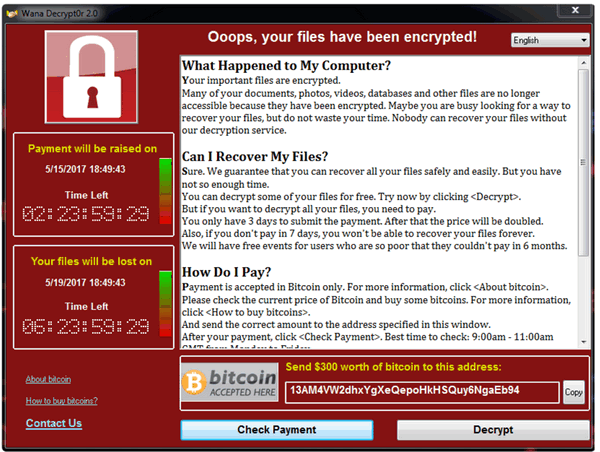
WCry will charge those infected $300 in Bitcoin to for the decryption key to decrypt their files if the ransom of $300 is not paid in 3 days, it will be doubled. If it is not paid in 7 days, compromised users will not be able to recover their files.
We have previously warned users of Windows XP that after Microsoft ended support there would be no more security patches or updates from Microsoft. We also warned that continuing to use Windows XP would eventually expose users to these kinds of attacks and there would be no defense against them. Outdated/unpatched versions of Windows allowed WCry to spread to tens of thousands of computers and cause hospitals to turn patients away and large companies to shut off their computer systems for the weekend. Since legitimate antivirus developers do not make antivirus programs for outdated, unpatched operating systems, there is no way to protect those systems from events like WCry ransomware. Because so many business are still using unsupported versions – WCry spread to tens of thousands of computers in over 100 countries, some countries were forced to shut down their computers for the weekend. It is so bad that Microsoft, in an unprecedented move, issued emergency patches for 3 unsupported versions of Windows: Windows XP, Windows 8, and Microsoft Server 2003 – Windows 10 was never vulnerable to this ransomware:
A day after a ransomware worm infected 75,000 machines in 100 countries, Microsoft is taking the highly unusual step of issuing patches that immunize Windows XP, 8, and Server 2003. These are operating systems the company stopped supporting as many as three years ago…
The moves came after attackers on Friday used a recently leaked attack tool developed by the National Security Agency to virally spread ransomware known as “WCry” or “WannaCrypt.” Within hours, computer systems around the world were crippled, prompting hospitals to turn away patients while telecoms, banks, and companies such as FedEx were forced to turn off computers for the weekend.
The chaos surprised many security watchers because Microsoft issued an update in March that patched the underlying vulnerability in Windows 7 and most other supported versions of Windows. (Windows 10 was never vulnerable.)…
Our advice: Keep your files backed up and remember Windows updates are important. Always keep your computer updated and do not turn off Windows Updates, Microsoft patched the vulnerability that WCry uses to encrypt files on Windows 7 computers over two months ago, Windows 10 was never at risk. And use an antivirus / anti-malware that will actually protect you from a wide array of threats. We recommend Emsisoft.
We’ve been recommending Emsisoft for over 3 years. We have found it to be best protection and, as usual, Emsisoft was right on top of the WCry epidemic. Those of you who are using Emsisoft are protected from this ransomware by Emsisoft’s Behavior Blocker. It will show you this warning if Emsisoft detects WCry trying to install on your computer.
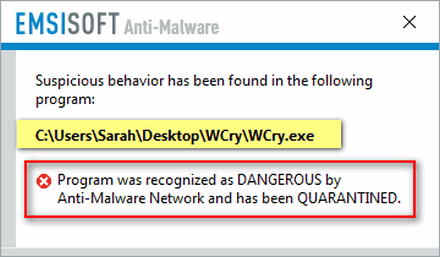
All Windows 7, Windows 8.1 and Windows 10 users who have Emsisoft installed have this extra layer of protection.
We recommend that you keep good backups, refrain from clicking links in strange or spam emails and be wary while on the Internet. Make sure Windows Update is on and working, and if you don’t have Emsisoft, you try it free for 30 days. If you want to buy a one-year license, we’ll even install it for you free.
Want to know more about WCry ransomware?
According to information we have received from Emsisoft…
WCry is primarily spreading via the leaked NSA exploits that the Shadow Brokers group released recently. More specifically, French researcher Kaffine was the first to suspect that WCry was being spread via the ETERNALBLUE exploit…
ETERNALBLUE exploits a vulnerability in the Microsoft SMBv1 protocol, allowing an attacker to take control over systems which…
- have the SMBv1 protocol enabled
- are accessible from the internet and
- have not been patched by the MS17-010 fix released by Microsoft back in March 2017
In addition, it appears that the malware authors are also taking advantage of DOUBLESPEAR, a backdoor that is usually installed via the ETERNALBLUE exploit and persisting on the system. So if your system was compromised by ETERNALBLUE previously, chances are your system is still vulnerable, even if the initial SMBv1 vulnerability was patched…
WCry key generation and encryption
… WCry ransomware uses a combination of RSA and AES-128-CBC to encrypt the victim’s data. To facilitate this process, is uses the Windows CryptoAPI for RSA, but a custom implementation for the AES encryption.
Interestingly, the encryption routine is stored in a separate component within the t.wnry file, and is itself encrypted using the same method used by the ransomware to encrypt user files. This was likely done to make the malware analysis more difficult. The module is loaded into memory using a custom loader and executed from there, without ever being written to the victim’s disk unencrypted.
When WCry arrives on a system, it will first import a hardcoded private RSA key that is used to decrypt the file encryption component stored within “t.wnry”. Once done, the ransomware will generate a new private RSA key. That RSA key is then submitted to the malware’s command and control server and a copy of the generated public key is stored on the system…
BE SAFE!
Make sure you are up-to-date with Windows Updates. Keep good backups, And use Emsisoft Anti-Malware – it’s been our number one recommended antivirus/antimalware for over 3 years. Now you can see why we trust the software and the great people behind it.
Get more information about Emsisoft here. Or buy a one-year Emsisoft license and we’ll install it and set it up for you for free!


Dear Cloudeight : Many thanks for your reassuring info about this malware attack. I was waiting for your comments and you didn’t delay. Since years I trust your advice to keep my computer, an important part of my senior single life, running well and safe. Be well and all the best !
Helga
Thank you for this very informative piece.
I can always count on you to clearly explain these things and keep us up to date.
It is good to know that my Emsisoft program protects against this terrible problem.
Happy Mother’s Day (if applicable) and thank you for the valuable service you provide to home computer users. I would hate to have to get along without your team.