A New Password-stealing Trojan is on the Loose – Be Careful with Email Attachments
Microsoft Security discovered malicious fake PDF files that download the Java-based StrRAT Trojan which can steal credentials, passwords and change file names but does not encrypt them as ransomware does.
According to BGR…
Stop opening PDFs attached to emails unless you’re absolutely certain about where they originated and who is sending them to you.
Not that most of you were likely opening such email attachments with wild abandon before now, but be warned — Microsoft’s Security Intelligence team has uncovered what sounds like a Trojan malware attack as part of a “massive” email campaign with a nasty payload — malicious PDFs, which download a password- and credential-stealing Java-based remote access Trojan called StrRAT. In addition to stealing credentials and even taking control of systems, Microsoft researchers have also found that this malware can disguise itself as faked ransomware.
‘When running on a system,” Microsoft explains in a tweet thread about this particular malware, ‘STRRAT connects to a C2 server. Version 1.5 is notably more obfuscated and modular than previous versions, but the backdoor functions mostly remain the same: collect browser passwords, run remote commands and PowerShell, log keystrokes, among others.’
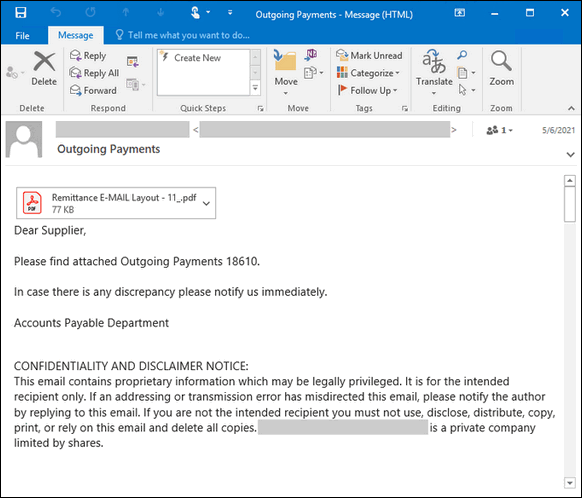
(According to Threatpost)‘…Some of the messages, for example, come with the subject line “Outgoing Payments,” which might seem innocuous enough to someone at a small business… Others purport to have come from the ‘Accounts Payable Department.’
The campaign includes several different emails that all use social engineering around payment receipts to encourage people to click on an attached file that appears to be a PDF but that actually has malicious intent,” Threatpost continues.
‘One email informs the recipient that it includes an ‘Outgoing Payment’ with a specific number — presumably, the attached PDF. Another addresses the message to a ‘Supplier’ and appears to let the receiver know that ‘your payment has been released as per attached payment advice,’ asking the recipient to verify adjustments made in the attached PDF.’
The delivery mechanism for this malware, via the phishing emails, is arguably something of a weakness, in that in this case it requires the victim to take an action to set this whole thing in motion… Read the entire post on the Web.
If you’re using Microsoft Defender or Emsisoft, you should be protected from the StrRAT Trojan. But don’t tempt fate. The best way to avoid this password-credential-stealing malware and other malicious software is to follow the advice we’ve been giving you for years. Never open email attachments unless you’re certain you know who sent the attachment(s) and you were expecting them. If you’re not sure, don’t ever open attachments in email. It is always better to be safe than sorry.


Great Information, Darcy, thank you. By the way, I got my Emsisoft License Key and installed it on my new laptop. Thankfully, I had an External Drive, WD Passport, and managed to download the files I wanted that were on my old laptop before it died…I mean totally, would not boot up, just kept trying, then showed Hibernating, in perpetuity. Drove me crazy, and for me, that’s a short drive. LOL. Anyway, you might want to advise folks of the importance of having an external drive attached at all times to their computer or laptop. It saved me hours of time getting all my old stuff instead of having to go to each website to download things. Thanks again.
Sandee