Bill is tricked into downloading a malware scam posing as an anti-malware program
Yesterday I had an interesting experience. I received a message from Facebook supposedly, advising me that there was a problem with my user ID and password and that they were going to change it for me. They sent the new ones (user ID & password) as an attachment which opened to Excel I believe it was. I should have known that the user is the only one who can/should change that. Well, there was a box which was advertising a new program, ‘CleanThis’. I couldn’t get rid of it so I rebooted the computer. In doing so, the ‘program’ installed. Then a box appeared with two choices listed–normal start or safe start. Of course the normal start was dimmed so in clicking safe start, this ‘thing’ began scanning the computer. After it finished, it listed a bunch of items that ‘needed’ to be removed/repaired with this Heuristic module, which it needed and I didn’t have. I checked the order thing and they wanted an arm and a leg for the ‘program’ and I suppose if they got a person’s credit card or such, that would be run to the max. Anyway, this program was not listed in Revo uninstaller nor the Control Panel so I couldn’t attempt a removal that way. I did find the program nestled in C:\user/bill\app data\roaming\install.
A bit later when I was running Malwarebytes, I was unable to delete the program. I figured it was password protected or something? I was unable to get rid of the interface of the program. It appeared to be a Microsoft program. One of the first boxes that appeared advised me of a virus or something and then I had two choices–I don’t recall now exactly what they were, but I clicked the one to find the solution to the problem or to clean it up. It was labeled Microsoft Security Essentials. I figured that should be all right then, but thinking back on it, I don’t have MSE installed in my computer.
To make a long story short, I run Malwarebytes and got rid of a couple viruses and a Trojan. Then I run SuperAntispyware and Avast Free and was able to completely rid my computer of these ‘aliens’. Whatever it was blocked my access to my browser and I was also unable to access my System Restore. Nasty.
In checking the program before it was eliminated, the name of the ‘company’ was listed as Cyber Wolf inc. (small i) V7.13.0.192. At first I also figured Microsoft was trying a hard sell, but even they wouldn’t be so blatant about it–would they? 🙂
Again I wish to thank you folks so much for enticing me to install Malwarebytes and SuperAntispyware. Between them and Avast, I feel my bacon was saved. I took several snapshots of the desktop with these various items displayed if I may send them to you too. Thanks again. Bill
Our Answer
Bill, I think this is the first time in the history of InfoAve Premium that a question has been almost longer than our answer! This is history. Not really. Our answer makes your question look short!
Your question and story provide everyone a good lesson. No legitimate company is going to email you an attachment and tell you to use it to reset your password. It is not ever going to happen. If a company has reason to believe your account was breeched, they may email you and suggest you login to your account and change your password, but they are not going to give you links to click and certainly they’re not going to send you attachments to click. We all make mistakes; you made a mistake by clicking on an attachment in an email you thought was from Facebook. But remember this…no big company – or even small company – which is legitimate is going to send you a “password reset” file to click on.
But we can’t cry over spilled milk. The program you were duped into downloading is one of the thousands of rogue security programs which not only infect your computer but make you pay them before you can “clean” (read “use”) your computer. CleanThis is one of the thousands of rogues out there. They are distributed via email attachments, malicious web sites, and malicious advertisements. They have different M.O.’s but they all work in the same way.
First they offer to scan (or just start scanning your computer without any warning). Actually what you are seeing is not really a scan of your system but an animated gif. Then there is a warning that the “scan” found dozens of infected files on the target computer – all of which are “dangerous” and which need to be removed. After the fake scan the program will offer to clean all these infected files — for a price. If you don’t pay the price, the program covers your desktop and you can’t get it off your desktop – the window remains on top of all other windows. You can’t use Alt F4 to close the window – and you can’t get to Task Manager to end the process. And unless you jump through hoops like you did – or use a simple trick we showed everyone in this newsletter a while back – the program will continue to start with Windows and remain on top of your desktop and all other windows – making your computer useless. CleanThis is not nearly as bad as some. Some of these rogues will fill your entire screen and you can’t open other programs or use your computer.
Unfortunately, these rogues generate tens of millions of dollars for cybercriminals who extract a ransom from computer users. Some people will pay $39 or $49 for these rogues just to get them off their desktop.
(Bill was kind enough to send us this screen shot – along with others.)
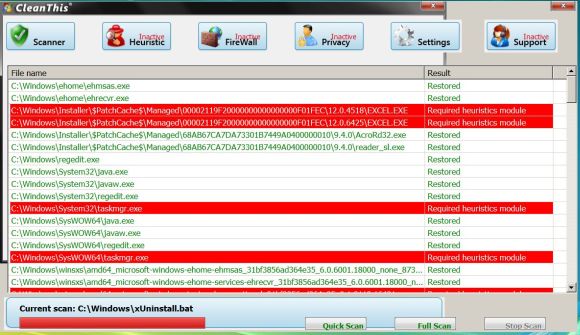
This same thing has happened to many people. It almost happened to EB the other day. It’s happened to me. I’ve even intentionally download one of these rogues to learn ways to get out of it with no damage, no leftovers, and with the least amount of work. Even those who are experienced with computers make mistakes. We all get tired; we all sometimes are guilty of clicking without thinking; we all get in a hurry and get careless. The minute you think it can’t happen to you is the minute it happens to you.
Bill, we’re glad you were able to get rid of the rogue – and you did well. But there is an easier, more certain, more complete solution to this kind of attack. Once you understand that the program is communicating with a Web server while its running and that it is starting up with Windows, you’ll see why our solution always works.
We’ve featured this as a tip in our newsletter previously. But this tip is also the answer to these kinds of attacks. When you use this tip you cut off the program from its connection to the Internet and you cut off its ability to start with Windows.
And everyone should commit this tip to memory – or print it out and keep it somewhere – because there’s a better than average chance that at least half of you reading this will be attacked by a rogue this year. There are thousands of them on the Web – and there are dozens of new ones being introduced every day – all with names like Windows AntiVirus 2011, CleanThis, Windows Security 2011, and so forth – all names indicative of a security program but which are really malicious programs which will try to subvert your computer and make you pay to clean phantom infections which don’t really exist.
Here are some examples of rogue attacks. They look genuine, don’t they?
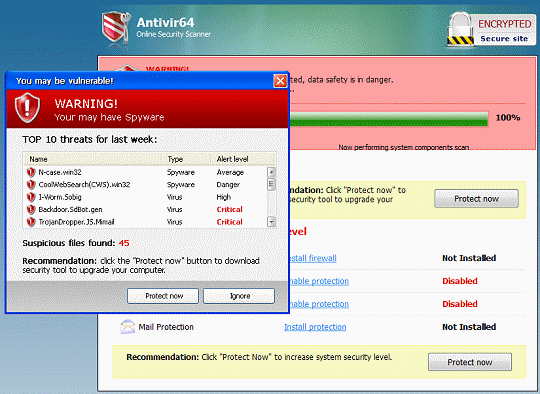
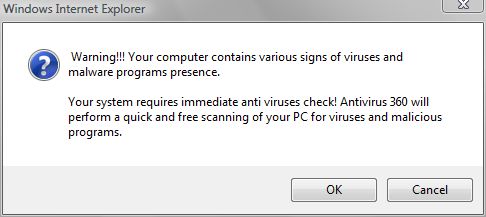
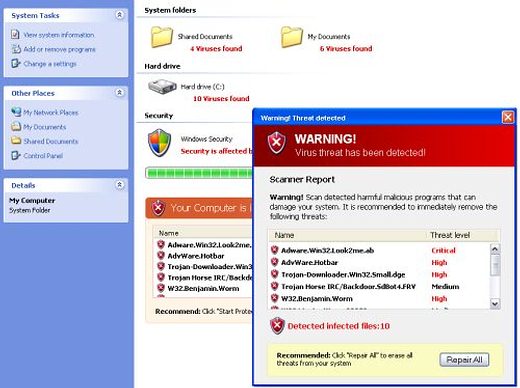
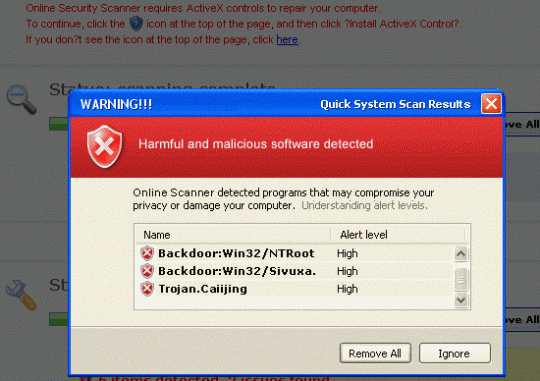
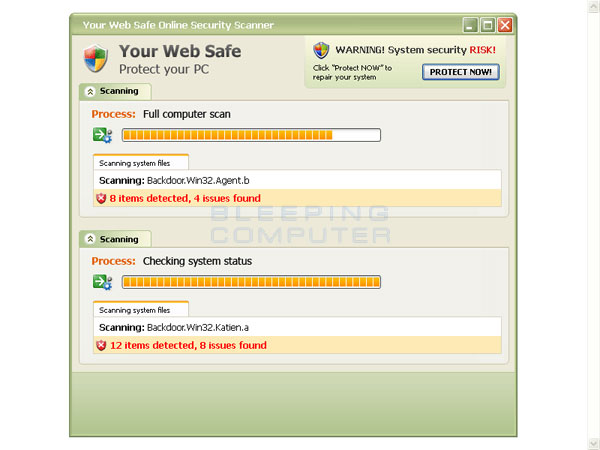
All of the above are examples of fake security software “scanning” or asking to scan your system. The scans are fake; the results are fake. But the money people are duped out of by these rogue security programs is real.
We want everyone to recognize these kinds of malicious attacks. And to realize that even with the best antispyware, antimalware and antivirus installed – you might still see one of these attacks. It’s a fact of Internet life. And you need to know the fastest and best way to get rid of a rogue should you find yourself in this situation.
There is a one best way to take care of this kind of attack – and you don’t need to download more software. And here it is. (If you’re printing this tip to save, start printing from here.)
RSTRUI – Six letters you shouldn’t ever forget
Here’s a tip you won’t remember until you need it. But this little tip can pull you out of some serious problems. There are several new rogue security programs on the Web, and they all follow the same M.O.
Thousands of rogues are currently being distributed on the Web or by email. There are new ones appearing every day, and most of the time the new ones are simply old ones with new names and updated user interfaces.
Some of these rogues spawn full-page alerts (or popups) that always stay on top of all other windows, no matter what you do. These kind are particularly annoying because you can’t access your browser, Windows Explorer or any other program because the rogue window is always on top. Some of these full page alerts and popups have no “X” in the top-right corner with which to close them, some do but the “x” does not work, while some work but only close the alert or popup window momentarily.
You can get these rogues simply by visiting a web site or by clicking an attachment in an email. We wish we could give you a list of these sites but there isn’t any way to do that. The sites distributing these rogues may be legitimate sites which have been duped into “selling” these rogues; they may sites which are owned by less-than-honest business people who are trying to make a quick buck by partnering with the crooks who make these rogue security products; or they maybe sites created by the crooks themselves. And even if we could give you a list of sites – it would change and grow every day – there’s just no way to keep up with them. But you don’t need to know the sites, all you need to know is this:
When a warning appears telling you that a virus or Trojan has been detected on your computer – DO NOT PANIC. Take a deep breath. Look carefully at the warning. Pay no attention to fancy Windows-like graphics. Look to see if the name of your security program(s) appear anywhere on that warning. If you use Avast – does it say Avast? If you use Microsoft Security Essentials, does it say that? If you use SUPERAntiSpyware – does it say SUPERAntiSpyware?
You get the picture. If it’s a rogue – it won’t know what security software you have installed, but the alert usually will have a legitimate sounding name on it – like Windows Internet Security 2011. CleanThis, Windows AntiVirus 2011 or similar.
You’re going to have to reach down and hold on – take a deep breath and use all your willpower so you don’t click the “Scan and clean my computer now” button. Remember, if you do click the scan and clean button on one of these rogues, you’ll be installing it. And if you do actually install one of these rogues, you’re going to have a lot more problems.
If you make a mistake and become infected or click a link that causes you to be infected, it’s important that you don’t panic. You can recover from this type of attack, but you need to stay calm and not do anything crazy like click “Purchase ….. now”, or “Clean your computer now”, or “Activate now”.
A number of these newer rogues are ingenious in their design. Their popups cover your entire screen when you start your computer. And you’ll have no way to minimize or close it – they give you one easy choice. The choice you’ll have is to buy the rogue security program by clicking the button on the popup which says “Buy now and clean your computer”, or similar. It can be very frustrating to users – many of whom don’t know how to get this popup off their screens. You can’t use ALT F4 to close it. There is no X in the top right corner, there is no icon on your taskbar to right-click and close – and sometimes you can’t see your task bar at all anyway.
If this happens to you – and it will happen to you sooner-or-later – there is a very simple solution. But you have to remember it and you have to remember not to panic. Here is the simple solution:
1. Shut your computer down. The only way you’ll be able to shut down is by turning off your computer. Use the power switch. You may not be able to shut down normally because your start button will be covered by the popup. (Some of the rogue’s cover everything but the taskbar and the start button – but when you click anything on the taskbar, the rogue popup reappears as soon as you click “Start” or anything else.)
2. Now after your computer has been shut down for at least a minute, turn the power button on and keep tapping the F8 key while Windows is booting. This will open your Safe Mode options. Choose “Safe Mode with Command Prompt”. This is the only option you should use in this scenario. The reason? Because it doesn’t start Windows Explorer – it opens a Window CMD window – the black and spooky “DOS window”. But have no fear. Your computer is not connected to the Internet. You’ve isolated your machine.
3. When the command window opens – and this can take some time so be patient – you’ll see something like C:\Windows\System32>
When you see C:\Windows\System32 > type rstrui.exe and press the Enter key.
Sit back, grab some coffee – or if you’re really nervous grab a double shot of Irish whiskey- and wait. It may take 5 or 6 minutes before you see anything change. But don’t worry, eventually it will change.
After a few minutes you’ll see the System Restore dialog appear. And when it does, start breathing easier because you’re almost home free. Choose a restore point at least 24 hours prior to the time you were attacked. After you have selected a System Restore point, go ahead and restore your computer. After a few minutes your computer will reboot. When Windows boots, your rogue security program will be gone, no more popups, no more trouble – it will be like nothing ever happened.
And the best thing is – you won’t lose any emails, photos, music files, or documents, etc. The only thing you’ll lose is any program(s) you’ve installed since the restore point you chose.
This tip can be used for many other problems too. Safe Mode with Command Prompt does not even load the Windows shell – but it does load the Windows system files, so you can access other Windows tools and features from the Command Prompt.
The key is RSTRUI.EXE and accessing it from Safe Mode with Command Prompt. Because when you do you can go back in time and get rid of the rogue and all the changes it made to your system. And your computer will be back to normal. It will be like the problem had never even happened.
Memorize this tip – or print it out. It will come in handy someday. Right Bill?


If this situation arises, could you not use Alt+F4 to close out this message?
The article points out that Alt F4 doesn’t close the window. If it were that easy we’d have recommended it first. We’ve actually installed these kinds of malicious programs on test computers to find out how they work. Alt F4 is useless against the worst of these kinds of programs. The programmers who create them are aware of all the ways there are to close windows. You can’t even access your taskbar or start menu to get to Task Manager to end the process. And the malware installs itself to three or four different locations with 3 or 4 different names – so ending the process of one just causes the process of another to start.
The only way to get out of this situation is to boot with USB flash drive which has security software installed on it (and the problem with that is not every computer is configured to boot from a flash drive) or use the tip we present in the article. It does not require users to change boot configuration or to download any software. It requires only Windows XP, Windows Vista, or Windows 7 – and some patience. And it works every time and doesn’t leave a single trace of the infection on your computer.
I have different colors of “butterflys”, purple in color boarder that has made an appearance on the top of everything I open..be it your page or my home (which isn’t yours) page etc. It also has some of my ‘favorites” printed in the boarder.Is this something that downloaded without my knowledge? Doesn’t seem to bother anything. It’s just I never had it before a few weeks ago? June