There’s a relatively new variant of an older Trojan/worm spreading across the Internet and this one is unusually bad because of the way it works and because if you’re not wary it could cost you $300 or more — and because most antivirus programs don’t catch it until it is too late.
It’s commonly called CryptoLocker — it’s been around for a few months now.. While it’s several months old, it has started to spread across the Internet and is becoming more and more prevalent and more and more people are becoming infected. So it now more likely you’re going to come in contact with it sooner or later.
It’s a particularly nasty ransomware variant in that it encrypts various file types on your computer and locks them so you can’t access them unless you have a key to decrypt them. Of course, the miscreants who developed this ransomware, want you to pay them $100 to $300 or more for the decryption key that will decrypt the files and allow you to access them. If you don’t pay the ransom, the files will remain locked and you’ll not be able to access them, even if you subsequently remove the ransomware from your computer.
CryptoLocker spreads by email…and this method of distribution is not new. It generally comes as a business email supposedly from FedEx, UPS, Amazon or some other company most of us are likely to have had done business with. The first clue you should have that something is amiss, is that the letter is poorly written — obviously not composed by someone who speaks English as their first language. This email comes with an attachment which carries the ransomware and if clicked with start the program and then start encrypting files on all drives in or attached to your computer.
We have reminded all of you many times: Never click a link in an email if you’re not sure who the email is from and you don’t know where the link leads. And NEVER NEVER NEVER open an attachment if you were not expecting an attachment and you are sure you know who it came from.
While most antivirus products won’t stop this worm from infecting your computer, Emsisoft will stop it and you’ll be protected from it. It’s one of the few security products which proactively prevent this worm from infecting your computer. In fact, Emsisoft wrote a blog about this particular ransomware in September — and we are featuring it in today’s newsletter – and we will publish it on our InfoAve site at https://thundercloud.net/infoave/new/
What file types are affected by this worm? Here are some, but not all, of the file types it will encrypt on your computer. One they have been encrypted, you will not be able to access them: *.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.mdf, *.dbf, *.psd, *.pdd, *.pdf, *.eps, *.ai, *.indd, *.cdr, *.jpg, *.jpe, img_*.jpg, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7c.
When it has finished encrypting your data files it will display the CryptoLocker screen:
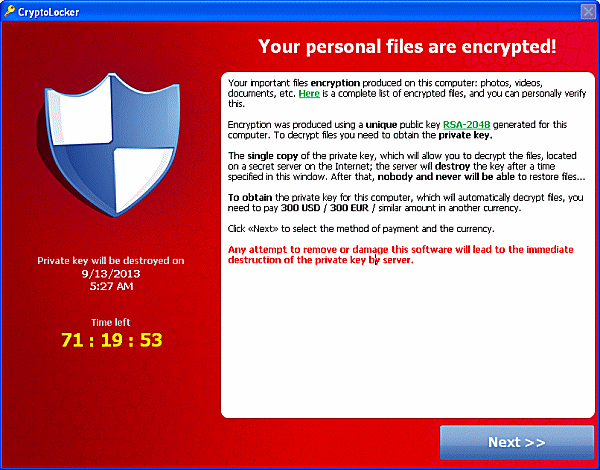
CryptoLocker wants you to pay the ransom by sending 2 bitcoins to an address (URL) that is dynamically generated. Bitcoin payments cannot be traced. A Bitcoin is worth around $200 U.S.D. If you want to know more about what Bitcoins are see http://en.wikipedia.org/wiki/Bitcoin . If you don’t want to get the details about Bitcoin — essentially it’s a way to pay and get paid anonymously — payments cannot be traced back to the payee or payer (theoretically — the NSA and FBI not withstanding).
As we said, once you’re infected, removing the infection will not decrypt the encrypted files. So the best way to avoid all this is to not become infected. As we pointed out, Emsisoft is one of the very few antivirus/anti-malware programs that will prevent you from becoming infected in the first place.
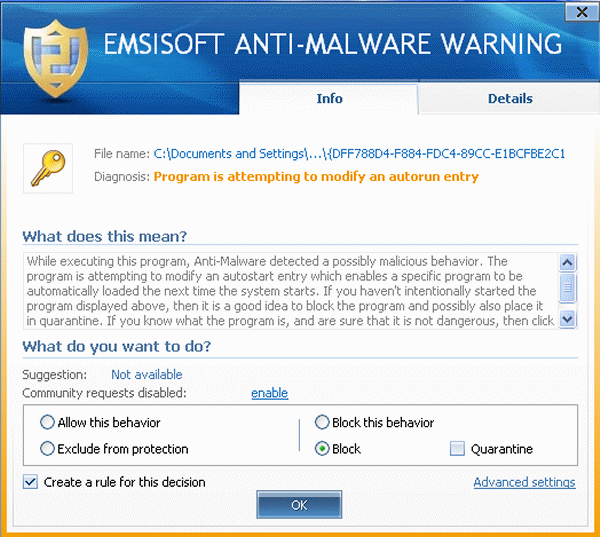
Above – Emsisoft blocking CryptoLocker
Users of Emsisoft Anti-Malware are not at risk of falling victim to either CryptoLocker or the malware downloader from the initial email campaign, unnoticed, as both are no match for our award winning behavior blocking technology.
But we know, not all of you have Emsisoft — so what happens if you do become infected?
#!. DO NOT PAY THE RANSOM.
No matter what — do not pay these criminals a cent.
#2. Keep your pictures and documents and other important files backed up in “the cloud”. There are many good, free, cloud storage services and some offer a generous 5GB of space — and you can have more than one. Keep a good image back-up on an External drive – but keep in mind any drive attached to your computer is subject to infection.. Keep a backup of those files you simply cannot replace on off site on a good cloud storage service online. There is some suggestion that the CryptoLocker infection may encrypt files on external drives as well. These probably would not affect image backups since most backup programs store their backup files in proprietary format. But just in case, do use a good cloud storage service to back-up your irreplaceable files — pictures, documents, videos, movies, etc.
#3. Don’t forget System Restore. System Restore offers you a way to restore your files to a time before you were infected.
At the first sign of infection do this:
1. Do not panic
2. Shut your computer off using the power switch – DO NOT REBOOT – some computers are made so the power switch is set to reboot the computer — only holding it in for several seconds will shut it down. It is important that the computer be turned off completely; if necessary unplug your computer from the wall.
3. Wait 2 minutes
4. Turn your computer back on using the power switch
5. Immediately after pressing the power switch, start pressing the F8 key continuously and rapidly until you see the Safe Mode boot menu
6. From the boot menu select “Safe Mode with command prompt” *** This is important *** if you choose any other version of safe mode, the CryptoLocker will load. Be sure to select SAFE MODE WITH COMMAND PROMPT
7. You will see Windows loading files – it may take a long time.
8. When everything is loaded, you’ll see a black screen with a command prompt which looks like this: C:\ >
9. At command prompt type RSTRUI.EXE (WINDOWS XP users see the note below* – Windows 8 and 8.1 users see note below **)
10. Windows System Restore will load — but it may take a very long time – don’t panic, be patient.
11. Select a restore point at least 2 days prior before the date of the infection
12. Run System Restore
13. Once System Restore is finished, you’ll boot into Windows and you be back to normal.
*Windows XP users: At the command prompt type CD: C:\Windows\System32 (exactly like that) and press Enter. The command prompt will now look like this C:\Windows\System32> . At that prompt, type RSTRUI.EXE and press Enter. Then follow the instructions above starting with #10.
** Windows 8 and Windows 8.1 users: See this guide for booting into safe mode on Windows 8 and 8.1. http://www.howtogeek.com/107511/
A reminder: If you get infected, removing CryptoLocker with your antivirus program or anti-malware program (if they can even remove it) will not solve your problem; it will not unlock your files, so you will still not be able to access them. The files are encrypted and the only way you’ll be able to open them again is with the decryption key — which you don’t have and won’t have unless you pay the ransom— DO NOT PAY THE RANSOM no matter what. If you do you’ll be part of the problem because you’ll be encouraging the criminals to develop more of this kind of stuff.
The best way to deal with this threat is to not get it in the first place. Emsisoft users are protected. If you don’t have Emsisoft (and even if you do) safe computer operating procedures are important. Never open an attachment you were not expecting AND do not open an attachment unless you’re positive you know who sent it. You cannot be positive by simply looking at the sender’s address — it could be forged. If in doubt, and it’s a friend of yours, call them or write them and ask if they sent you an attachment — and ask what it is.
The best advice though is : NEVER open an attachment from an email.


URGENT –
I have the Emsisoft Emergency Kit. But have Bitdefender also. Plus lifetime SuperAntiSpyware Pro and UnHackme.
Must I now purchase Emsisoft also????
I trust your guidance. I’ve been a lifetime subscriber for years and you’ve guided this 83 year old geezer past many pitfalls. THANKS
We are not saying anyone has to purchase anything. You’d have to check with BitDefender to learn if they prevent you from getting infected in the first place. From what we understand, many will not — some will clean the infection after the fact, however then it is too late because many of your personal files have been encrypted and can’t be decrypted without the encryption key.
I cannot answer questions for BitDefender. We recommend Emsisoft for a reason — because it’s not only one of the best anti-virus programs, it’s one of the best antimalware programs.
Emergency Kit is not a real-time scanner — therefore it would only remove the parasite after the fact — hence your files would still be encrypted. The reason Emsisoft works to prevent this infection is because it is a real-time scanner and its behavior blocker recognizes CryptoLocker and prevents (blocks) it before any damage is done.
SUPERAntiSpyware is an anti-spyware. CryptoLocker is not spyware, therefore it does not protect you from CryptoLocker nor does it remove it after infection.
The reason we tested Emsisoft in the first place was because we were looking for a good antimalware that would prevent people from getting infected with PUPs and malware — and to remove them once they were infected. We were not aware at first that it was also one of the top anti-virus programs too. So it was kind of a no-brainer for us to install it on our own computers which we did when we finished testing. We both used it for about two weeks (after two weeks of testing) and then we recommended it to our readers.
Sorry I cannot answer your questions about BitDefender Pro — only BitDefender can address that question.
And we never forced anyone to buy Emsisoft –but the fact that we use it on business computers, our personal computers, and our families and friends now all use it speaks volumes for what we think of Emsisoft.
Not only is Emsisoft, in our opinion, the best anti-virus / anti-malware program available today, but their support is amazing, and we are in contact with the developers almost every day. They’ve been responsive to our requests for changes in the program — and to our readers’ as well. In fact, by the end of this year Emsisoft will implement some major changes we have recommended to them –that will make it even better.
Too many nasty people out there. We should have the capability to send a command back to them when they send these things and burn their fingers and set their computers afire!
Well…I’m not sure anyone will read this now. I’m trying to copy my documents from C drive. It’s impossible without buying some program. Or I have no idea what I’m doing. I try to click just my documents and it adds music etc. Then I tried clicking on individual files–it still insisted on the entire documents folder! What is this!
Ok I finally found a way to do this! It was so easy on my extra hard drive. I save most things on my second drive. But I don’t save all things. And over a period of a couple years this adds up. I put in my empty disk. Then I opened my documents in question. I then dragged the folders and documents I wanted on this disk in the list over on the left side. Before I’m not at all sure what the heck all it was copying! But I can’t find any disk with over 25 gigs for copying! LOL YEAH got it all copied. I used a Dvd disk which is much larger than the cd disk. So, I got much more on one disk! I double checked the two disks I made. I made a spare just in case. They both work fine!
Oh yes I added this in case anyone else has same problem!
I’m so hoping others read this. I wonder if this can effect the macs? We use a mac for business and we back it up every day. But still having to reload the whole thing…what a mess!