VeraCrypt: The best TrueCrypt replacement
TrueCrypt lived a long life. It was the most commonly used Windows encryption tool until TrueCrypt, with no warning, closed up shop. Since then many other have tried, none ever attained TrueCrypt’s popularity or ease of use, until VeraCrypt came along.
VeraCrypt is a powerful encryption tool and for most of us not something you can use out-of-the-box, so to speak. If you’re an advanced user, you’ll probably be able to figure it out without referring to the documentation. I am not an encryption expert, but I found the documentation easy to understand, and the program easy to use IF you refer to the documentation and don’t click things with understanding what you’re clicking.
Make no mistake, VeraCrypt is powerful encryption software – its encryption algorithms are thousands of times stronger than TrueCrypt, and the program is almost as easy to use. But again, we remind you, even if you are an advanced user, do not assume anything, check the documentation is you don’t understand something. Unlike most programs, clicking the wrong thing or doing things the wrong way can really cause severe computer problems. The documentation is easy to read and understand – there is no reason not to refer to it if you find yourself not understanding something.
Why do you need VeraCrypt? You don’t need it. If you have confidential files on your computer that you want to encrypt and keep safe from all prying eyes, VeraCrypt can do that. The only way anyone can ever get the information stored in volumes encrypted by VeraCrypt is is by using a password – your password.
Maybe you don’t have anything that sensitive on your computer; maybe you just want to learn something new – this is a great way to learn more about Windows and encryption techniques. Maybe you want to store you credit card numbers, important documents or other sensitive items on your computer and you want a 100% money-back (no money back really, EB, just a figure of speech!) guarantee than no one – no one – can ever access your sensitive files and folder without your password.
We are certainly not encryption experts, but after one reading of the Beginner’s Tutorial we were able to create and mount and encrypted drive ( Z ) and move and/or copy files to it. (Obviously if these are confidential or sensitive files you’re going to want to move — not copy 00 the files to encrypted folder/drive.)
Here’s a snippet from the Beginner’s Tutorial:
Beginner’s Tutorial
How to Create and Use a VeraCrypt Container
This chapter contains step-by-step instructions on how to create, mount, and use a VeraCrypt volume. We strongly recommend that you also read the other sections of this manual, as they contain important information.
STEP 1:
If you have not done so, download and install VeraCrypt. Then launch VeraCrypt by double-clicking the file VeraCrypt.exe or by clicking the VeraCrypt shortcut in your Windows Start menu.
STEP 2:
The main VeraCrypt window should appear. Click Create Volume (marked with a red rectangle for clarity).
STEP 3:
The VeraCrypt Volume Creation Wizard window should appear.
In this step you need to choose where you wish the VeraCrypt volume to be created. A VeraCrypt volume can reside in a file, which is also called container, in a partition or drive. In this tutorial, we will choose the first option and create a VeraCrypt volume within a file..
There is, of course, a lot more to the tutorial. You’ll be given an option to read it as soon as you’ve installed Veracrypt – or you can always read it online here. We highly recommend you read it before you start using the program.
Now we’re going to give you some information about Veracrypt from the author and show you some screen shots from our first experience with Veracrypt.
What does VeraCrypt bring to you?
VeraCrypt adds enhanced security to the algorithms used for system and partitions encryption making it immune to new developments in brute-force attacks.
VeraCrypt also solves many vulnerabilities and security issues found in TrueCrypt. The following post describes some of the enhancements and corrections done:https://veracrypt.codeplex.com/discussions/569777#PostContent_1313325
As an example, when the system partition is encrypted, TrueCrypt uses PBKDF2-RIPEMD160 with 1000 iterations whereas in VeraCrypt we use 327661. And for standard containers and other partitions, TrueCrypt uses at most 2000 iterations but VeraCrypt uses 655331 for RIPEMD160 and 500000 iterations for SHA-2 and Whirlpool.
This enhanced security adds some delay only to the opening of encrypted partitions without any performance impact to the application use phase. This is acceptable to the legitimate owner but it makes it much harder for an attacker to gain access to the encrypted data.
Starting from version 1.12, it is possible to use custom iterations through the PIM feature, which can be used to increase the encryption security.
Starting from version 1.0f, VeraCrypt can load TrueCrypt volume. It also offers the possibility to convert TrueCrypt containers and non-system partitions to VeraCrypt format.
UPDATE August 9th 2015 : VeraCrypt 1.14 has been released. It adds the possibility of creating volumes using command line on Windows. It also adds some features and fixes some issues. Please check the release notes for the complete list of changes. Download for Windows is here.
UPDATE August 9th 2015 : VeraCrypt 1.13 has just been released to address reported crashes of Tor Browser when run from a VeraCrypt 1.12 volume. Users that already installed version 1.12 are encouraged to update to version 1.13.
As usual, a MacOSX version is available in the Downloads section or by clicking on the following link. It supports MacOSX 10.6 and above and it requires OSXFUSE 2.3 and later(https://osxfuse.github.io/). MacFUSE compatibility layer must checked during OSXFUSE installation.
Also a Linux version is available in the Downloads section or by clicking on the following link. The package contains the installation scripts for 32-bit and 64-bit versions, and for GUI and console-only version (choose which script is adapted the best to your machine).
All released files are signed with a PGP key available on the following link :https://www.idrix.fr/VeraCrypt/VeraCrypt_PGP_public_key.asc . It’s also available on major key servers with ID=0x54DDD393.
Please check that its fingerprint is 993B7D7E8E413809828F0F29EB559C7C54DDD393.
SHA256 and SHA512 sums for all released files are available in the Downloads section…
Now we’re going to show you that we, with hardly any encryption experience, used VeraCrypt to create an encrypted volume – into which we can stash our sensitive files like how much money EB pays me – we sure want to keep that a secret…I’d be embarrassed and EB would look parsimonious. Really!

The first dialog – Volume Creation Wizard is pretty straight shootin’. We choose the first option as it’s the one recommended for inexperienced users – that be us in this case, I tells ya!
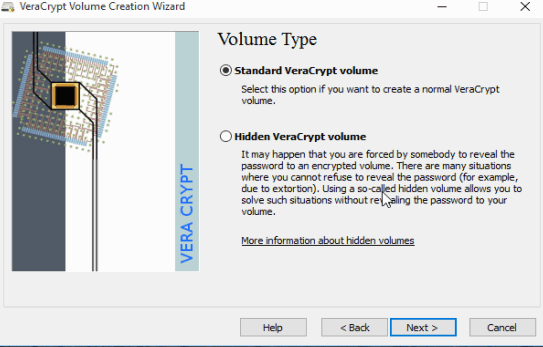
See — we are making a place to store files in an encrypted volume.
Formatting our new volume. Read the Beginner’s Tutorial to learn how to strengthen the encryption by moving your mouse around inside the dialog – really!
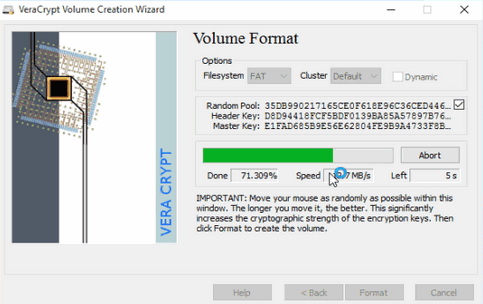

We’re doing good! OK, EB, the grammar police are out and about – “We’re doing well!”
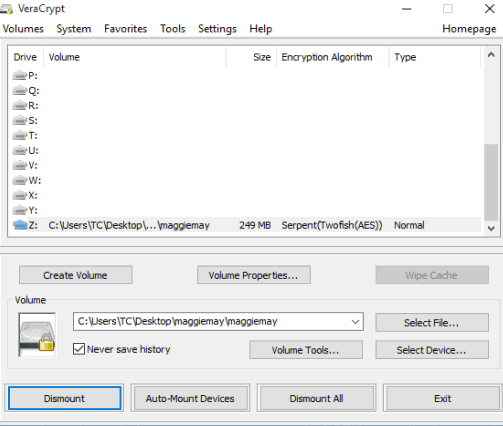
Above we’re mounting the volume, nothing like mounting a horse. We choose the drive letter Z – for no particular reason.

Yay for us. We successful mounted the encrypted volume (drive) we created. See? Look up!
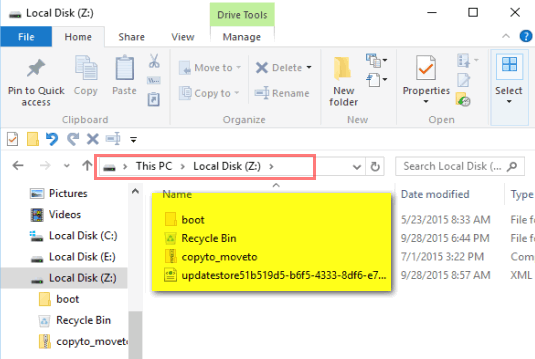
We copy/move some files to our new encrypted volume. As long as we’re logged in we don’t have to use our password to access this encrypted drive, but if we reboot or shut down and restart, we will not be able to access anything we moved to this drive. Make sure you use a strong password and make sure you can remember it without writing it down – if you must write it down store it someplace other than in your purse or wallet or next to your computer.
We were able to use VeraCrypt after a quick review of the Beginner’s Tutorial – and you will able to also. Even if you don’t want to encrypt your files, this program is fun to learn and when you’re done and you have created and encrypted volume, you’ll feel like a real geek – and EB will send you pair of horned-rim geek glasses if you ask her really nice.
You can read more about and/or download VeraCrypt from the author’s site. There are no games going on there, no malware bundled with the file, no download tricks. VeraCrypt is free.

