|
Cloudeight InfoAve Premium
October 7, 2011
Issue # 416
Volume 9 Number 1
Dear friends,
Welcome to InfoAve Premium, Issue # 416 - We're
glad to have you with us. Thank you so much for subscribing to
this newsletter and for all your support and kind words. We
appreciate it very much!
Welcome to the 9th year of InfoAve
Premium!
This is the first issue of InfoAve Premium as we
open our ninth year of publication. It's hard to believe we've been
writing and sending this email newsletter to you for eight years
now. The world and the Internet have changed so much in the past 8
years. Eight years ago, Windows XP was brand new and the iPod,
iPhone, iPad, Windows Vista, and Windows 7 didn't exist. There were
no smartphones and tablets were things you used to write grocery
lists and notes on. Desktops were the way most of us accessed the
Internet and laptops were not very popular. We've kept up with
things so we can keep you up with things and all the while we've
been committed to leaving the techno-speak out of this newsletter.
We've tried to keep our sense of humor to remind ourselves and you
that life doesn't begin or end with a computer. We've tried to keep
things in perspective and to make learning about computers as fun
for you as it is for us.
Without you this newsletter would have never made it
this long. Your donations, purchases, support and kind words have
kept us going. And we are very
appreciative - without your help and your support we couldn't have
made it through the past eight years. We're looking forward to a
fascinating ninth year which should include the introduction of
Windows 8, Amazon's Kindle Fire, iPad 3, iPhone 5, and who knows
what else? Thank you for making this newsletter possible and thank
you for the donations and support you give us. We both want you to
know it is very much appreciated.
Thank you!
NEW!
EXCLUSIVE OFFER FOR CLOUDEIGHT SUBSCRIBERS!
SAVE 15% OFF ON REIMAGE - No coupon code
required!
Offer good only for Cloudeight subscribers using the links provided
Reimage is one of our biggest selling featured products thanks
to you! And Reimage works on 32bit and 64bit
Windows XP, Windows Vista, and Windows 7.
The Reimage Scan is free. The scan will tell you what Windows
issues you may have with your computer. To fix your computer
you must purchase a license for Reimage. When you purchase you will
automatically get an exclusive 15% Cloudeight discount.
There are two good
reasons why Reimage has become one of our biggest selling affiliate products: It works
and its support staff is outstanding! If you are you looking for a
permanent solution to your annoying
computer problems, whether it be an agonizingly slow startup or
shutdown, constant Windows error messages, or problems running
programs or booting into Windows, Reimage can fix your computer.
Reimage is an online PC repair tool that repairs Windows
and makes your PC run like new again, for a fraction of the
cost that places like Best Buy, Staples, and other computer
repair services charge. And Reimage guarantees it will work for
you or you get your money back!
Reimage Features and Benefits
-
Requires no setup
-
Reimage is the
ultimate professional repair tool
-
Rebuilds the
entire Windows system - without damaging your programs or
files
-
Repairs damaged
operating system
-
Refreshes native
operating system drivers
-
All
Cloudeight subscribers save 15% off Reimage - use any of the
special links in this advertisement - or click here right now.
Don't waste your money on
inferior products or
spend hundreds of dollars on computer repair.
Repair Windows quickly and easily at fraction of the cost of
computer repair services like "Geek Squad".
Repair your Windows system in minutes
and save 15% right now!
If you need to change your
newsletter subscription address please see "Manage your
subscription" at the bottom of this newsletter.
We hope you enjoy this issue of InfoAve Premium!
Thanks again for subscribing. And thank you all for your
generous support.
A comment from Joan (regarding EarthLink's recent
block of our newsletter)
Here's my story to bring you and T.C. up to date. I contacted
EarthLink Support two times. Neither brought a resolve. I tried a
3rd time today, but Comcast lost connectivity for our phones and the
internet. TV was fine. I was "41 minutes" into support when this
happened today and, of course, getting nowhere fast and then lost
service. I called a different number when service returned and I
told the person I wanted to speak to someone in Atlanta in the Home
Office. I was connected to a fellow American named Jim in Knoxville,
TN. Hallelujah!
He does not work in the capacity of security but he documented my
information. I offered to forward him a copy of your newsletter -
great - also copies of your correspondence in answer to my
irreconcilable differences with their censorship. The one below and
also your July 12 response to my July 11 quandary. I also stated I
took great umbrage of EarthLink taking it upon themselves to censor
any of my e-mail when on my 'Web Mail' web site they can forward my
incoming e-mail to either Suspect Mail or Spam and I will evaluate.
I added that in their own words on their own Web Mail Preference
Settings, for a High spam blocker it clearly states that 'all' mail
would then go into the 'Suspect Mail' file. I also used your great
analogy about the U.S.P.S. determining for both he and myself what
they deemed as appropriate mail to deliver to us.
None of the above was communicated anywhere close to unpleasant. I
find a hostile approach will automatically be met with hostility and
the initiator loses. I do not particularly like to lose. One must
carefully pick their fights. Anyway, I digress, the conversation
could not have been more congenial and the following is to be the
outcome.
He receives the above three forwards. He will e-mail them to the
Security Team staff that handles blockers and firewalls, etc. They
will see what he sees and put Cloudeight into servers marked as
accessible. He will also ask them for a time frame (at my request)
for Security to resolve this and he will e-mail me this information.
He is also going to advise me when Cloudeight is put on the White
List. In my last forward to Jim I thanked both he and the Security
Team staff.
Also near the end of our conversation advising him of your
invaluable newsletter he asked for the spelling and pulled up your
web site. Not a problem, but that's no surprise.
Thank you for your support and I hope to see your newsletter
delivered to me tomorrow.
Thanks for sending this to us. It's still amazing
to us that ISPs think they have the right to take something
belonging to you - an email addressed to you belongs to you as much
as a letter does - and delete it. And worse - they seem surprised
when people question them about it. You handled this very well and
hopefully from now on you'll get our Premium newsletter without any
problem. Thanks again! TC & EB
A comment from Virginia
(commenting on our answer to
Kathy's
question about Active-X in last week's issue)
I am so glad Kathy asked that question. I couldn’t wait to read
your explanation. Like her, I’ve been reading your tips and
explanations for a long time. I am never afraid to try a program if
you two have endorsed it. Thank you both so much for all your
information and help. Have a blessed day. Virginia
Thank you for your nice comments and for
your confidence in us, Virginia. We're hope you found our
explanation helpful. Thanks, again! TC & EB
A comment from Evelyn
Thank-you for recommending
REIMAGE. I purchased the program recently and ran it. Some
Windows updates automatically went in the next day and my Windows
Live Essentials - Mail, etc would not work. I contacted
REIMAGE and after 3 techies and after 17 hours over 3 days of
investigation, they found out what the offending update was and
removed it. All of this was done at NO extra cost. Very pleasant
people to deal with. I can't say enough good things. All my files,
pictures, programs are intact. Thanks again for recommending them -
I will certainly be telling lots of people about them. Also,
thank-you to both of you for all you do. Regards, Evelyn
Thanks so much for your comments and your
recommendation. The Reimage team is willing to go the extra mile to
make sure you're satisfied and that's another reason we're proud to
recommend and endorse Reimage. A great program still needs great
support - and Reimage has both. Thanks for writing and for your nice
comments! TC & EB
A comment from us about
the death of Steve Jobs
We were both saddened when we learned of the death of Steve Jobs.
While this is a Windows newsletter, we have always admired Steve
Jobs and the innovations he brought to world of technology. IAny of
you who use a mouse are using one of his innovations. The graphical
user interface of Windows, is a Steve Jobs innovation. Even the
beautiful fonts we enjoy on our Widows computers came into being
because Steve Jobs once dropped in on some calligraphy classes. So
whether or not you're using Apple's products, a lot of what you're
using came from the mind and the creativity of Steve Jobs.
Perhaps the best way to honor his memory is by sharing his words
with you. If you haven't read this commencement address given by
Steve Jobs,
please take a few minutes to read it. It will be worth your
time.
We will miss his creativity his innovation and his
contributions to the world of computers and technology. As Steve
Jobs said at the end of his commencement address at Standford: "Stay
hungry. Stay foolish."
Your comments are always welcome!

We really need your help!
If you can help us right now by making a
donation, we'd very much appreciate. We do realize that many of
you are having a tough time right now too. But if you are able
to help us get through a very difficult time, we'd be very
grateful. We continue to work as hard as we can to provide you
with the very best computer newsletter on the Web - and your
support and encouragement has helped us immeasurably. We've cut
our expenses as far as we can and still keep things going. Many
of you have helped us many times and we appreciate it. If you
are able to, this week, please consider visiting our Donation
Station and making a donation. We have some very nice gifts
available for various donation amounts. We have a "donate any
amount" feature - where you can donate any amount you like -
even the smallest donations are greatly appreciated. We really
need your help. Thanks so much!
The following items are available right now
from our
Donation Station.
Your donations are very much appreciated. Thank
you!
Jack Asks About Phishing
What exactly is "Phishing". I have recently heard that term
on the news and seen it on the Web a lot. I enjoy your premium
newsletter very much. thanks, Jack
Our Answer
Thanks Jack. Phishing is a term used to describe the current
method of choice by hackers and other criminals to steal your
personal information by deceit. It's like fishing only in this
fishing expedition WE are the fish. The email comes to you looking
exactly like a legitimate email from a bank, credit card company, or
other financial institution asking you to "verify" your account
information. Of course no legitimate financial institution, bank, or
credit card company would ever ask you for this information via
email, especially not addressed to "Dear Cardmember" or "Dear
Account Holder". You may be asked to click a link which may well
appear to a link to the bank's Web site but links are easily
disguised. For instance:
http://www.google.com/
or http://www.citibank.com/
If you clicked those links where did you end up? On Google? On
Citibank? And those links were not very well disguised (i.e. we
didn't use a script to redirect you or some fancy HTML coding to
change the link ). Had we used a script it would have been harder
for you to tell without clicking it. However you could have
right-clicked that link and chosen "Copy Shortcut" from the menu
which appears and pasted it into an email or notepad file and you
could verify that the link was authentic. Or, depending on your
browser, you could hover over the links and looked in your browser's
status bar to see the real link. (The browser's status bar is the
bar across the very bottom of your browser window.)
If you ever have a question about where a link
might lead you it's always wise to use one of the above techniques
to check and make sure you know where you're going before you
actually click the link. Many new worms are spread this way.
However, whenever you receive an email from a financial institution
DO NOT CLICK THE LINKS IN THE EMAIL. If you get an email from your
bank, and it appears legitimate, don't click the links. If you think
your bank has something important to tell you, type the URL into
your browser's address bar or call them. Do not click links in
emails which appear to be from financial institutions ESPECIALLY if
the email is asking for you to verify your account information or
change/verify your password(s). Banks, credit card companies, and
other legitimate financial institutions will never ask you for
personal information (i.e. social security number, credit card
number, etc.) in an email, nor will they ever ask you to click a
link to verify your account information or to change your password..
Email is not secure. But click-happy people, click links in such
email or enter the information without thinking and this is why
identity theft is the fastest growing crime in the world. And all it
takes is a little lapse of common sense and your private information
is in the hands of a criminal who can and will use your identity and
information for his/her own financial gain. If you think your bank
has something important to ask you or your account needs to be
updated or verified, type the URL to your bank in the browser's
address bar or call the bank and ask. Do not ever, ever, ever, click
links in emails that appear to have come from a financial
institution - ESPECIALLY if the email is asking for you to verify
your account information or change/verify your password(s).
Peggy wants an easy way to launch Windows Calculator
Is there a quick way to bring up the calculator? I hate having
to click through start, programs, accessories, calculator. Thanks for
all your great tips. It impresses my friends when I show them what I've
learned from you. And I always pass on the great tips from your
newsletter.
Our Answer
Hi Lee. Here you go. Astound your friends and co-workers.
If you're running Windows XP, Vista or Windows 7, Click Start, Run, type
in CALC. In Windows XP or Vista you can right-click on Calculator and
choose "Pin to Start Menu". If you're using Windows Seven you can pin it
to your Start Menu, or to you can choose "Pin to Taskbar". Also
Calculator can still be found in your start menu under All
Programs/Accessories. And one more thing you probably don't want to know
but we'll tell you anyway. The file for Calculator is called Calc.exe
and it's located in C: \Windows\System32.
And if you're using Google Chrome browser, you can do
calculations right from the address bar. Things like 18*188114 or
1224/14 or 11+11+22+48+55 or 18801-1206 . You can add, subtract,
multiply or divide using the address bar of Google Chrome without using
Calculator. You can also do it from Internet Explorer and Firefox but
only if you have Google as your default search engine.
Patty wants to know about
system recovery disks
Hey, guys! I've got a stupid question. What is the difference
between the recovery disk that came with my Windows XP computer and
a Windows disk? If you could explain this to me I would be very
happy. Thanks a lot. Keep up the good work. Patty
Our answer
Thanks, Patty. There's no such thing as a stupid question.
The recovery disk that used to come with new PCs (they
no longer do and we'll get to that later) served one purpose: to restore
your computer to the state it was in the day you brought it home. So if
all you're looking for is a way to get your computer back to the way it
was when you first bought it, the recovery disk will do this. It's
quick. It's easy. It's a no-brainer to use.
A Windows installation disk contains only the
Windows operating system and nothing else. When you reinstall Windows
using a Windows installation disk, all you'll have on your computer when
you're done is Windows. Everything that was on your computer before -
programs, files, documents, settings, etc. will be gone. But there are
bigger problems with recovery disks than just wiping everything from your system.
Here's the problem with wiping your computer:
Most of us actually use our computers everyday. That
means we put stuff on it. Programs, files, photos, images, documents,
etc. We customize our start menus to match the way we use our computers.
We change our desktops the way we like them. We make all kinds of
setting changes and take great pains to do all we can do to setup our
computers exactly the way we like them. It can take months and months to
get a computer setup the way we like.
Using a Recovery Disk will wipe out everything that has taken you months
to do - all your files, all your images, all your documents, all your
settings - everything. It will take your computer back in time to the
day you first plugged it in. So essentially you're wiping your computer
exactly as you would if you used a Windows installation disk. But wait!
There are even worse things waiting for those who use a recovery disk.
Most new computers are filled with garbage and trial version software.
This is the computer manufacturer's attempt to make more money from
you than they've already made from you. They want to start selling you
more stuff in the after-market. Most of the programs computer manufacturers
put on computers programs most of us would ever choose to install. So a lot of
us like to remove all this junk as soon as we plug our new computer in
for the first time. Sometimes it's not easy - some of this software
seems to have ways of resisting removal. Plus, there's an awful lot of
it. So if you use the System Recovery Disk that came with your computer
---you guessed it - you will putting all this junk back on your computer
- it will be exactly the way it was the day you first plugged in your
new computer when it was brand new. This is something you wouldn't have
to deal with if you have a full Windows installation disk.
But now things have gotten even worse because most Windows 7 computers
don't even come with a recovery disk. You have the option to create a
recovery disk (called a System Repair Disc in Windows 7) by following the
instructions provided at
http://windows.microsoft.com/en-us/windows7/Create-a-system-repair-disc
. The only computer manufacturer we know of that still provides Windows
installation disks with their new computers is Dell. Dell charges $10.00
extra for a Windows operating system DVD. If you buy a Dell computer you
should pay the extra $10.00; it is well
worth it. If have purchased a Windows 7 computer - make sure you have a
system repair disk. If you don't, right now is a good time to
make one.
Remember though - the best way to protect your data is to create a
mirror image backup. If you have one, you won't need to worry about
System Recovery disks or making a system repair disk because your can
completely restore you computer to the state it was in - including the
operating system, settings, files, documents, etc. - before you had
major computer problems. To read one of our many articles on creating a
hard drive clone - or mirror image backup see
http://thundercloud.net/infoave/new/?p=2402 .
John wants to know if he's right to use Task
Manager to shut down his computer
Hi TC & EB. Going back a 'few' years to Win98 I always used Task
Manager (CTRL+ALT+DELETE) to shut down my computer, and I am sure
that the advice came from your good selves. I continue to shut down
the same way, as I feel somewhat uncomfortable using the Start,
Shutdown, and seeing the 'Force' programmes to close button, which I
don't use anyway. Your advice in this matter would be appreciated.
Thank you for your continued and positive recommendations. John
Our Answer
Hi John. Thank you! We don't recall ever giving any advice about
shutting down using Task Manager, but our memories are growing old -
so we may have. It really doesn't how you shut down your computer.
(Don't be silly, EB. Of course we don't mean pulling the plug or
using the on and off switch to shut down a computer!) Whether you
shut your computer down using the Start button or Task Manager or
use the command prompt, any running programs will be terminated
before Windows will shut down. The "Force" programs to close dialog
is a little strongly worded. Any programs that are running at
Windows shutdown will be terminated - before Windows can shut down
(or restart). When you use Task Manager to shut down you simply
don't see the "Force programs to close" dialog - but any programs
that are running will be forced to close - if they weren't closed,
Windows wouldn't shut down
Now's a good time to remind everyone that they can speed up Windows
shutdown by saving their work and closing all running programs
manually. If you close as many open programs as you can - after
saving any open work - it will reduce the number of programs that
Windows has to close, and this saves time.
Jean is concerned about hackers stealing her Outlook Express
passwords
I have Windows XP. I am wondering where email addresses are stored other than in
'stored user name & passwords' via the control panel and User Accounts? Mine
shows it blank...no passwords saved, yet when I ran the SIW program (System
information for Windows by Topala Software Solutions) I ran down each category
which included 'passwords'. I was shocked to find all my email addresses and
passwords there. Two of them were email addresses for Windows Live, which I no
longer have, but cannot find anywhere to delete those two. My question is where
else are system email addresses hidden? Is this normal? If my computer were to
be hijacked, I see how easy it is to get any of my personal emails and private
information. I always thought if there the stored email passwords area in user
accounts was blank, none were stored. Not the case. Can you advise? Thanks!
Our answer
Hi Jean. Outlook Express passwords, messages, and folders are stored in
several places - the main one is in your Outlook Message store. Passwords
are also stored in the registry. We're not sure what you mean about your
computer being "hijacked". For the sake of answering you we're going to
assume you mean a hacker - someone outside your home accessing your email
addresses and passwords remotely. The chances of that happening are very
remote - about one in one billion. Hackers don't sit in the shadows lurking
nearby waiting to hijack your computer. They may trick you into giving up
passwords and other personal information. They may trick you into installing
a data-stealing bot or Trojan. But the odds of a hacker targeting your
personal computer are infinitely smaller than you being struck by lightning,
or struck on the head by a meteor, or you winning the Mega Millions Lottery
(about 1 in 95 million). So your odds of winning "The Big One" in the
lottery are about 10 times greater than you having your data stole by a
hacker targeting your computer directly. You can
reduce your risks by not clicking on links in email that ask you to
click links to change your password or account information. You can
reduce your risks by keeping your computer protected with good antivirus
and antispyware programs and keeping them updated. You can reduce your
risks by thinking before you click. The horror stories you hear about
hackers lying in wait and stealing your information by "hacking" into
your computer are very very slim. Your PC or laptop is just of a billion
computers and devices connected to the Internet. If you have good security software, you don't
click on links in suspicious emails, and you use your own good common
sense, your risk is so small that your time would be better spent
worrying about something more probable. Now if you're
talking about someone with console access to your computer - i.e.
someone sitting at your computer and logged on as you, then that's
another story. If you allow someone to login as you then they'll see
whatever you can see. Don't let anyone you do not trust use you
computer. If you have two or more people using your computer, password
protect your Windows user account (Control Panel/User accounts). Then
set up separate restricted user accounts for each other person using
your computer. Even if you trust the others using your computer - always
set up separate password protected accounts for each person using your
computer. The others can change their passwords after you've set up
their accounts. Also, if you are using a wireless router,
make sure you are using good security and password protection -
it's essential and
it's easy to do. There was a time when someone had to be in close
proximity to your wireless router to intercept and use your wireless
connection. But now, your wireless can be intercepted by someone a
half-mile or more away. If someone gains access to your wireless router
they have access to any data that you transmit via your wireless
connection. And one more thing to remember -
everything you've ever seen or typed on your computer is still there
somewhere. Don't worry about the phantoms created largely by those
seeking financial gain by scaring you - i.e. firewall vendors. They sell
billions of dollars worth of software by scaring people - and they way
they like to scare people is by making it seem that your PC, my PC, EB's
PC, all of our PCs are just moments away from being "hacked" and our
personal information stolen by phantoms lurking in the ether. It just
ain't so. Use common sense. Don't click links in emails
asking you to "verify your account", or "change your password".
Especially don't click links in emails which may look like they're from
your bank, credit card company, or any financial institution which ask
you to verify your information or change your password - these are
almost always phishing emails or may contain links which will attempt to
install password-stealing Trojans. Keep your antivirus
and antispyware programs up to date. Most of all, don't worry about
phantoms conjured up by money-driven security vendors who want you to
believe your personal information will be stolen by "criminals" or
"hackers" unless you install their great software. It just isn't true.
Snap your mouse!
Windows XP, Windows Vista, Windows 7
One of the more annoying things about dialog boxes when you need to
confirm or click OK, is the fact there's no way of knowing exactly
where, on your desktop, that the dialog with the "OK" "Cancel"
buttons is going to appear. Sometimes it appears in the middle of
your screen; sometimes on the left, sometimes on the right,
sometimes at the top and sometimes at the bottom. Guessing where the
dialog box will appear is a game Windows users have been playing for
a long time. This isn't so bad when you only have one dialog box to
confirm or cancel. But what about those times when you're dealing
with multiple dialog boxes in rapid succession? You're going to be
all over your screen clicking OK or Cancel.
But did you know you can make your mouse snap to the default button
on the dialog box automatically - no matter where on your screen it
decides to appear? You can and here's how to do it!
To train, err I mean configure the mouse pointer in Windows XP,
Windows Vista and Windows 7, to land on the default button in the
dialog box, so you can easily select "OK" without even moving your
mouse.
Windows XP - Click on Start \ Control Panel and click on Mouse to
open the Mouse properties. Select the Pointer Options tab, then
select the check box next to "Automatically move pointer to the
default button in a dialog box". Click OK to save the setting and
close the mouse property window.
Windows Vista/Windows 7- Open the Control Panel by clicking on the
Start button in Vista or Windows 7, and type mouse in the search
box, then click on Mouse in the search results to open the Mouse
properties. Select the Pointer Options tab, then select the check
box next to "Automatically move pointer to the default button in a
dialog box". Click OK to save the setting and close the mouse
property window.
Nothing's better than a snapping mouse - except maybe a snapping
turtle...or a snapping spouse :)
Test your computer's security software
Windows XP, Windows Vista, Windows 7 all versions
All of you should, by now, have security software
installed - which means updated antivirus and antispyware programs. And
most of you have never seen a warning from your security software other
than many those "tracking cookies" which really aren't a threat at all.
So how do you set off the alarms to see if everything is working
correctly? You can run soft of a fire drill by installing PC Security
Test (1.5MB download, freeware, Windows XP, Vista, Seven - 32bit and
64bit) that's what you can do.
Before you run off to download and run this software
program, we want to advise those of you who use Microsoft Security
Essentials that you'll not get a warning about the "Eicar" virus. The
reason why you won't is because Eicar is well-known virus simulation
that has been around for years. MSE's engine recognizes that it's not
really a virus and issues no warning. If you're using other
antivirus software, you may get a warning. If you do that is not proof
that the other antivirus is better than MSE or that MSE is "smarter".
It's simply the difference in definitions and should not be construed to
mean anything else.
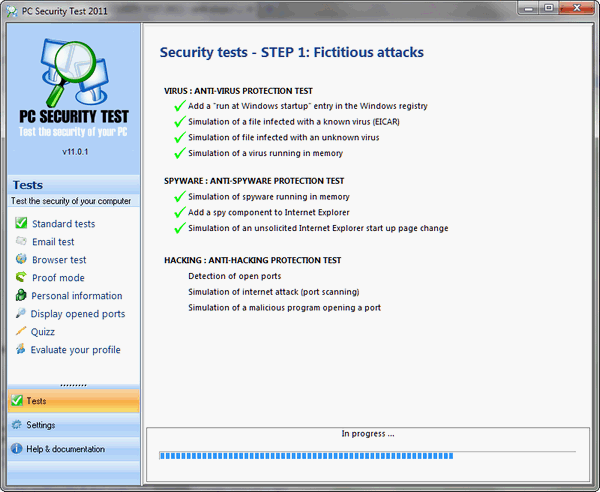
So a word from the developer and then we'll set you free
to download this small freeware program so you can see how your
computer's security software measures up.
"PC Security Test is a free program for Windows that
checks computer security against viruses, spyware and hackers. With a
few mouse clicks, users can easily control the efficiency of their
protection software (anti-virus programs, spyware scanners and
firewalls). PC Security Test simulates virus, spyware and hacking
attacks and monitors the responses of your protection software. Don't
worry, no real viruses are involved ! After the tests are complete, PC
Securtiy (sic) computes a security index and provides tips on improving
PC security."
You can read
more about and/or download PC Security Test (Freeware) from this link.
Remember any warnings you get while running the test are not threats - they
are simulations. Also keep in mind that some threats shown by this
program are worst-case. In other words, you're not likely to encounter
some of these threats. So don't panic - common sense, remember?
Zappit is now available
directly from us
Windows XP, Windows Vista, Windows 7
32bit and 64bit Systems

A couple of weeks ago we became aware that CNet was bundling
software with all their free downloads. We're sorry that CNet has
chosen to take this path. It's bad enough when a trusted site takes
advantage of that trust to make money, but the bundler CNet uses has
the bundled software pre-selected in the installer and if you're not
careful you'll install it with the program you wanted. And for every
program you didn't want but installed by mistake, CNet gets paid.
This is not only cheating you - the user, but it's cheating the
company who is paying CNet to include their program in the bundle.
If people aren't installing it willingly then they're likely to be
angry and wonder where the software came from. So they'll look at
the software and blame the company who paid CNet to bundle it. Bad
PR.
Anyway, we've been offering our software through CNet
for several years. But since we've learned of CNet's changes we've
changed all our software links on our pages so the downloads of our
programs come directly from us - not CNet.
One of the programs we often overlook, but one which we
want to feature today because it's a darn good program is Zappit - our
own Windows cleaner. It works great with Windows 7 (32 and 64 bit) as
well as with Windows XP and Windows Vista. And unlike other cleaner
programs, Zappit is safe to use. There's another cleaner program, one
which many use, that has a registry cleaner built in - and this registry
cleaner has caused many problems for many people. It's not a good
registry cleaner - in fact it can cause major problems. Zappit has no
registry cleaner but it has lot of other useful and safe features. And
it shows the actual amount of junk removed - it does not show an
inflated figure.
Yes we're tooting our own horn here, but Zappit is a
great freeware program, that's easy and safe to use. And now all our
Zappit downloads come from us - not CNet. So when you download Zappit,
that's all you get. You get nothing else.
Zappit has a safe mode that will remove all the
temporary and junk files the average user would want or need to clean.
There is also an advanced mode that gives more advanced users access to
more powerful cleaning features. So Zappit is perfect for beginners as
well as advanced users.
Zappit has some other great tools and tweaks too:
Favorites/Start Menu Manager - With the click of a button, you can sort
your Favorites alphabetically. or you can organize them manually. And,
with a click you can sort the Windows Start Menu alphabetically. Windows
Vista and Windows 7 do this automatically, so check your start menu to
see if your start menu is sorted alphabetically. Windows XP users will
find the alphabetical start menu sorter especially useful.
Schedule Wizard - Set up a schedule to perform system cleanup
automatically at a pre-determined time, using predefined settings. Set
it and forget it.
Windows Startup Manager - Makes it easy for you to take control of many
of the programs that automatically start when you start or reboot your
computer.
Program Options Dialog - by default, it is set to automatically create a
system restore point each time Zappit is used. Other user controlled
options here too!
So Zappit is more than just a junk and garbage files
cleaner. It has a lot of useful tools too. And now you can download
Zappit free directly from us - no more CNet downloads. If you're
interested in a great system cleaner with a lot of other great features,
you're welcome to read more about and/or download Zappit at
http://zappit.net/ .
A Windows tweaking tool that's a really great
tool for learning more about Windows
Windows XP, Windows Vista, Windows 7
Once in a while we'll feature a Windows tweaker program
because we know some of you like to play around with them - and
sometimes we do too. Some tweakers are powerful programs that can change
some important Windows settings and make serious changes to the Windows
registry. All this can be good or bad. Some tweaks are best used by
advanced users, because if you don't know what you're doing you can, at
worst, make some unwanted changes to your Windows system. So we're often
reluctant to recommend a really powerful tweaker like this one. We don't
like getting letters from people that say - "I downloaded that program
and now my computer has nothing but Chinese text ....".
X-Setup Pro is an extremely powerful
Windows tweaker that enables you to make over 1,900 changes to
settings that are usually hidden deeply in configuration-files and
the registry with just a click. You can use it on Windows XP, Vista, or
Seven (32 or 64 bit). It's fairly easy to use and has a friendly user
interface. You can make changes to almost every aspect of your computer.
X-Setup Pro is one of the most powerful and comprehensive tweakers
available - which means it is also one you need to use with caution.
X-Setup Pro sold for $14.95 when it
was still being sold. But alas, like so many other small Web companies,
the folks who built their hopes and dreams on their programming skills
have closed up shop. But they've been kind enough to allow everyone to
use X-Setup free. This means two things: You can get X-Setup free and
it's no longer being developed. If you download and install X-Setup
you'll notice some features are a bit dated. For instance, you'll
see settings changes for Internet Explorer 6, 7 and 8 - but not for 9.
But don't let that stop you - there are still over a thousand setting
changes you can make with X-Setup. It's still one of the most powerful
tweakers you an install.
Here's a twist. We're not recommending this program
simply as a tweaker. We're recommending it as a Windows learning tool.
Almost every settings change you can make is accompanied by a complete
description of what that change does and how a certain part of Windows
works. This program is worth downloading even if you never use it to
make a single settings change. If all you do is read the information
that accompanies each potential settings change - you'll learn a great
deal about Windows.

If you're interested in getting one of the most powerful Windows
tweakers available or if you're just interested in learning more
about the Windows you use every day you should download X-Setup Pro.
At one time you would have paid $14.95 for this program, but now you
it's free.
You can download the program from here and register it with
the free registration key posted on the download page - or if
you forgot to copy the key, use the key below:
XSA092-11TA9R-8K12YT
Wait! Before you do anything
else - Reboot!
Windows all versions
Whether you're using Windows 98 or Windows Seven one thing remains
constant: If you're having problems with your Windows computer, no
matter what they are, the first thing you should try is rebooting.
Whether you're having problems with installing a program, running a
program, opening a folder, opening a file, or your computer is
running like Granny Gertrude in a senior potato sack race, rebooting
is the first thing you should try.
Why? Because, you might spend hours trying to figure out what is
wrong and never find a thing. Before you waste time looking through
tips, tricks or Googling for the answer, you might find that
rebooting will fix whatever ails your computer.
Rebooting flushes your memory cache, reloads all Windows system
files and gives your computer a fresh start. Everything's reloaded,
memory is cleared, and that, my friends, can make a world of
difference.
So before you waste hours of time trying to figure out a problem,
save your time and the frustration of trying to find a solution to a
problem that may be solved by something as simple as restarting your
computer. We've learned this lesson the hard way, many times. We've
wasted time looking for solutions to problems that seemed to
disappear after we rebooted. And, often, in the frustration of the
moment, when you're computer seems destined for oblivion, simply
restarting it might take care of whatever was wrong. Of course, if
it the problem keeps recurring, even after you restart your
computer, you're going to have to dig down and find the source of
the problem and fix it. But save all that work for later. The first
step in troubleshooting is rebooting.
Zoom, Zoom, Zoom
Windows Vista and Windows 7 all versions
When you are browsing around your hard drive in Windows Explorer
and you're looking at folders with lots of documents, emails, or
text files, you might prefer using the "List" or "Details"
views. But, if you're looking at a folder with lots of pictures,
you'll have probably want to choose the thumbnail view so you
can preview each picture. You can choose between small, medium
and large thumbnail views for your pictures.
Beginning with Windows Vista and
continuing in Windows 7, you can change folder views on the fly.
Just use the "Views" button on the taskbar to switch between the
views available for the folder you're viewing. Remember - it's
always faster to use a shortcut when you can. So if you are
viewing a folder and want to zoom in on the icons in that folder
here is a shortcut for you: When viewing a folder using
thumbnail view, just hold own the Ctrl key and use your
mouse scroll wheel to resize them. You can go from small to
extra-large and never lift your finger off the scroll wheel.
It's pretty cool.
Here's another trick. The scroll-wheel trick also works on your
Windows desktop. If you're working on your desktop, press your
Ctrl key and hold it down and use your mouse's scroll wheel to
change the icon size from 48x48 icons to the extra-large,
Vista/Seven-style icons (256x256 photographic-quality icons).
For those of you who have a cluttered desktop full of folders,
shortcuts, and files, you can use this feature a lot to squeeze
even more stuff on your screen (and desktop). But remember that
professionals like EB have clean uncluttered desktop, slobs like
TC have cluttered desktop. Needless to say TC has the smallest
possible icons on his desktop, that's why his eyeballs are about
six inches from the monitor. Use the darn Scroll Wheel trick,
TC! Save your aging eyeballs. EB says keep your desktop clean
and look like a pro - don't be a slob like TC!
What is an ISP
All computer users
An ISP is an Internet Service Provider. In today’s
world, there aren’t many pure ISPs left – most are huge media companies
like Time Warner, Comcast, Verizon, and AT&T. An ISP is supposed to
provide you with Internet access and email. That’s what you’re paying an
ISP to provide. Just like you pay the gas company to provide you with
natural gas, or the electric company to provide you with electricity,
you pay your ISP to provide you with Internet access.
Somehow, somewhere, ISPs decided that besides providing you with
Internet access and email service they'd also provide a censoring
service – to protect you from spam. In doing so, many ISPs filter
incoming mail using not-so-sophisticated software which many times ends
up throwing the baby out with the bathwater.
Yes, we agree that spam is a problem, but a bigger problem is losing
that one important email – an order confirmation, a software
registration key, an email from a long-lost friend, an email from your
bank or credit card company, our even our InfoAve Premium newsletter.
There’s been a great shift in our society from one of taking care of
one’s own responsibilities to allowing others to do everything for us.
Of course when you stop taking care of the things you should be
responsible for and allow another to do it for you, you give up
something very important – control. Allowing your ISP to delete email
addressed to you – even if it is spam – is to give your ISP control over
what email you’ll receive. Considering that no spam filter even comes
close to being 100% accurate (most are well below 80%) giving control to
your ISP means you’re going to miss some – maybe many – important
emails.
Sure it’s a hassle to deal with spam – there’s a lot of it. But it
doesn’t take more than a few minutes to delete spam. It can take you
hours – even days to track down a good email that was deleted by your
ISP as spam. It will require writing emails to the sender, your ISP and
waiting for answers. And even worse, when an important email has been
sent to you and you weren’t expecting it - you had no idea it was
coming. If your ISP deletes it, you’ll never see it - and you'll never
look for it because you never even knew it existed. If you order
something online and you don’t get a confirming email, don’t assume the
merchant didn’t send it. If you order a software program online that
requires a registration key to be sent to you via email, don’t assume
the vendor didn’t send it. If you subscribe to a newsletter like InfoAve
Premium, and you don’t get it on Friday, don’t assume we didn’t send it.
If you’re one of the millions of people whose ISP uses spam filtering,
your first assumption should be that your ISP deleted it -- as spam.
And if you write to your ISP and they tell you that they don’t delete
email or don’t use spam filtering, take it with a grain of salt. We have
dozens of copies of letters from ISPs to customers in which the ISP lied
to their customers.
ISPs have no legal right to delete any email addressed to you – but they
do. They claim there is so much spam they need to filter email to save
money or to save server resources. But that’s just another lie. It takes
more server resources to run spam filters and to delete spam than to
just send the spam to the addressee. So why do they do it then? Because
there’s a certain segment of the population that sees spam filtering as
a service. It’s no more a service than if the U. S. Postal Service
started tossing mail addressed to you because it looked like junk mail.
Not many people would stand for the USPS trashing their mail because the
post office considered it junk. But somehow people think that ISP’s are
doing them a favor by tossing emails they THINK are spam.
If you think your ISP is doing you a favor by deleting spam for you,
think again. If your ISP uses spam filtering there is a 100% chance
you’re not getting all of your good email because no spam filter is even
close to 100% effective. When you stop taking personal responsibility
for things you should be responsible for, and you allow someone
disinterested third-party to do it for you, you aren’t always going to
be happy with the result.
As ISPs get bigger and more and more powerful, there may come a
day when ISPs will decide to provide additional “services” which will
scan your downloads for you, or “rate” the Web sites you visit for you
to "protect you" by preventing you from seeing a site that they deem
dangerous. There may come a day when ISPs monitor your connection and
prevent you from downloading songs or movies because they are trying to
“protect” you from getting into trouble for piracy. And all these things
are things ISPs are very capable of doing right now– and may well
do if people continue to want and allow others to make decisions for
them. More and more we see people who think having big brother watching
out for them is a good idea.
But all this is nothing new – it’s been done before – it’s been done a
lot. It’s called censorship. Censorship is always sold to the citizenry
as a good thing. It’s always sold as a way to protect people from what
someone else deems inappropriate or dangerous for them. And guess what?
It never has worked and it will never work.
ISPs will continue to sell customers on the advantages of spam filtering
- calling it a "service". They’ll continue to filter mail and toss good
emails out with the bad. And the only reason so many do it today is
because people let them do it. And the more you let someone do things
for you the more they will want to do.
Isn’t it time you stood up and took responsibility for your own email
and stop letting ISPs control what email you receive and what email you
don’t? If you allow you ISP to censor email addressed to you we will
guarantee you that you will never get 100% of the good email you want –
and you’ll still get some spam.
You’re paying your ISP to provide you with the best connection to the
Internet possible and email service – and that’s it. You’re not paying
them to delete email or to make choices for you. It’s time that ISPs got
out of the censorship business and started taking care of the service
for which you’re paying them.
Give it some thought.
Here's a little-known way to speed up your
Windows boot time
Windows XP,
Windows Vista and Windows 7 (all versions; 32bit and 64bit)
Every Windows user, whether they're using XP, Vista or Windows 7,
wants to speed up boot time. So, over the years, we've offered many
tips and tricks and featured many programs that can help you reduce
the amount of time it takes Windows to boot. Probably none of them
is more important than reducing the number of programs that start
with Windows. And we've told you many times to cut down on the
number of programs you allow to start with Windows - so we'll assume
you've already done that :-)
But there is another tip we've never featured. It's not a very
well-known tip, but it can help you reduce the amount of time it
takes for your version of Windows to start up.
Windows keeps a list of all the
recent items you've opened. And since we all open a lot of things, over
time the list can become very large. Every time you boot, Windows checks
that list during boot. So if that list is huge, it takes Windows longer
to check it and Windows takes longer to start up. (You should also know,
if you leave that list intact, anyone who uses your computer can see
what you've opened. Right? Right! We're just sayin'...)
Here are simple instructions for clearing the list of recently opened
items. It's different for each version of Windows..
Windows XP
Windows XP has a section of the Start menu you can see called “My Recent
Documents”. This section displays the last 15 documents that you've
opened. But the real number of recently opened documents that XP keeps
can be much larger than the 15 items you can see. Here's how to clear
that list and hopefully improve your Windows boot time:
1. Click the Start button
2. Click Run
3. Type “recent” into the box (no quotes please) and then click OK.
4. When the folder has opened, you can delete all or some of the items
in that list.
Windows Vista and Windows 7
In Vista, the start menu no longer displays recent documents. In Windows
7, recently used items show in Jumplists.
Here's how to view and clean that list in Vista:
1. Click the Start button
2. Enter shell:recent into the Start Search box (notice there are no
spaces between shell:recent )
3. In the list that appears, click on shell:recent
4. When the folder opens, delete any (or all) items you wish.
Do you have a tip or trick to share, or something
you'd like us to research?
Let us know!
About screen shots
A Screen Shot is an adult
drink. You take one oz. of tequila, one oz. of Scotch, one oz. of
Vermouth, four oz. of cheap beer, four large prunes, a tomatillo and a
cup of ice. Place all the ingredients in a blender and blend for 8
minutes and 19 seconds. After blending, let mixture stand for at least 2
hours before consuming. Warning: Make sure you're sitting down before
you drink this mixture. Do not drive or operate machinery while
drinking. Make sure a bathroom is nearby. DO NOT DRINK NEAR FIRE OR
FLAMES!
Oh, just kidding. You knew that. A screen shot is an image taken from a
computer screen. It can be the whole screen or just a part of the
screen. Normally, screen shots are used to provide help for computer
users and illustrate a program's functions. Sometimes multiple screen
shots are used in creating tutorials. A picture is worth a thousand
words, so they say.
You can make a screen shot right now, without downloading an image
editor or anything else. Press your Prnt Screen key (it's up there near
the top-left of your keyboard -usually). Do it! Now click Start/Run and
type in MSPAINT (just like that). When Paint opens, click "Edit" then
"Paste". Now click "File", "Save as" (give your file a name), use the
drop down arrow to choose JPG format (this keeps your image smaller in
KB) and save it. That's all there is to making a screen shot. Yes, we
know you can use other things besides Paint to make screen shots and
most of them work better with more options and yada, yada, yada. We're
just helping neophytes make screen shots without stopping to download
Mr. Greenies' Screen Shot Wonder Macheeny ..ya know?
 Available
now at our Donation Station!
USB
2.0 Expandable Memory Card Reader
SUPPORTS 10 Different kinds of Memory Cards!
This high-quality USB 2.0 Expandable USB Flash Memory Card
Reader Pen Drive allows you to flexibly transform your supported
flash memory card to a portable pen/flash drive. Use it to read your
camera's SD card if you don't have a SD card slot on your
computer... you won't have to hook up your camera to transfer
pictures from your SD card. Use it to transfer data from any device
using a memory card to your computer!
Slide your SD/MMC/Mini
SD/RS MMC/T-flash memory card into this expandable pen drive and
transfer your data or photos to your computer without cables. This
expandable pen drive allows you to turn any memory card into a USB
flash drive in seconds!
Specifications:
-
Supports SD, MMC, MMC II, RS MMC, Ultra II SD,
Extreme SD, Extreme II SD, Mini SD, MMC Micro, and T-Flash
-
LED indicator lights
-
Transform supported flash memory card to a
portable USB flash drive.
-
Hot swappable (Swap memory cards without
unplugging from the computer.)
-
Change to a different flash memory card at
anytime
-
High-speed USB 2.0 supported
-
Use it to read your camera's SD card if you
don't have a SD card slot on your computer. Then you don't have
to hook up your camera to transfer pictures from your SD card.
Computer has no card reader? No problem. Put your
camera's flash memory card into this USB flash drive/Card Reader and
plug it into any open USB slot on your computer! Or use your flash
memory card as a USB Flash Drive! Use it to transfer data from any
memory card to your computer in a flash!
Get
your USB 2.0 Expandable USB Flash/Pen Drive with SD/MMC Card Reader
Pen Drive today!
|
Our software
recommendations |
- Our
new #1 choice in registry cleaners and optimizer. Easy and safe.
It's a winner. Save
$20 on
Registry Commander right now - or get more information about
Registry Commander here. New! Use your license on 2
computers!
SUPERAntiSpyware
Superior antispyware protection - lifetime
license - on sale now! Now our #1 choice for antispyware
protection.
Captain
Optimizer - Save $20 on the program that won our
best new software of 2010 award! Use your license on two
computers!
Read
more here.
You on
the Wind
Imagine the day is passing slowly and you look out of a window and
see the bright blue sky melting into the pale blue of the horizon then
disappearing into a horizon of haze. And imagine the feel of tall thick
grass on your bare feet and the smell of autumn all around. Now suppose
you looked at the old tree that sits in the yard in front of your place,
the one you've seen a thousand times, the one you've never really seen.
And for some reason today you see it, you see its very soul. You see the
stiff, brittle branches and tired curled leaves of early autumn, the
ones yearning to turn into leaves of orange or red or yellow. The ones
now longing for color and sleep. The ones tired from the long summer of
reaching up and touching the sun and being seared by its heat. Suppose
you could feel them longing for the cool days and cold nights of autumn;
imagine you can almost hear their begging to be released, to fall softly
on the ground and sleep forever in the grass and then disappear in an
awful howling wind that belongs to some dark and cold December night.
Imagine it's just another October, just another one in a lifetime of
Octobers all the same and all different...
Read
the rest of this essay here.
|
This
week's freeware pick |
WinPatrol 2011
A great Windows system monitor, system utility and security tool - all
in one
Works with Windows XP, Vista, Seven (32bit/64bit)
803KB download file size
Which would you rather have at your house? The highway
patrol, the border patrol, or WinPatrol? If you answered highway patrol
or border patrol, are you reading the right newsletter? You said
WinPatrol didn't you? Even if you didn't know what it was, you knew it
was a better choice than the others. Good! We're getting somewhere!
Let's see. We've featured WinPatrol three times before. And, we're
featuring it again today. Why? Because version 2011 of WinPatrol is the
best ever - it's optimized for Windows 7 (32bit and 64bit) but it also
plays nicely with Windows XP and Vista too. WinPatrol is one of the most
outstanding programs of its kind - it's really one-of-a-kind, and we
think that WinPatrol is a tool that should be on everyone's computer -
and that includes yours.
Why should it be on everyone's computer? It's simple. Because it
performs a number of useful functions that are important. And sure, you
might be able to do some of these functions by following some
technophile's long, arcane, geekspeak-filled tutorials, but what would
take you literally hours to do, WinPatrol can do for you in seconds even
nanoseconds, right EB? Time me...how many nanoseconds? Really? Ten?
Great!
The features of WinPatrol 2011 are just short of amazing (well maybe not
even just short - they are amazing!). We particularly like the "Hidden
Files" feature. No, these are not the same "hidden files and folders"
that you can view with Windows. These are super-hidden files, files you
wouldn't normally know existed, unless you're some sort of geeky wizard
with a master's degree in geekotech. Which none of us reading this (or
writing this) are. Are we? NO!
They (whoever 'they' are) say that a picture is worth a thousand words.
If that were so then this newsletter would just be six or seven pictures
and you folks wouldn't be writing about how long this newsletter is.
Just a few pictures. Sounds interesting. Maybe I will try that. Not!
Wait! Yes I know I'm rambling again...let me get back to WinPatrol.
In this case, a picture is worth at least two-hundred words. Take a
look.

That, dear friends, is a screen shot of WinPatrol 2011. As you view the
information below, glance back up here, and you'll see how easy this
program is to figure out and use.
- Startup Programs. A basic foundation for great computer performance is
reigning in and controlling the number of programs that start with
Windows. If your computer is running slow, you have programs that crash,
your computer freezes, or you have unexplained error messages which
constantly harass you while you are using your computer: It could be
adware or spyware, or too many programs starting with Windows (or all
three) and burning up all your computer's resources before the horse
even gets out of the gate. Control the programs starting with Windows
and - you'll have more control over your computer - and your computer's
performance will improve! WinPatrol makes it snap to control programs
which are starting with Windows. In fact, WinPatrol, does this better
and easier than any other program we've ever tried.
- Services are one of the most misunderstood aspects of Windows XP.
Services are programs, folks. And not only are they programs, but
they're programs which start with Windows. Getting the picture? Don't
let the moniker "Services" throw you. Services are programs, they use
memory, and the ones that are running in the background are burning
memory. But wait! Some services are necessary for Windows to work? Which
are necessary and which are not. Let WinPatrol help you decide.
- IE Helpers - better known as "Browser Helper Objects". These things
have become much maligned because many are, in fact, spyware/adware
applications running as Browser Help Objects or "IE Helpers". But many
BHO's are helpful, some are great tools, and some are baddies that ruin
your computer. WinPatrol lets you peer into the arcane realm of BHO's
and gives you insight into which ones you have installed. It's a good
place to check for spyware/adware too. WinPatrol makes it easy to see
what's going on.
WinPatrol has many other helpful and useful features. Don't believe me
huh? Look up! Look at that toolbar array! How much more do you want? You
want ice and water too? Really? Seriously, anything, any tip or trick,
any program, any utility that makes using your computer better, easier,
faster, safer and quicker is good. Right? WinPatrol does all of those
things and more.
Best of all WinPatrol's free version is not crippled and useless. It's
functional and a pleasure to use. You shouldn't be with out it. We
shouldn't be without it - and we're not. We have it! And you should too!
Are you getting the point yet?
And besides all of the above, WinPatrol's creator, Bill P. is a stand-up
guy. He's not running some huge corporate giant with little cogs
churning out software applications by the dozens. Plus, Scotty,
WinPatrol's mascot, is a clever little doggie indeed. Wait 'til you meet
him!
Bill wants to speak, he's the developer, so we must let him write a
little blurb about his program, right?
"You don't have to be doing anything wrong on the Internet to become
a casualty of malware. WinPatrol takes snapshot of your critical system
resources and alerts you to any changes that may occur without your
knowledge. WinPatrol was the pioneer in using a heuristic behavioral
approach to detecting Zero-Day attacks and violations of your computing
environment. WinPatrol continues to be the most powerful system monitor
for its small memory footprint.
WinPatrol's easy tabbed interface allows you to explore deep inside your
computer without having to be a computer expert. A one-time investment
in WinPatrol PLUS provides a unique experience you won't find in any
other software..."
Thank you, Bill!
So back to the business at hand --
You can get WinPatrol's free version (and learn more about it) by
visiting this page. Once you try
WinPatrol 2011, you'll wonder
what you ever did without it. And once you've used it for a while you'll
quickly see why it's one program we always have on all our computers and
one of our top-ten freeware picks of all time.
Who in the world doesn't like WinPatrol?
WonderHowTo
OK here's the truth. Nothing but the truth. The whole truth. The other
day EB called me. I had told her about a good wine I'd found. It was a
2003 Chateau du Ox - an deep red wine with a tantalizing thrush. It has
brilliant finish of dried fish and googoo root. Well, EB isn't very
cultured. She's not an oenophile. Anyway ... she called me and wanted to
know how in the heck to open the wine bottle. Every bottle of wine she'd
ever had in her life had a screw-off cap. She's been drinking Boone's
Farm Apple since she was 14 - but don't tell her family. She used to go
out behind the shed with her friends and drink wine and smoke fish. Now
you can see what a good influence I've been for her.
Anyway, when she called about how open the wine bottle (it had a cork),
I told her "use a corkscrew". She said, "a what?" I knew I was in
trouble. I told her to buy a corkscrew - corkscrews come with
instructions. She said she wasn't going to buy a corkscrew just for one
bottle of wine - she's been drinking Boone's since she was a girl and
she's not going to change now. Well, I was perplexed but determined. I
wanted her to taste the Chateau du Ox; I wanted her to experience some
culture. But she refused to buy a corkscrew.
With the internet at my disposal I resolved to find a way to open a
bottle of wine without a corkscrew (and I don't mean the kind of wine in
bottles with screw-off caps). You're laughing at me! So, smarty, how do
you open a bottle of wine without a corkscrew? I know the answer. I know
the answer because I found our site of the week. And it's a literal
treasure chest of interesting how-to-do-stuff videos that will delight
and mesmerize you - and I'm not waxing in wild hyperbole either.
Besides teaching you how to remove a cork from a bottle of wine without
a corkscrew, you can learn:
How do use a Mason jar with a blender - good for that homebrew
How to prevent social networking sites from tracking you
How to build a self-watering greenhouse (don't ask!)
How to make your laptop theft-proof
How to craft a ferocious origami eagle
Oh there's so much stuff and so little space to tell you about it. Each
"How to" is a video so you can see how to do whatever it is you want to
do. Opening that wine bottle only requires a wall and a towel. EB is
back to the Boone's.
Enough of this! Let's bring in the developers of "WonderHowTo.com" to
tell you about their marvelous site - which is our marvelous site of the
week pick too!
"We launched WonderHowTo in January 2008. With professional
backgrounds in television programming, software development, motion
graphics, and textile design, our team loves contributing to,
interacting with, and organizing the disparate voices who create
downright wonderful tutorials and unselfishly share their idiosyncratic
knowledge with...the rest of us.
Initially we focused on searching, curating, & indexing every single
great video tutorial on the web as the Co-Founders had come from
television. But within a short period of time, we allowed members to
contribute original articles, recognizing that some topics are better
read than viewed. Last year, acknowledging the need to offer our most
energetic creators the ability to seamlessly, show off and communicate
with other members of WonderHowTo, we created the Worlds platform.
Human curation remains central to our relentless focus on quality. In
the past year, because we marvel at the mindbending innovation endemic
to the How-To space, our front page has evolved from showcasing the best
How-To of the day, to (now) systematically reporting the real time news
events of all things DIY.
Today, WonderHowTo provides more than 170,000 how-to videos & articles
from more than 17,000 specialized creators, spanning 35 vertical
categories and 424 sub-categories. Our strategy for growth is to empower
our intellectually-curious community..."
So, find out how to do things
you always wanted to know how to do and how to do things you never
wanted to learn how to do.
Visit our site pick "WonderHowTo.com" and learn how to do what
you always or never wanted to do.
No. We are not endorsing any brand or type of wine. We are not endorsing
drinking. We are not endorsing Mason jars. We are not endorsing
anything!
Twitter, InfoAve Daily and Facebook
We've been very active on our Twitter and Facebook pages recently.
You can follow us on
Twitter here.
Also
we've got a new daily tips and tricks newsletter that we send every
weekday afternoon around 7PM Eastern time. It's free and you can
sign up for it at
http://thundercloud.net/start/subscribe.htm. It's a great way to
review some of our best tips from all the past issues of our
newsletters.
We like you! And we'd like you to like us on
Facebook. We're not too proud to beg! Walmart has more friends than
us! We gotta do better! Cloudie is hurt.
Please take a second and "like us" on Facebook by
clicking on Cloudie. You won't hurt him. He's ticklish! He likes it.
Love Cloudie and love us too. Don't just like us on
Facebook - Love us! We love you :-)
FCC Chairman Proposes Replacing USF with "Connect America" Fund
FCC Chairman Julius Genachowski outlined a "Connect America" plan to
reform and modernize the Universal Service Fund (USF) and Intercarrier
Compensation (ICC) system with the goal of expanding broadband
infrastructure and extending mobile broadband to areas of the country
where it is not currently available.
The plan calls for transitioning the $4.5 billion annual USF into the
new Connect America Fund, which would have two core goals:
(1) Ensuring universal availability of robust, scalable, affordable
broadband to homes, businesses and anchor institutions in unserved
areas. The Connect America Fund would begin near-term build-out to
hundreds of thousands of consumers in 2012, and would ultimately help
get broadband to the 18 million Americans who can't get it today.
(2) Ensuring universal availability of affordable mobile broadband
through a new Mobility Fund, which would be part of the Connect America
Fund. Deployment of state-of-the-art mobile broadband would be extended
to more than 100,000 road miles where Americans live, work, and travel.
In addition to a one-time shot-in-the-arm effort to accelerate
deployment of 4G networks in 2012, this Fund would provide significant
ongoing support for rural mobile broadband.
Continue reading...
What's next for Apple?
Steve Jobs, high-tech's brightest star for more than a
quarter century, left Apple in better shape than nearly any other
American company: flush with cash, rolling in revenue, the envy of
innovators everywhere.
So how can Apple possibly replace a cultural figure that Google
Executive Chairman Eric Schmidt once called the best CEO of the past 50
years? That is likely to be a popular parlor game in Silicon Valley for
the foreseeable future.
"The job calls for a world-class leader, requiring vision, creativity
..."
Continue reading...
Important Links:
Submit your questions, comments, and suggestions for possible
inclusion in our newsletters here. This form is for
questions, comments and suggestions for this newsletter, not for
product support, stationery questions, or general questions
concerning our products or services.
Submit your Windows
tips and tricks here.
Send us your
suggestions and recommendation for future freeware picks and/or
sites of the week.
Follow us on Twitter
Visit this page
if you're having problems getting our newsletter - or if you
think your ISP is blocking, censoring or deleting this
newsletter.
If
you need help with one of our software programs, have a question
about an order, or have a question about any of our email
stationery, screen savers, or other products - please don't use
our InfoAve Questions/Answers/Tips form.
Please
use our general Cloudeight support form
instead.
Recommended security applications
Microsoft Security Essentials version 2 - excellent anti-virus
protection. Free and easy to use - easy on resources.
AVAST Anti-Virus (free version for personal/home use - updated
to Version 5) AVAST continues to offer and support their free
version.
AntiVir (free personal version available) now compatible with
Windows Vista and Windows 7.
NEVER
INSTALL MORE THAN ONE ANTIVIRUS PROGRAM!
No
anti-virus can protect you if you do not keep it updated. Update
your anti-virus at least twice a week or more. Install and use only
one anti-virus program. Installing two does not give you twice the
protection. On the contrary, installing two could result in reduced
protection and many computer problems.
Also,
it's very important that you keep your Windows updated with the
latest patches, fixes, and updates. If you don't have Automatic
Update turned on, you should consider turning on Windows updates -
at least to notify you when updates are available. You can still
choose when to install them, not install them or install them
automatically. If you don't install Windows updates you could be
leaving yourself vulnerable to emerging threats. We highly recommend
you install all Windows updates as soon as they become available.
Recommended anti-spyware programs
(install two anti-spyware
programs for the best protection)
SUPERAntiSpyware
Superior antispyware protection - lifetime license -
on sale
now! Use your license on two computers - it costs less than
$12.50 per computer for a lifetime of spyware/malware protection.
Pay once - never pay again. SUPERAntiSpyware is our #1 choice for
antispyware protection.
Recommended firewall
We do
not recommend any third-party firewalls. We do recommend you use the
Windows Firewall and leave it turned on.
Other
recommended programs
These programs can help protect you
and your computer in other ways than anti-spyware/anti-virus
programs.
Malwarebytes
(free version - no real-time protection - but very useful anyway.
Malwarebytes (Pro version) - includes real-time protection -
lifetime license.
Always
keep your common sense with you when you're on the Internet. Don't
be lured into installing free software or signing up for a free
service if it seems too good to be true. Research it - google it!
Read the privacy policy and/or Terms of Service or License Agreement
of any free software or free service you're considering. As a rule
of thumb, free products and free services which have extremely long,
difficult-to-understand agreements are most often deceptive in
nature. Be careful and stay informed - you'll be just fine. The
internet is the greatest source of information ever - and it's all
right at your fingertips. And despite all the nonsense and
misanthropes that hide in the shadows, the Web is a wonderful place.
Play it safe, use common sense, and enjoy all the internet has to
offer.

Visit Our Donation Station
Padded neoprene USB Flash Drive Holder Key Chain
USB 2.0 Flash drive/Memory Card reader - supports 10 different
kinds of flash memory cards
HubbaMan 4-port USB hubs
USB Wristband Flash Drives
4GB ReadyBoost Flash Drives
6-pocket USB flash drive/SD card holders
Donate Any Amount
- Donate any amount no matter how
small and choose a registered version of FolderMagic,
CalendarPal, or Smileycons. Any amount no matter how small helps
- and you can choose your gift just for helping us
If you can help us right now, we'd really appreciate
it. But we know that many of you are having problems as well with
the world economy being what it is. If you can't afford to help us
financially, you can help us by
using our Start Page.
Our Start Page now
has over 100 free games you can play, plus breaking news and daily
tips and tricks. It costs nothing to use our Start Page - and you
don't even have to register.
Use our Start Page
as your start page and you'll be helping us without spending a dime
InfoAve Daily
Tips & Tricks
We're offering something we think most of you will
enjoy. We're offering a daily tips and tricks summary newsletter
that is sent everyday. It's a summary of daily tips, freeware picks,
and site picks - so it's very brief and lightweight. If you'd like
to receive or daily tips and tricks newsletter (completely free, of
course) you
can subscribe here.
Don't forget... you can also help us by using our
Start Page. We have
added over 100 free games to our Start Page. It costs you nothing to
use our Start Page
--and helps us a lot.
Don't forget all Cloudeight subscribers save 15% on Reimage - for a
limited time only!
Thank you very much for
subscribing to InfoAve Premium. We appreciate your help and your
support very much.
Have a great weekend!
Eightball & Thundercloud
Cloudeight InfoAve Premium Edition Issue # 416
Volume 9 Number 1
October 7, 2011
IMPORTANT DISCLAIMER
ABOUT SOFTWARE RECOMMENDED IN THIS NEWSLETTER
All software recommendations we make in this
newsletter are based on our own experience and testing of the
programs that we recommend. This does NOT guarantee they will
work on YOUR computer. We assume you will read the program
documentation and use the program according to the instructions.
We make no guarantees about any program recommended in this
newsletter or its suitability for any particular purpose. We
will not be responsible for any problems you may have. We do not
and cannot provide support for any products other than our own
Cloudeight products and we will not answer email concerning any
product which is not a Cloudeight product. We urge you to use
good judgment when downloading and installing software and to
use a program only after reading the program's documentation.
And, all Tips & Tricks in this newsletter have been tested by us
on several different computers and were found to work as
indicated. They may not work on yours. We make no guarantees.
Anything we recommend you try and use at your own risk. We will
not be responsible for any problems caused by any software
programs recommended in this newsletter or any of the tips and
tricks in this newsletter.
Readers' comments are their
own and Cloudeight Internet LLC is not responsible for comments
of our readers. All readers' comments, suggestions, questions,
and tips and tricks sent to us become the property of Cloudeight
Internet LLC. You understand that we may use your comments
without your explicit permission.
InfoAve Premium is published by:
Cloudeight Internet LLC
PO BOX 73
Middleville, Michigan
USA 49353-0073
This newsletter is sent from the address
infoave-premium/@/pr1.netatlantic.com . The IP address for
Netatlantic is 69.25.194.2. Netatlantic is a respected newsletter
hosting service. We have used their services for many years. All
content is copyright ©2011 by Cloudeight Internet LLC (all rights
reserved). |