A New Villain In Town
His name is Poweliks (or her name is Poweliks, if you prefer). And while Poweliks has been around since last summer we hadn’t seen any cases of it, until this week when we saw three in one day.
Now the reason that Poweliks deserves mention here (there are always dozens of new black hat released every week) is that Poweliks doesn’t run an executable but runs a Windows PowerShell script which writes data to the registry Because it does not function as a typical malware file – i.e. it’s not something you install and because it is so new, antivirus programs are just now writing definition files for Poweliks.
We’re going to let the experts tell you more about Poweliks in detail, but we’re going to show you and easy way you can tell if you’re infected.
Open Task Manager ( CTRL+SHIFT+ESC) and click the processes tab. If you see several (or dozens) of processes with the name dllhost.exe*32 running, then you have Poweliks. And it’s important that if you have it your remove it quickly as it is hardcoded with IP addresses of servers it connects to and downloads commands and possibly scripts. We suspect (although cannot prove nor has anyone else made this connection) that if Poweliks remains active on a computer for very long that it can download a script which will then encrypt JPG (picture files), MP3 (music files) and some types of documents. And according to a ransom note left behind, the only way to remove the encryption so you can use / view the encrypted files is if you pay a ransom to the miscreants, usually $400 to $500. They want you to install the Tor browser and pay with Bitcoin – this ensures they can’t be traced – or at least not by normal methods. Now are not sure whether the file encryption we have seen in 2 of the 3 cases of Poweliks we discovered this week during Cloudeight Direct Computer Care sessions this week is related to Poweliks or not. It may be coincidental, but I’m not a big fan of coincidence.
Here is a screen shot showing Task Manager/Processes tab of a computer infected with Poweliks:
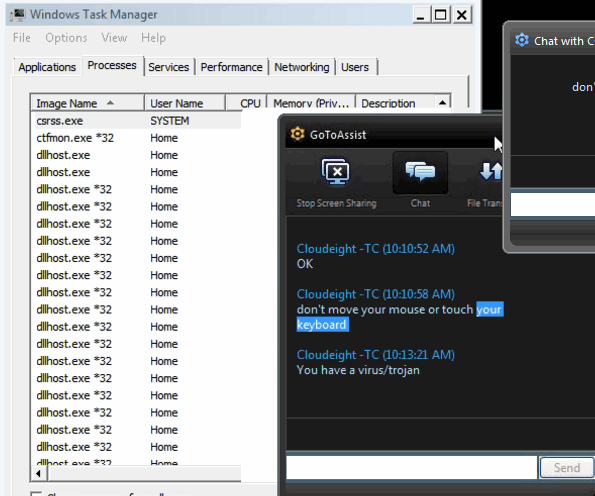
Screenshot of Poweliks’ processes running on a Windows computer during an actual Cloudeight Direct Session.
While most good antivirus and antimalware programs are being updated to catch Poweliks before it does its thing, the best defense is what we’ve been telling you all along — good common sense. Apparently Poweliks spreads via spam email and poisoned Word documents. From what we’ve discovered it appears most of these spam emails with the attached poisoned Word document are fake emails from the USPS (or other shipping company) regarding package delivery. Why anyone not expecting a package would open such an attached file, escapes us. No shipping company, not the USPS, FedEx, DHL, UPS, are going to send emails with attachments. So common sense dictates you don’t open attachments unless you are 100% sure who send it and you were expecting it. It’s easy to fake the “FROM” address so don’t assume if something says from FedEx, USPS, UPS, etc. that it actually come from them. And if you’re not expecting a package why would you open the mail. Use your heads! Use your common senses! We have been preaching this same mantra for years. Also keep Adobe Flash and Sun Java updated – always. It seems Poweliks can infect your system through unpatched old versions of Flash Player and Java.
1. Think before you click.
2. Think before you open an email.
3. Think twice before you ever open an attachment of any kind.
4. Do not click links in email unless you are 100% sure you know who sent it.
5. Be sure the antivirus you use can protect you from both viruses and malware.
6. Don’t base your antivirus/antimalware choice based on price. Free antivirus may not really be very free if you have to pay someone to clean your infected computer
7. Make sure you keep your Flash and Java up-to-date. Vulnerabilities in older versions can be exploited by Poweliks.
The following is a more technical description of what Poweliks is and how it works.
“A new piece of malware referred to as Poweliks tries to evade detection and analysis by operating completely from your system registry without having files on the disk, security researchers alert.
The technique of “fileless” malware that only is present in the system’s memory isn’t new, but such threats are rare simply because they don’t live through system reboots, in the event the memory is cleared. That’s not the case for Poweliks, that takes a fairly new strategy to accomplish persistence while staying fileless, as outlined by malware researchers from G Data Software.
The Poweliks malware spreads via emails which includes a malicious Microsoft Word document. The document holds all the code required for the attack, encrypted and hidden, once executed the malicious code generates an encoded autostart registry key and to fly under the radar it keeps the registry key hidden.
Poweliks creates a registry entry that executes the legitimate rundll32.exe Windows file followed by some encoded JavaScript code. This triggers a process similar in concept to a Matryoshka Russian nesting doll, said Paul Rascagnères, senior threat researcher at G Data, in a blog post.
The JavaScript code checks whether or not Windows PowerShell, a command-line shell and scripting environment, exists on the system. When it isn’t, it downloads and installs it after which it decodes even more code that is really a PowerShell script.
After it’s successfully installed, Poweliks attempts to contact hardcoded IP addresses to receive further commands from the attacker.
Following these steps explained by Paul Rascagneres, Senior Threat Specialist at GData:
As the entry point, they exploit a vulnerability in Microsoft Word with the help of a crafted Word document they spread via email. The same approach would work with any other exploit.
After that, they make sure that the malicious activities survive system re-boot by creating an encoded autostart registry key. To remain undetected, this key is disguised/hidden.
Decoding this key shows two new aspects: Code which makes sure the affected system has Microsoft PowerShell installed and additional code.
The additional code is a Base64-encoded PowerShell script, which calls and executes the shellcode (assembly).
As a final step, this shellcode executes a Windows binary, the payload. In the case analyzed, the binary tried to connect to hard coded IP addresses to receive further commands, but the attackers could have triggered any other action at this point.
All activities are stored in the registry. No file is ever created….” (Source: http://zerosecurity.org/2014/08/poweliks-malware-drops-files )
If you find your computer has been infected, don’t wait! Make sure you remove it from your compuer ASAP. We can remove Poweliks from your computer with our Cloudeight Direct Computer Care service.


I found dllhost.exe*32 running, once. 603 Kilobytes COM surrogate. Does that mean I am infected if it is only listed once?
Keep an eye on it and if start seeing more and more – you’re infected.
I’m happy to say no dllhost.exe*32 was running on my computer. I appreciate you giving us a way to check.
In your seven point warning list above, number two is……”think before you open an email”
It is a frequent occurrence in my house for my wife to ask me if she can safely open a particular email from an unknown source.
Based on your instructions over the years, I invariably tell her that merely opening an email cannot expose you to nasties but under no circumstances to open any attachments or click on any URL’s.
Have I been laboring under a false sense of security all this time?