|
Cloudeight InfoAve Premium
September 9, 2011
Issue # 412
Volume 8 Number 49
Dear friends,
Welcome to InfoAve Premium, Issue # 412 - We're
glad to have you with us. Thank you so much for subscribing to
this newsletter and for all your support and kind words. We
appreciate it very much!
THANK YOU VERY MUCH
We are very grateful for all the help and
donations you've given us. Your support helps to keep our small business afloat
in these difficult times. We both are sincerely thankful for
your kindness and generosity. We don't know what we'd do with
you! In times like these you discover the best in people. We are
overwhelmed by your response; we can't thank you enough for your
support. Our promise to you is that week after week we'll give
you the best we have.
Thank you!
Can you help?
Times are still difficult for us. If you can
help us right now by making a donation, we'd very much
appreciate. We do realize that many of you are having a tough time right now too.
But if you are able to help us get through a very difficult
time, we'd be very grateful. We
continue to work as hard as we can to provide you with the very
best computer newsletter on the Web - and your support and
encouragement has helped us immeasurably. We've cut our expenses
as far as we can and still keep things going. Many of you have
helped us many times and we appreciate it. If you are able to,
this week, please consider visiting our Donation Station and
making a donation. We have some very nice gifts available for
various donation amounts. We have a "donate any amount" feature
- where you can donate any amount you like - even the smallest
donations are greatly appreciated. We really need your help
again this weekend. Thanks so much!
Special Announcement! We have 100 registration keys to give
away!
We have 100 keys for Aplus Screen Recorder we will be giving away
this weekend (until they're gone). APlus Screen Recorder
is an easy-to-use tool for creating software demonstrations, website
helps, user training movies, or video tutorials by capturing screen
activity from the windows desktop and turning the captured images
into standard AVI movies as EXE files that you can play on any PC.
Learn
more about Aplus Screen Recorder.
This program normally sells for $29.95. We have 100 registration
keys to give away. We will give a key to anyone who makes a donation
until the keys are gone.
Visit
our Donation Station, chose any of our gifts, make a
donation, and we'll send you a free registration key for Aplus
Screen Recorder in addition to the gift you chose. It's a great deal
for you! So please help us this weekend and we'll give you an extra
gift! Offer valid until the 100 keys are gone!

All items available from our
donation station come with FREE shipping anywhere in the world!
And this weekend, every donation, no matter how small, qualifies
you for a free registration key for APlus Screen Recorder - a
$29.95 retail value.
 Now
at our Donation Station! Now
at our Donation Station!
Carry and protect up to six
camera/digital media cards! Slimline, protective case
holds up to six memory cards including SD, Memory Stick®
Smart Media® and Micro SD. Faux Leather Black case has
strap on the back so you can connect it to your camera
strap, camera bag, belt, etc. Includes a 25 year
warranty by CaseLogic. FREE SHIPPING ANYWHERE!
Learn more and/or donate here.
Now At our Donation Station!
 Wireless Laptop Optical Scroll Mouse Wireless Laptop Optical Scroll Mouse
This high-quality Wireless Laptop Optical Scroll Mouse
features a foldable USB receiver so you can safely take this
mouse anywhere! Sleek, compact design for netbooks and laptops.
This mouse is wireless so there are no messy cords or cables to
get tangled. Great for travel or at home. This mouse also works
great with your desktop computer too!
Features:
-
3-button + scroll wheel
-
Operates on 2 x AA batteries, included
-
Color: Black, White or Blue
-
Includes foldable USB receiver
-
Learn more and/or donate now!
If you need to change your
newsletter subscription address please see "Manage your
subscription" at the bottom of this newsletter.
We hope you enjoy this issue of InfoAve Premium!
Thanks again for subscribing.
We thank you all for your
generous support.
A comment from Daniel
I wanted to commend you two on the great job you do with this
newsletter. There isn't a week that goes by that you don't hit
the nail on the head with something in your newsletter. Last
week, it was like you were reading my mind. Several of your tips
seemed like they written for me. It happens a lot. I think yours
is the best computer newsletter around, and I for one appreciate
all your do. Although things are a little down here, I made a
donation last week, it wasn't much but I hope it helps you.
Thanks to both of you.
Thanks so much for your support and your kind words, Daniel.
Every donation, regardless of the amount helps us greatly. We
very much appreciate it.
TC & EB
A comment from John
Hi TC & EB. Cluttered desktops is a subject which you
address from time to time with programmes to create an 'orderly'
desktop. I have been using a little 'trick' for many years, and
all I have on the main desktop is one icon. Right click anywhere
on the main screen, go to 'New' then 'Folder', top of the list.
I named the folder 'Second Desktop'. Drag and drop all the icons
into the new folder and find a nice, quiet parking place for it.
Double click the new folder and there, in alphabetical order are
the icons, in alphabetical order. From the 'Organize' menu the
layout can be arranged to suit personal preferences.
Kind regards,
John in Oz.
Thanks for sharing your tip for a cleaner
desktop. John. From the desktops we've seen in our time
(including our own sometimes), ideas for keeping the desktop
more orderly should be welcomed by many! Thanks again, TC & EB
A comment from Carol
I wish to extend to you and to the person suggesting the USB
bracelet being used as a medical bracelet my heartfelt thank
you. I can now discard the several sheets of paper I carry
around with me. All my medical alerts are in one place and easy
to access by medical professionals. I just had to use a
permanent marker to put the "Medical Alert" on the bracelet. I
appreciate so much all of the help you have provided with your
newsletters. Carol
Thank you so much for your support and your kind remarks.
We thought it was great idea and a really good way to use one of
the USB bracelets we have on our donation station. Thanks again,
Carol. TC & EB
A comment from LE
I wish I knew how much you made every time someone Googled on
your homepage (your homepage is my home page). I am a lifetime
subscriber to everything you have offered "lifetime" to. I click
on as many ads I can before logging into NOTH. I Google anything
and everything, all day long. My "ieSpell" quit. It is there I
just can't assess it in "tools" any more.... well... if I need
to check the spelling of a word I google it from your home page.
And if I spelled it wrong Google says: "did you mean..." ...yes
I did. I used to have a lot of cook books they are gone..... I
do a lot of gardening, and I don't bother looking in the garden
books... "Google"... I do a lot of research, and your home page
"Google" almost over-heats... I am almost not making it
myself... I'm behind on a lot. Thank Heaven, I no longer have a
mortgage or I would have lost the house... I am slowly acquiring
the paid "recommended security applications" you recommend. But
I do Google all day long and it is only from your homepage. And
if anyone else uses my computer they are not allowed to Google
from any other place than your home page. Also nothing gets
downloaded on my computer unless it is "highly" recommended by
you (suggestion of the week, etc). What else can we do with your
home page to make money for you. I have been a subscriber since
the mid 90's. Thank you, and don't worry about your "shadows"
you both are our angels of the internet. Karma owes you... you
both owe nothing to Karma nor the Universe, any and all mild
transgressions that either of you could possibly have committed
have been paid back tenfold. Bless you both, and thank you
again. L E
Thank you very much for writing, for your
support, and for your help. We don't know how much we make per
search from our start page - a few pennies at most, but
thousands of searches times a few pennies adds up. As for
your ieSpell, keep reading this newsletter and you'll find we
have another spell checker for IE you might like. The economic
recovery we had all hoped would come, never really came, and
many are barely getting by. And we sure do understand that.
While most of our congress is made up of multi-millionaires who
have no idea what it's like to live from paycheck to paycheck,
we are not millionaires and we do understand how really bad
things are for most of us in the disappearing middle-class.
You're helping us by all you are doing and we hope others who
are having hard times financially will join you in using the
Google search on our Start Page. It helps us and the Google
search form there works like other Google searches. Thanks again
for all you do to help us. TC & EB
Your comments are always welcome!
 Available
this
week from our Donation Station
Padded Neoprene USB Flash Drive Holders with Key Ring
Keep your flash drives handy and safe from
damage with one of our Neoprene Padded USB flash drive holders
with a convenient key ring.
These padded flash drive holders are made from
durable, high-quality neoprene. They'll keep your data safe and
handy.
-
Expandable neoprene case stores 2 USB Flash
drives in separate pockets; padding protects drives too!
-
Metal Key Ring included so you can attach to
keys, laptop case, lanyards, backpacks. Never misplace a USB
drive again!
-
Dimensions 4.75" x 1.75" x 0.5"
Get more information here!
Your donations are very much appreciated. Thank
you!
Teresa asks about PCMatic - As Seen on TV
What do you know about PCMatic.com? I keep seeing it advertised
on TV and it sounds like a great program but I am always afraid
of things that sound too good to be true.
Our answer
We've not seen PC Matic's TV commercials on TV. Our first
reaction was to dismiss it offhand because most such "miracle
and magical" computer optimization products advertised on TV are
scams - MyCleanPC, FinallyFast, etc.
Dutifully we decided to look into PC Matic to see who makes it.
We were surprised to find that it is made by PC Pitstop,
generally a site we respect. With that being said, the promises
made by the program seem improbable - plus it's a suite of tools
designed to do everything under the sun, and it's price tag is
$49.95 which is a bit steep considering most of what it claims
to do can be done with freeware or other programs selling for
substantially less.
PC Pitstop says:
"PC Matic is an easy to use application that performs critical
computer maintenance with a click of a button. PC Matic will
remove and keep Malware at bay while boosting internet and
system performance. The new Active Malware Protection stops
Viruses, Spyware, Worms, Trojan Horses, Rootkits, Bots,
Keyloggers, Adware, and many other forms of Malware. Eliminate
lockups and computer crashes with PC Matic's advance registry
cleaning and patent pending Driver Matic automatic driver update
technology. Keep files safe, PC Matic now includes PC Pitstop's
new DAT1 backup software which provides 2GB of free secure
online backup and unlimited local backup. PC Matic Cloud based
scheduler makes it easy to keep multiple computers running like
new. You will never again have to run multiple programs to
maximize the performance, stability and security of your system.
With just one click, PC Matic will make sure your PC always runs
like new."
It makes some pretty heady claims, which sound too much like marketing
hype to us. There isn't a software program made that can keep
your PC always running like new, unless of course you never
install and uninstall software - and rarely use your computer.
Another concern: PC Matic says it is an antivirus, but we've never seen any independent lab
tests of its antivirus. In our opinion, trusting your computer
to an off-brand antivirus would be risky - we don't see PCMatic
listed as a top choice antivirus program anywhere. And nowhere
could we find out if you do install this product if its
antivirus component is one of those rare ones that runs
alongside of your regular antivirus or whether you'd need to
uninstall your current antivirus program.
We didn't test the program because the trial version is a scan
only - nothing is repaired. As with most such products, we'd
expect to see hundreds of errors which would be instantly
corrected as soon as we paid $50. It wasn't worth $50 for us
to find out. As anyone who reads our newsletter knows, we're not
fans of security suites - especially security suites which claim to be jacks of
all trades - they're usually masters of none. Since PC Matic
contains antispyware, antivirus and antimalware component, it
qualifies as a security suite.
We'd advise you not to spend your money on this
program. We think you'd be disappointed and we'd be really
concerned about trusting its security programs. Security
software is something you shouldn't experiment with.
While we generally hold PC Pitstop in high regard, we cannot
recommend this program.
A question from Annie
Could you possibly help me please? I am signed in as
Administrator in my new Windows 7 computer, however I am trying
to set up my PSPX2 and I need to add the dlls...but my computer
tells me I need administrative permission? I have double checked
and I am the administrator in my User Accounts. Can you tell me
how to get my computer to accept the dlls for my 64bit please? I
use PSP a lot. You are so awesome about helping us folks. I look
forward to your response. Thank you kindly. Annie
Our answer
Thanks so much for your kind comments, Annie. Windows 7 allows
you to have an administrator account, but it really doesn't
assign you administrator privileges - you're really using a
restricted administrator account, so there are many things you
cannot do unless you elevate your privileges. You could can
create a Super Administrator account, but that would be overkill
since all you want to do is install a program that requires
administrator permissions to install all its components
A little note: DLLs are Dynamic Link Libraries. These are
normally installed by the program's installer. The DLLs are
executable (like EXEs) but can't be run directly. They hold
shared code libraries and information used and shared by one or
more programs. If you can't install DLLs when you install a program
because you don't have administrator rights, we suggest you do
this:
Reinstall PSPX2 but this time right-click on the installer and
choose "Run as administrator" from the right-click menu. This
will run the program's installer in an elevated mode with
administrative permissions. The program and its associated DLLs
should install correctly in this mode. If it doesn't, try
uninstalling it: go into Control Panel, Programs, Uninstall a
program, locate PSPX2 and uninstall it. After you done this,
reboot, and try reinstalling it by right-clicking the PSPX2
installer and choosing "Run as administrator".
We hope this helps you Annie.
Randy misses Tweak UI
I'm a new Windows 7 user - I finally moved (reluctantly)
from Windows XP. Windows 7 isn't too bad, I miss Outlook Express
though, and many things are in different places. I'm learning to
find my way around. My question is - On Windows XP I used a
program called Tweak UI which let me easily make some
modifications to Windows that I really enjoyed. But I can't find
Tweak UI for Windows 7. Do you know of any program that's easy
to use that works like Tweak UI did that works in Windows 7
64bit? Thanks for all the great information. I really enjoy
your newsletters.
Our answer
Thanks, Randy. We loved Tweak UI. It was a great program anyone could use to safely tweak Windows
and customize it to their personal tastes. When we saw your
question we thought we'd see if we could find a good replacement
for Tweak UI for Windows 7. We
got lucky. We not only found a program that does most of what
Tweak UI did in Windows XP, but does even more.
Unlike Tweak UI, which was for the most part
safe, some features of the program called "WinBubbles" (the
program's toolbar says "WinBubble")should only be used if you
really know what you're doing. It's a serious tweaking tool, but it
also has many safe-to-use and fun features such as an easy-to-use
Logon Screen changer. It also allows you to take ownership of files, add "copy to",
"move to" and more items to right click menus and much, much more. If
you use it with discretion you can make some really useful
tweaks to your computer. Better than Tweak UI? Yes. But, we
recommend you use caution when making some of the changes this
program makes so easy to do. If you're not sure what something
does, don't do it until you find out exactly what you are about
to do.
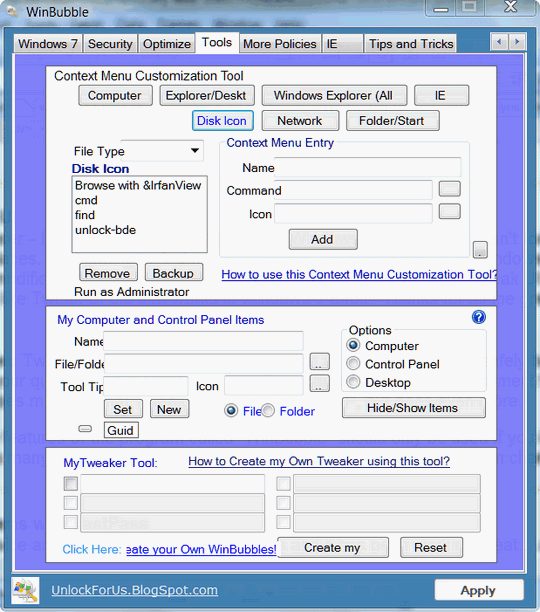
WinBubbles makes it easy to access and modify
hundreds of Windows settings. You can reset file associations,
change your screensaver, change your logon screen, tweak Windows
7 and make it your own. As with any good tweaking tool, some of
its features must be used with caution. WinBubbles has tons of
features though, which are fun and easy to understand and use.
We think it makes a great TweakUI replacement for Windows 7
since it does everything TweakUI did in Windows XP - and more. We think you'll like it.
You can learn more about and/or download WinBubble (or
WinBubbles) here.
Helen is worried because she sent a
Malwarebytes scan log as an attachment in Email
Can you tell me if I am in danger of someone stealing my
information. I sent a ddl log by email to a Malwarebytes trouble
shooter, He told me to do it as an attachment and i thought that
is what he meant. He was upset with me for doing it that way. My
question now is can someone access my CPU with this info? I am
scared to death to use my computer email. Please let me know.
Thank you, for all your help, I like many others, would not know
what to do without all your knowledge that you share.
Our answer
We're not sure what you mean by DDL log file, but we've
checked out the log file generated by Malwarebytes' scan, and
we've checked out the Windows dump file logs, and there is
nothing in those log files that would give anyone access to your
computer. Additionally you'd have to assume that your email had
been intercepted by a malcontent who thought your computer might
have something of great value on it to him or her. It's not
likely that those who sit and watch Internet traffic and attempt
to intercept email are going to be watching for email from you
to a Malwarebytes troubleshooter. There are emails being sent
from big corporations, banks, stock brokerage, large retail
establishments - millions of them, every day. It's really very
highly unlikely that someone is going to even care or notice an
email from any home computer user. But even if they did, there
is nothing in those log files that they could use to "break
into" your PC. There are no passwords or usernames in Windows
DMP files or in Malwarebytes scan logs.
It's good to be careful and it's wise to be
cautious, but we think your Malwarebytes troubleshooter is being
a little paranoid. Don't worry, Helen, we think your computer is
just as safe as it was before you sent that email with the
attachment.
Wayne needs to get rid of a rogue security
program
How can I remove a rogue program that has invaded my computer.
It calls itself Vista Home Security 2012 and it has somehow
infiltrated my windows security center with it's own firewall
and antispyware that is giving me one large headache with all
kinds of pop ups with warnings of virus attacks security
breaches which I know are not true. It wants me to buy the full
registered program before it will remove all infections it tells
me that I have. I am using Avast Antivirus at this time with
SUPERAntiSpyware lifetime user and Registry Mechanic. I have
scanted my computer with all these programs and they did not
find any problems. They are also all up to date. I have tried
using the search program as well as Revo Uninstaller and windows
uninstaller but could not find the rogue program anywhere. I am
totally frustrated. Could you please help.
Our answer
The reason the rogue is on your system is because you were
tricked into clicking on one of those Windows warning screens
that says something like "your computer is infected with blah,
blah, blah Trojan". These warnings do look very
realistic and they do trick millions into installing rogues every
day. These windows appear at random while browsing the
Web. Once you click on the link "to scan your computer"- you're
infected. And rogues escape detection by antispyware and antivirus
programs because they are neither spyware or viruses - they are
Windows programs. But they're very pernicious; they install
themselves in many places on your computer. They disable your current
antispyware and antivirus and take over Windows Security
Center and then hold your computer hostage until you pay for
license.
These rogues don't protect your computer even after you pay for
them - it's theft by deception which anywhere else but the Web
would be punishable by imprisonment.
But all that is neither here nor there as far as
you're concerned. Your computer is infected and you need to
clean out the infection. Now that you're already infected
there are two possible solutions:
1. Use System Restore to go back to a time
before you were infected. Unless you've deleted restore points,
you should have restore points going back 10-14 days. Go back to
the oldest restore point you can find and restore your computer
back to that point. The only thing you'll lose will be any
programs you have installed during that time; hopefully the
rogue was installed during that time. If you restore back to a
point before the rogue was installed, it will be just like it
never even happened.
or
2. If you don't have restore points that go back
to a time before you installed the rogue, you can try using
Malwarebytes to remove the rogue. It is the only program that
can remove most rogue security programs even after they've been
installed. The freeware version will work to remove the rogue.
Remember that the freeware version does not include "real-time" protection, so
if you use the freeware version, keep in mind that Malwarebytes will remove the
rogue but will protect you from being
infected again. The Pro version has real-time protection, the
freeware version does not. Here are the links to Malwarebytes Free and
Pro:
Malwarebytes
(free version) - no real-time protection - but very useful anyway.
Malwarebytes (Pro version) - includes real-time protection -
lifetime license.
You can protect yourself from being tricked
again by never clicking on warning dialogs that appear in your
browser while you are browsing the Web which warn you that your
computer is infected. If that happens again, don't fool around,
shut your browser down immediately by using Task Manager, going
to the browser's process and Ending the
Process of your browser. Or shut your computer down immediately
at the switch - it's better than becoming infected. Keep in mind
that if you try to close your browser normally during a rogue attack
you will (in most cases) not be able to and your computer end up
being infected.
You can't uninstall the rogue by using Control
Panel even if you see an uninstall entry in the Control Panel
for it - it's just a ruse. The above two methods are the quickest
and easiest ways to
get rid of rogue security software. You will find long and
complicated ways to remove the rogue manually, but these are
often difficult to implement and not always effective.
Danielle wants to know how to
alphabetize a list of names in MS Word
I have a list of 'my friends' in Word. I am wondering if know to
a way to arrange them in alphabetical order? I run Windows 7. I
have Microsoft Office Professional 2010. Thanks Danielle.
Our Answer
If you're working with a list of names in MS Word and you
want to sort them alphabetically just do this:
First make sure that each name is on its own line. Then...
1. Highlight all the names
2. Click Table (in the Word toolbar), then choose Sort
3. Click OK
You can use this same method with
other word processors too.
Never Reinstall Windows Again!
Reimage is one of our biggest selling featured products thanks
to you!
REIMAGE NOW WORKS ON 32bit and 64bit
Windows XP, Windows Vista, and Windows 7
There's only one
reason why Reimage has become a fast selling product: It works.
Are you looking for a permanent solution for your annoying
computer problems? Slow startup? Slow reboots? Constant Windows
error messages? Waiting forever for programs to start?
Reimage is an online PC repair tool that repairs Windows
and makes your PC run like new again, for a fraction of the
cost that places like Best Buy, Staples, and other computer
repair services charge. And Reimage guarantees it will work for
you or you get your money back!
Reimage Features and Benefits
-
Requires no setup
-
Reimage is the
ultimate professional repair tool
-
Rebuilds the
entire Windows system - without damaging your programs or
files
-
Repairs damaged
operating system
-
Refreshes native
operating system drivers
-
Save 10% off Reimage - use coupon code fixitnow10 at
checkout!
"It works like
Magic." - eWeek Magazine
Don't
spend hundreds of dollars on computer repair.
Repair Windows quickly and easily at fraction of the cost of
computer repair services like "Geek Squad".
Repair your Windows system in minutes.
Eat all you want and lose weight!
All computer users
We've all seen those commercials for miracle weight loss
products, that really don't work. The companies that make those
kinds of products know that the FDA doesn't regulate
supplements. So they market weight-loss products as supplements
and escape regulation. The can make wild claims and show fake
testimonials - and make millions of dollars in the process.
The same thing happens on the Internet. Every day some security
vendor comes out with a new ultimate defense
against...against...well against every possible danger one could
face. But the truth is - they can't. There is no regulatory
commission that prevents security companies from making wild
claims that can't be substantiated.
Take Norton, for instance. According to Norton they have the
best security software in the world. If you don't believe that,
take a look at their Web site. But what is really going on with
Norton? Norton is a product of Symantec, a huge multi-billion
dollar software conglomerate. The spend tens of millions of
dollars
convincing consumers how wonderful Norton's security products
are. But just about a year ago, they added "Lifelock"
( another
borderline scam - Lifelock was sued by the U.S. Government for
making false claims). If Norton protected you from everything
before, why did they add someone else's product to their
security suite? Marketing. It has nothing to do with protection.
It has everything to do with perception and finding new ways to
get your money.
There's another smaller company out there who sells security
software. We're not going to mention their name, but they make a
security suite which contains a firewall. They make wild claims
how their firewall can protect you from identity theft, but it
can do no such thing. They know that no one is going to prove
them wrong. They know that no one is regulating their claims.
They can say anything they want (unless they say something about
Social Security numbers and how you can paint your Social
Security number on the side of your car and they can protect you
--- then the Feds will step in).
There is more money wasted on security software (it's a
multi-billion-dollar business) than on any other kind of
software. The truth is that you can protect your computer just
as well without spending a dime. And you can believe that or
not, but the old adage that "you get what you pay for" simply
doesn't hold true when it comes to security software.
As most of you know, we're small business and we're struggling
right now. We could be making thousands of much-needed dollars
by hawking $60 security programs in our newsletters and making
50% to 60% commission on them. We could deceive our readers and
make money from that deception, but we'd rather go belly-up than
to make money from lies, deceit and half-truths. It's too bad
security vendors don't have the same ethics, isn't it.
The truth is, there isn't a single reason why you need to pay
for a security suite for your computer. Not a singe valid reason
in this world why you'd need to buy a security suite. There's no
reason at all why you'd need to pay for things you don't need -
like a 3rd-party firewall. Or pay for an antivirus program when
their are free antivirus programs that work as well or better -
and it's been proven time and again by independent tests. Yet,
we're betting that 25% of you are still paying an annual
subscription for an antivirus or security suite.
Many of you purchased computers in the last or two or three
years. And we know that 99% of all new computers come with
either Norton or McAfee installed on them. Norton and McAfee
know that if their products are on new computers, purchasers
will assume that the computer manufacturers put the best
software on their new computers. That's laughable but
understandable. Dell, HP, Toshiba, Lenovo, Acer, Asus and the
rest, are out to up their profit margins on new PCs and laptops.
Margins are small in the computer industry and competition is
fierce. Computer makers are looking every possible way to
increase their profits on each new PC or laptop sold and
Norton/McAfee are happy to pay to have their software installed.
They know that a substantial percentage of computer users will
pay the yearly subscription fee of $49, $59 or $69 every year,
because they simply don't know that there are better products
available free.
Those of you who are reading this don't represent the majority
of computer users. You've taken the time to subscribe to this
newsletter; you're taking time to learn about your computer and
to become a better computer user. And because you're interested
in being a better computer user, most of you aren't buying into
the Norton/McAfee endless loop of subscriptions. You're saving
money as you learn about your computer.
Unfortunately, most computer users don't take the time to learn
more about their computers - they just want to use it. It's true
of a lot of things. I don't want to learn more about my car, I
just want to drive it. Others, who take the time to learn about
their cars, can save hundreds of dollars in maintenance and
repair costs. It all depends on what you like. But you don't
have to know a lot about cars to be a good driver, but you have
to know a quite a bit about computers to use a computer safely
and wisely. They don't build roads that intentionally trick you
into driving off a cliff - but there are companies and sites on
the web that do just that. They lure you in with trickery, then
push you off the cliff in order to make money from you or steal
your personal information (another way to make money). And there
isn't a single security program - free or paid - that is going
to protect you from all the trickery and all the scams that are
so ubiquitous on the Internet today. And it is only going to get
worse. Criminals are honing their craft and it's getting harder
and harder to tell a scam from something worthwhile. The only
thing that stands between you and being duped isn't Norton,
McAfee or any software program - it's your common sense and your
knowledge about your computer.
And even if we warn you a million times and you take care to do
what we tell you to do to be safe, you still have to be aware
and use your common sense every time you go on the Internet.
There are millions of people accessing the Internet in so many
ways - smartphones, PCs, Macs, laptops, netbooks, tablets - who
don't care to know anything more than it takes to get on the
Internet and do what they need or want to do. So the criminals
always have a huge group of unknowledgeable people from whom to
steal money and/or personal information (which is the same as
money).
You can't eat all you want and lose weight. You can't install
one security suite and relax thinking it will protect you.
Nothing can protect you from yourself. The best way to be safe
is to learn all you can and use your head every time you use
your smartphone, laptop, PC, Mac, tablet or netbook and use the
Internet. You can't eat ice cream and cake every day and lose
weight. There is no magic bullet. The best security software is
free - and everyone has access to it - it's called knowledge and
common sense.
There will always be people who will believe that they can eat
anything they want as often as they want and lose weight. They
pay good money for useless diet pills and diet powders that
don't work. And there will always be people willing to believe
that for $60 a year they can do whatever they want on the
Internet and be protected from everything, all of the time. Our
job is to make sure you're not one of them.
Open an
elevated command prompt in Windows Vista or Windows 7
Windows Vista and Windows 7
Don't you just
hate it when you're trying to perform a task in Windows Vista or
Windows 7 that requires you to run a Windows program that
requires you to use an elevated command prompt, and you get the
message that you "must be an administrator" to run it?
Want to know a
quick and easy way to open an elevated command prompt in Windows
Vista or Windows 7? Here's how:
To open an
elevated command prompt in Windows Vista or Windows 7:
1. Press the
Window key
2. Type cmd (in the start menu search) and then press
Ctrl+Shift+Enter. Now click OK or hit ALT+C to confirm F 1 at the prompt. F1 will turn the
background white and the text color dark blue. You can use F4 if
you prefer red text - or you can play around with the number
after F-keys to give you different colors of text. For instance color
F9 gives you a white background with medium blue text. So you
don't have to be stuck looking at a plain, old black and white
DOS prompt window anymore - unless you like black and white :-).
Getting down and dirty with Windows 7's Disk
Defragmenter
Windows 7 -
32bit and 64bit
When your drives become fragmented Windows takes
longer to find the files it needs to perform a requested
operation or to open a program. It's no more complex than that.
So defragmenting your hard drive(s) at least once a month is a
good maintenance routine - one that can keep your computer
running faster longer.
The disk defragmenter that came with earlier
versions of Windows wasn't very good, and most of us went off to
search for good freeware disk defragmenters that were better and
faster than the one Microsoft provided us.
Windows 7's disk defragmenter is really pretty
good, especially if you know a few of its advanced features.
Using parameters to specify what you want defragmenter to do,
is a great way to feel like you actually have some control over
Windows :-) as well as keeping your drives defragmented and
helping Windows to run faster.
For instance, let's say you want to defrag your
Windows drive (usually C). The Windows drive will always be more
fragmented than any other drives you may have because it is the
drive you'll always access most often.
If you just want to see how fragmented your
Windows drive is, you'd do this:
Click start, type in CMD in the start menu
search, and right-click on CMD when it appears at the top of the
menu and choose "Run as administrator". At the prompt type:
defrag C: /A
Note the colon after C: and the space between the C: and the
/A
Now lets see how you can string together
parameters to control disk defragmentation.
defrag C: /U /V
The above command
would defrag drive C and print the progress on your screen -
using verbose output (kind of like this newsletter!)
Now using the list we've provided below, see if you can figure
out what the following commands would do:
defrag C: D: /M
defrag /C /H /V
Here are a list of available parameters and value descriptions
you can play around with when you defrag your drives using
Windows 7's disk defragmentation tool:
/A Perform analysis on the specified volumes.
/C Perform the operation on all volumes.
/E Perform the operation on all volumes except those specified.
/H Run the operation at normal priority (default is low).
/M Run the operation on each volume in parallel in the
background.
/T Track an operation already in progress on the specified
volume.
/U Print the progress of the operation on the screen.
/V Print verbose output containing the fragmentation statistics.
/X Perform free space consolidation on the specified volumes.
Of course you can just use the command defrag C: and defragment
your C (Windows) drive without using parameters at all. The
important things to remember are that Windows 7's
defragmentation tool is excellent, fast, and much better than
the one found in older versions of Windows; and that you defrag
your Windows drive once a month. It's a good habit to get into.
What is Speckie?
Windows XP, Windows Vista, Windows 7
32bit and 64 bit
Some browsers, Google Chrome for instance, have a built-in spell
checkers. Others, like Internet Explorer, don't. Why on Earth
would you need a spell checker in a browser? Let us count the
ways:
Web Mail
Web support forms
Facebook wall posts
Forum posts
Letters to the editor - based on Web forms
Web forms
Social Networking pages and posts
If you use Internet Explorer and you post on Web sites, social
networking sites, use support forms, etc. then your misspellings
will not be corrected. You may find it odd that we're pointing
this out, but do as we say, not as we do :-).
If you're using Internet Explorer 9 and you like it, then you'll
be interested in Speckie - a spell-checker for Internet Explorer
9 (and IE 7 and IE 8 too).Speckie runs on Windows XP, Vista, and
Windows 7 32-bit and 64-bit. As far as we know, it's the only
spell-checker that works with Internet Explorer 9.
So if you use Internet Explorer 9 and you want to make a good
impression, and you want all your site postings and Web form
submissions to be free of spelling errors, you should take a look
at Speckie.
Speckie is a free spell-checker for Internet
Explorer 9. If you happen to be using IE7 or IE8 you can use Speckie too, if
you like. It's a 1.2MB download - and it's free.
You can read more about it here -
http://www.speckie.com/
.
Or go directly to the download page here -
http://www.speckie.com/dload/
Gmail's Recent Activity feature
All computer users
How many of you who have Gmail accounts have noticed the link at
the bottom of Gmail account main page that says "Last account
activity... Details" (which Details being underlined as a
clickable link)?
If you haven't seen it before, open your Gmail account right
now, sign in and click the link "Details" next to "Last account
activity" near the bottom right of the page. If you've accessed
your account recently you'll see when you last accessed it, your
IP address and how you accessed it (Google Toolbar, POP3 (email
program), via your mobile device, or your browser). The IP
address will have your location after it.
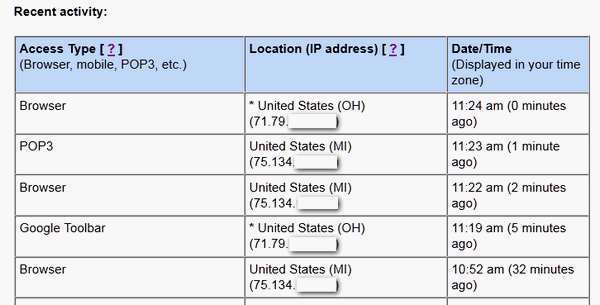
So why would you want to do this? It's a good way to check to
make sure that no one else is accessing your Gmail account - or
snooping around. If
you're using an ISP who does not assign you a static IP address
(one that does not change frequently) then you may find the last
3 digits of your IP address have changed since you last
logged into Gmail. That's fine. However if you see a completely
different IP address, from a different location than where you
are, then you may have a problem.
It's a good time to remind you that your Gmail account's
security is only as good as your password. If you're using a
weak password, then you're playing with fire. You are counting
on luck to keep your account and all the information you store
in it from prying eyes. Please do yourself a favor and change
your passwords to all of your Web accounts while you're thinking
about it. Don't be one of those people who think it can't happen
to them - it can happen to anyone.
Keyboard shortcuts you can use to shut down
your computer
Windows XP, Windows Vista, and Windows 7
Why would you want to use keyboard shortcuts to
shut your computer down? Because you can? Because it's fast?
Because it's cool? We don't know why you'd want to use keyboard
shortcuts to shut your computer down, but we thought you'd like
to know how to do it anyway.
Windows XP
Press the Windows Key then u u
Remember to release each key before pressing the next one - and
do it quickly.
Windows Vista
Well, Vista's shortcut isn't so short, but here
it is:
Windows Key, Right-Arrow Key, Right-Arrow key,
Right Arrow key, u
Remember to release each key first before pressing the next one.
Windows 7
Windows key, Right-arrow key, Enter
Always remember for these shortcuts -- press the keys one at a
time. Oh and one more thing - save all your work before you try
this tip. These shortcuts will shut down your computer and if
you are working on something and you don't save it prior to
shutting down, you're going to lose your work. Of course you
knew that right?
Twelve
computer tips you can use every day
Windows XP, Windows Vista, and Windows 7
-
Change computer time: Right
mouse click on the clock in your system tray (lower far
right) or right click in system tray and choose "adjust date
and time".
-
To save a picture/image from a
web page, right mouse click and choose "Save Picture As" or
"Same image as" (depending on your browser). You can rename
it - if you wish - when you save it to your hard drive.
-
To see how much hard drive/hard
disk space you have left, do this: Double click My Computer.
right mouse click on your C drive (or any hard drive) and
chose properties.
-
Most common image formats are
JPG, GIF, BMP and PNG. The most common image format exported
from a digital camera is a JPG.
-
If you accidently delete a file,
click Control key + Z to bring it back instantly. You can
also look in your recycle bin if you don't realize it until
later, then just right click on the file and choose
"restore" and it will go back to where it came from.
-
If you hold the shift key down
when deleting a file, it bypasses the recycle bin. Control Z
will still bring it back.
-
If you occasionally see a red X
instead of an image on a web page, it is not a setting
problem with your browser. It usually means the webmaster
who made the page put in a bad link.
-
F1 key opens
Windows Help quickly.
-
You can quickly maximize a
window by double clicking the title bar of the window...
this is the big long blue area at the top of your window.
Double click again to bring it back to the size it was prior
to maximizing.
-
Alphabetize the items in your
start menu by clicking Start, Programs, and while hovering
over any program, right mouse click and choose Sort by Name.
-
Quick View of your System: If
you hold the Alt key down while double clicking My Computer,
it will open System Properties Window. This is where you can
find your computer's name, system restore, auto updates,
hardware, and more. The first screen "general" will show you
a lot of information about your system such as what version
of Windows you are using, who the computer is registered to,
how fast your CPU is and how much RAM you have.
-
To open a "Run" command, just
press the Windows Key + R.
A new spam scam which claims to be an IQ test
All computer users
E-Diagnostics is a scam. You may get an email (or several
emails) which looks likes it came from one from your friends or
a company you have done business with. The email makes it looks
like a friend or a company has send you an email. The email
contains a short message and you’re asked to click a link to
visit the E-Diagnostics Web site, supposed to take an IQ test.
But E-Diagnostics is a spam-scam dating site that purports to
match you with people of similar IQs or interests. E-Diagnostics
is a company which promotes itself via spam – it lures people to
signup and then coaxes them into connecting their MSN, Yahoo, or
Gmail accounts with E-Diagnostics. In other words, they promote
via spam, but with a twist. The twist is they disguise the spam
by making it look like it came from a company or person with
whom you may be familiar.
The link in the email does not lead to a download or a Trojan, a
virus, or any sort of malware. Clicking the links in this email
leads to an IQ test which leads to the real purpose of the email
– to get you to promote their scam dating and test sites via
spam.
The important thing for you to remember is: don’t click any
links in any email from E-Diagnostics. You can easily recognize
the email because it always contains the following message –
only the supposed sender’s name changes:
“(Whatever name here) has written you a message…
You can view the message on E-Diagnostics, the platform for
personality and intelligence tests that are also fun! To read
your message now, go to the following link…”
Do not click links in this email. Do
not click "Unsubscribe". Just delete the email and save yourself
a lot of trouble and a lot of spam.
Get the "Windows 8" look
on your Windows 7 computer
Windows 7 - all versions
I’m not so sure what to
think about Windows 8. It looks to me like a cell phone run amok.
The big rectangular buttons on the desktop do nothing for me, but
they may be really cool for the Starbuck’s generation. Maybe I’m out
of the loop.
One thing for sure, Windows 8 won’t look (by default) like any
Windows before it. It’s odd that Windows 8 continues be modeled
after the spectacularly unsuccessful Windows Phone – which has been,
so far at least, a notorious flop.
Maybe you’re in the Starbuck’s crowd – or you want to be. Maybe you
just want to get a head start on Windows 8, or maybe, like me, you
just want to get feel for it and then go back to Windows 7. If you
want to give the Windows 8 look a try without affecting your current
Windows 7 system, you’ll want to give The Mosaic Project a try. All
you have to do to run it is to download the zip file, unzip it and
click on the executable (mosaic.exe). You don’t have to install
anything – and you can exit at anytime and go back to your old
Windows 7 look.
The Mosaic Project is still in beta testing which means there are
some bugs and issues with it. If you’re not comfortable with that,
please don’t download it. If you’re adventurous to a point, and
would like to get a feel for how Windows 8 might look (it’s modeled
after current milestone builds of Windows) then you should download
it and give it a try.

Do you like big bright
buttons? Would you like your desktop to look like a cell phone? Do
you like change? If you would like to see what your desktop might
look like running Windows 8, then you might want to give Mosaic a try.
You can get more
information and/or download Mosaic from here.
Note: Mosaic is beta software. It’s small zipped file (572KB) which
you download and unzip. Just click on the executable file to run it
– in other words you don’t need to install anything. You can easily
exit Mosaic by clicking the arrow on the desktop and selecting
“Exit” from the menu. Be sure you check out the program options.
Click on the arrow on the desktop and choose “Options.”
Think before you
click
Windows all versions
What's the first thing you learned when you first started to use a
computer? If you think about it, the first thing you learned to do
was to click things. You have to click an icon to open your email or
browser. You have to click a link to go to a web page. All of us,
when we first start to learn computers are click happy. It's fun.
How many other things can you do it life and get instant results? On
a computer, you click something and something usually happens.
Everything these days
is just a click away - including BIG trouble. And clicking can
sometimes become a knee-jerk reaction. There's just something
fascinating about a hyperlink. You just
want to click it .
How many of you clicked the previous sentence? It looks like a link,
but it's not. And we hope by now you trust us enough to know we're
not going to put any dangerous links in our newsletters. But admit
it, even if you didn't click on that sentence, you were tempted to,
right?
Criminals and
pranksters and spammers - all of the malevolent ones who lurk on the
Internet, prey on those who just cannot resist a link. And even
those of us who know better than to click links when we shouldn't
sometimes find ourselves wondering where the link leads to.
Despite what some
experts say, if someone gets their identity stolen is by clicking a
link that leads to a phishing site.
The quickest way to
get your computer infected with bots, viruses, spyware, adware and
malware is to click links without thinking. Even if you have the
best antivirus and the two best antispyware programs installed and
updated on your computer - you shouldn't be clicking links in
untrusted emails or Web sites of which you're not sure.
There are new viruses
and Trojans being introduced to the Internet every day. The ones
being developed now are highly evolved. And in the last couple of
years a new threat has emerged called rogue security programs --
rogues are arguably the threat that most of us are most likely to
encounter.
Rogues are
particularly tricky because they appear to be legitimate programs,
and install as legitimate programs, but once installed they proceed
to shut down your security programs (antivirus, antispyware, etc.)
and proceed to unload their nefarious and sneaky bundle unto your
computer. And once that happens, your computer is helpless and
unless you pay the ransom (the price of the rogue security program)
you're helpless too - unless you know the right things to do to get
rid of it. If you see a warning while you're browsing the Web that
tells you your computer is infected and to "click here" to scan your
computer and remove the malicious files, don't click, or you'll be
sorry. Think before you click.
Recently a very good
friend of mine had a problem. He clicked a link in an email that he
shouldn't have - it appeared to have come from a friend. By the time
he called me, it was too late. He had to format his computer and
reinstall Windows - and three weeks later he is still reinstalling
all his programs because he didn't listen to me when I told him to
keep a good, mirror-image backup. He does listen to me now though.
The link downloaded a Trojan and a virus which spread through his
computer so quickly once it started spreading it was already too
late. Think before you click. My friend is not a beginner. By
anyone's standards he's very smart and very careful. But because one
time he didn't think before he clicked, it cost him a lot of time
and a lot of aggravation. It could have cost him a lot more.
Whether you're
talking about computers or the Internet - everything is just a click
away. Not thinking before you click a link could cost more than time
- it could cost you personal information or money. Software programs
cannot think - but you can. Antivirus and antispyware can only
protect you from malicious files and programs - but they cannot and
never will be able to protect you from yourself.
Yes, when you're on
the Internet everything is
just a click away - and so is having your computer ruined, your
identity stolen or your bank account drained.
Think before you click.
Do you have a tip or trick to share, or something
you'd like us to research?
Let us know!
What's the difference between
antivirus and antispyware?
Antivirus software protects your computer from viruses, Trojans,
worms and rootkits. Since all viruses work in a similar way they all
have certain commonalities that identify them as viruses. The same
is true of worms, Trojans, and rootkits. Antivirus software detects
the characteristics of these forms of malware. To oversimplify a
bit, antivirus software only has to identify the activity of these
forms of malware since viruses, trojans, worms and rootkits all have
characteristics that identify them for what they are. If a virus
didn't display virus-like activity, it wouldn't be a virus right?
Antispyware software has a more difficult task, there are so many
different kinds of spyware. There is spyware that will log your
keystrokes, but that kind of spyware is totally different from the
kind of spyware that tracks your web browsing and tracks your
behavior online - most often so it can display "relevant"
advertising which may appear as popups on your computer that seem to
come from nowhere. There are spyware programs that track you, send
information about you back to the company from whom you downloaded
the software. Then there is adware which is similar to spyware but
different in that it may only display random ads that come with the
program - in which case it's not really spyware at all, or it may
use data collected from your computer - your browsing history for
example - to display ads target to what the program thinks you're
most likely to buy. And there are other forms of spyware too.
Whereas viruses are written to harm your computer, spyware isn't.
Spyware is generally written to "spy" on you, not to harm your
computer. Most spyware is created to make money from you. And there
are thousands of new spyware programs being released on the Internet
every day and they're all different. So antispyware software has a
bigger challenge than antivirus software - and that's why we
recommend you use at least two good antispyware programs. There is
just too many spyware and adware programs that already exist and too
many new ones being released every day for one program to keep up
with them all.
Antivirus software is more efficient because the kinds of malware it
is designed to detect and prevent all have certain characteristics
that are identifiable; antispyware software has to detect all kinds
of spyware software, some of which have no common and definable
characteristics. You need both antispyware and antivirus software
installed on your computer - they're two different animals which
protect you from different kinds of threats.
Viruses can severely damage your computer, and Trojans and worms can
be devastating to your privacy. Spyware and its cousin adware can
cause your computer to slow to a crawl, cover your screen with
unwanted and annoying pop-up advertisements, and jeopardize your
privacy. Antivirus software isn't designed to detect and remove
spyware and antispyware isn't designed to detect viruses.
To keep your computer safe and your privacy guarded, you should run
one good antivirus program, and keep it updated, and you should run
two updated antispyware programs.
 Available
now at our Donation Station!
USB
2.0 Expandable Memory Card Reader
SUPPORTS 10 Different kinds of Memory Cards!
This high-quality USB 2.0 Expandable USB Flash Memory Card
Reader Pen Drive allows you to flexibly transform your supported
flash memory card to a portable pen/flash drive. Use it to read your
camera's SD card if you don't have a SD card slot on your
computer... you won't have to hook up your camera to transfer
pictures from your SD card. Use it to transfer data from any device
using a memory card to your computer!
Slide your SD/MMC/Mini
SD/RS MMC/T-flash memory card into this expandable pen drive and
transfer your data or photos to your computer without cables. This
expandable pen drive allows you to turn any memory card into a USB
flash drive in seconds!
Specifications:
-
Supports SD, MMC, MMC II, RS MMC, Ultra II SD,
Extreme SD, Extreme II SD, Mini SD, MMC Micro, and T-Flash
-
LED indicator lights
-
Transform supported flash memory card to a
portable USB flash drive.
-
Hot swappable (Swap memory cards without
unplugging from the computer.)
-
Change to a different flash memory card at
anytime
-
High-speed USB 2.0 supported
-
Use it to read your camera's SD card if you
don't have a SD card slot on your computer. Then you don't have
to hook up your camera to transfer pictures from your SD card.
Computer has no card reader? No problem. Put your
camera's flash memory card into this USB flash drive/Card Reader and
plug it into any open USB slot on your computer! Or use your flash
memory card as a USB Flash Drive! Use it to transfer data from any
memory card to your computer in a flash!
Get
your USB 2.0 Expandable USB Flash/Pen Drive with SD/MMC Card Reader
Pen Drive today!
|
Our software
recommendations |
- Our
new #1 choice in registry cleaners and optimizer. Easy and safe.
It's a winner. Save
$20 on
Registry Commander right now - or get more information about
Registry Commander here. New! Use your license on 2
computers!
SUPERAntiSpyware
Superior antispyware protection - lifetime
license - on sale now! Now our #1 choice for antispyware
protection.
Captain
Optimizer - Save $20 on the program that won our
best new software of 2010 award! Use your license on two
computers!
Read
more here.
Minneapolis and Other Things We Stole
Minneapolis is a name that we (white people) stole from the Indians,
or to be more PC: Native Americans. We stole a lot of things from
the Indians, but not the Cleveland Indians; we can't blame those
Indians on the real Native American Indians.
We stole a lot of names from the Indians. White folks are good at
stealing things and making a lot of money. Take Windows for example
- or Facebook. See? It's true.
I digress. We stole the names of a lot of states from them: Ohio,
Michigan, Minnesota, Iowa, and some others. We stole the names of
cities from them: Minneapolis, Sandusky, Huron, Pontiac, etc. We
stole their land and their women. We even stole their bison and
called them buffalo.
Read
the rest of this essay here.
|
This
week's freeware pick |
LastPass Free
Password Manager, Password Generator and more
Windows XP, Windows Vista, Windows 7
32bit and 64bit
Works with all major browsers (IE, Firefox, Chrome, and Safari)
Download size depends on the version you download (between 10-12MB)
We really wish this would be the last pass for us reminding you how
important using strong passwords for all your online accounts is. We
really wish this was the last pass for us reminding you never to use
the same password twice for anything. We really wish that this was
the last pass for reminding you how important passwords are and how
passwords are the best line of defense you have against getting your
personal information stolen.
But we're all human. Most of us are reactive and not proactive. We
wait until something happens and think "If only I would have...." or
"I knew what I should have done." We do learn well by painful
lessons. But some lessons are more painful and costly than others.
Having your online banking account password guessed (not stolen) by
someone who guessed your password was 12345 or password or
dsmith1281.... is painful and costly. Having your Yahoo or Gmail or
Hotmail account accessed is painful and possibly embarrassing...and
maybe costly too, if you have any of your credit card information or
banking account details stored in your online mail accounts (which
you shouldn't have).
Today we're featuring one of our favorite freeware programs. It's
called LastPass. LastPass is a password manager. In today's cloudy
Web you need a password manager. Period. Whether you want to take
our advice and get LastPass Free or pay for Roboform, or you think
you have a better one, get a password manager.
Now I've been using LastPass for over two years now and I'm
perfectly happy with it. I am perfectly happy with not knowing any
of my LastPass generated complex passwords. If someone tied me to a
stake and drove bamboos shoots into my toenails, I couldn't save
myself because I really don't know what my passwords are. Most of
them look like this:
NV88%41LBjaT4
I love it. Who in the world is going to remember that or guess that?
No one. That's want I want. All I ever have to remember is my master
password to LastPass and all my other passwords are unlocked - but
only for me. And when I visit a Web site that requires a username
and password, LastPass fills it in for me - automatically.
Oh really? You say your browser does that for you? And what happens
when your kids, grandkids or someone else uses your browser. Do you
have it set up to require a master password before you auto-login to
your accounts? Does your browser generate strong, uncrackable
passwords? Does your browser have a Secure Notes feature where you
can store sensitive information in encrypted form? No? Your browser
was free, and so is LastPass so why are you still using your
browser's password manager anyway? If you're using your browser's
built-in password manager on a laptop, you're taking an even bigger
chance - unless you're one of the astute ones who knows how to
password protect your browser's password store. And no we're not
going to tell you how to do that - because storing your passwords in
your browser doesn't give you the security or the features of
LastPass. You still wouldn't have a password generator - which
generates and remembers complex strong passwords. And you still
wouldn't have a Secure Notes feature.
The time has come to stop using weak passwords. The time has come to
stop using the same password for everything simply because you're
afraid if you use a different password for everything you'll forget
your passwords. The time for storing your passwords in a Word doc
(we know some of you do that) or printing them out on paper and
locking them in a desk drawer (yes we know some of you do that too)
is long past. We all live in the age of the cloud and it's getting
cloudier and cloudier. Whether you like the cloud or hate the cloud
doesn't matter. The cloud is going to continue to grow and become
more and more of your Internet life.
LastPass Free is our freeware pick this week. That means it costs
you nothing - zero - nada. LastPass works with Windows XP, Windows
Vista, and Window 7 - both 32bit and 64bit versions of them all.
LastPass works with your browser whether you use Internet Explorer,
Google Chrome, Firefox, or Safari. You've really got no excuse
anymore to be using weak passwords or worse, the same weak password
for everything.
You can read more about LastPass from
https://www.lastpass.com/
- if you don't need to read more, and want to jump right to the
download, you can download LastPass Free from here.
https://lastpass.com/misc_download.php .
The master password you set unlocks LastPass and after you've
entered your master password, LastPass will automatically fill in
your username and password for every account you've created in
LastPass. And even creating accounts in LastPass is automatic. Go to
a site which requires you to log in, type in your username and
password and LastPass will ask you if you want to save your password
and username in LastPass. If your passwords are week, you can have
LastPass generate new ones for you and remember them too.
There's no excuse for anyone to be roaming around the Web without a
password manager anymore. LastPass Free costs nothing, it's easy
enough to learn to use that even Web neophytes can use it.
LastPass Free is one of our
favorite freeware programs and one saves us time and aggravation.
Get LastPass right now and
start shoring up those weak passwords before you learn the hard way
that weak passwords are bad for you and your personal information.
Don't wait until you experience a painful lesson in Internet
security - weak passwords are an invitation to big trouble.
InstaPaper
If you are like us then
you'll probably have times when you find some interesting articles
you'd like to read later. And there are several browser add-ons that
will let you do this. But today I found one that not only works as a
browser bookmarklet, but lets your create folders to store your
articles in and read them later - at your convenience. But not only
can you read them later on your own PC (and this is why I found this
service particularly interesting) you can read them on any PC - as
long as you remember your login information.
But wait! There's more! You can also read your saved articles on
your iPhone, iPad, Kindle e-reader, or Nook e-reader (or any
e-reader which supports epub format, which is most.) I have a Nook
and with a Nook you can "side load" your saved epub files from your
computer to your Nook's "documents" folder.
The service (and the site) is called InstaPaper. It converts
articles that you want to read into a newspaper-like format. This
makes it easy to read. All ads and other distracting images are
removed, leaving you with just the article, clean and nicely
formatted.
The basic service is free. The developer makes it clear how he funds
his free service - by selling smartphones apps and from
advertisements on his Web site.
If you're an avid reader and you find yourself reading articles
online often, we're betting you'd really love InstaPaper.
InstaPaper requires you to create an account, but all you need is an
email address and a password to create one. It's free.
You should spend a few minutes reading the FAQ and other information
on the site. It is easy to use but could be made a little easier by
making some of the features more noticeable. InstaPaper has a lot of
features you could miss if you don't take a few minutes to read the
FAQ and other helpful information on the site.

If you do a lot of reading
on the Web - take advantage of our Site of the Week and the free
service it offers. It's called InstaPaper - we think it's great -
and if you're a reader you'll think it's great too.
Visit InstaPaper right now
and sign up for a free account. Your reading will be more
comfortably that's for sure.
InstaPaper is our Cloudeight
Site Pick this week. We hope you like it!
Twitter, InfoAve Daily and Facebook
We've been very active on our Twitter and Facebook pages recently.
You can follow us on
Twitter here.
Also
we've got a new daily tips and tricks newsletter that we send every
weekday afternoon around 7PM Eastern time. It's free and you can
sign up for it at
http://thundercloud.net/start/subscribe.htm. It's a great way to
review some of our best tips from all the past issues of our
newsletters.
We like you! And we'd like you to like us on
Facebook. We're not too proud to beg! Walmart has more friends than
us! We gotta do better! Cloudie is hurt.
Please take a second and "like us" on Facebook by
clicking on Cloudie. You won't hurt him. He's ticklish! He likes it.
Hotmail, MSN outage sparks doubts about Microsoft cloud
For a few hours last night, millions of Hotmail users and other
Microsoft online services were unable to access or use their
accounts, which led to the usual en masse griping on Twitter and
Facebook. While service seems to be restored, the outage might have
a lingering impact on the perception of the company's future in
cloud computing.
Not only was Hotmail down, but also Skydrive, MSN and Office 365.
As BBC News reported, "Such a major problem is likely to raise
questions about the reliability of cloud computing versus local
storage. Especially embarrassing is the temporary loss of Office
365, the company's alternative to Google's suite of online apps."
Continue reading...
Microsoft removes AVG app from Windows Phone Marketplace
Microsoft has pulled an AVG antivirus app from the Windows Phone
Marketplace after learning that it was improperly gathering and
sending certain user data back to AVG.
In a tweet posted yesterday, Microsoft's Brandon Watson, Director of
Developer Experience for Windows Phone, confirmed that the app had
been removed based on the company's own investigations and research
done by a couple of external experts.
Launched earlier this week, AVG's new antivirus app for Windows
Phone quickly triggered concerns among users, according to
WinRumors. Digging behind the scenes into the app's codebase, Justin
Angel, a former Microsoft employee, and Rafael Rivera, a
self-proclaimed Windows hacker and author of the Within Windows
blog, uncovered the reasons for concern.
Rivera found that the app just displays ads and scans for EICAR test
strings, which is simply a file used to test antivirus software.
Noting that "there just isn't any malware to scan for on Windows
Phone," Rivera dubbed the app "AVG-owned scareware."
Continue reading...
Important Links:
Submit your questions, comments, and suggestions for possible
inclusion in our newsletters here. This form is for
questions, comments and suggestions for this newsletter, not for
product support, stationery questions, or general questions
concerning our products or services.
Submit your Windows
tips and tricks here.
Send us your
suggestions and recommendation for future freeware picks and/or
sites of the week.
Follow us on Twitter
Visit this page
if you're having problems getting our newsletter - or if you
think your ISP is blocking, censoring or deleting this
newsletter.
If
you need help with one of our software programs, have a question
about an order, or have a question about any of our email
stationery, screen savers, or other products - please don't use
our InfoAve Questions/Answers/Tips form.
Please
use our general Cloudeight support form
instead.
Recommended security applications
Microsoft Security Essentials version 2 - excellent anti-virus
protection. Free and easy to use - easy on resources.
AVAST Anti-Virus (free version for personal/home use - updated
to Version 5) AVAST continues to offer and support their free
version.
AntiVir (free personal version available) now compatible with
Windows Vista and Windows 7.
NEVER
INSTALL MORE THAN ONE ANTIVIRUS PROGRAM!
No
anti-virus can protect you if you do not keep it updated. Update
your anti-virus at least twice a week or more. Install and use only
one anti-virus program. Installing two does not give you twice the
protection. On the contrary, installing two could result in reduced
protection and many computer problems.
Also,
it's very important that you keep your Windows updated with the
latest patches, fixes, and updates. If you don't have Automatic
Update turned on, you should consider turning on Windows updates -
at least to notify you when updates are available. You can still
choose when to install them, not install them or install them
automatically. If you don't install Windows updates you could be
leaving yourself vulnerable to emerging threats. We highly recommend
you install all Windows updates as soon as they become available.
Recommended anti-spyware programs
(install two anti-spyware
programs for the best protection)
SUPERAntiSpyware
Superior antispyware protection - lifetime license -
on sale
now! Use your license on two computers - it costs less than
$12.50 per computer for a lifetime of spyware/malware protection.
Pay once - never pay again. SUPERAntiSpyware is our #1 choice for
antispyware protection.
Recommended firewall
We do
not recommend any third-party firewalls. We do recommend you use the
Windows Firewall and leave it turned on.
Other
recommended programs
These programs can help protect you
and your computer in other ways than anti-spyware/anti-virus
programs.
Malwarebytes
(free version - no real-time protection - but very useful anyway.
Malwarebytes (Pro version) - includes real-time protection -
lifetime license.
Always
keep your common sense with you when you're on the Internet. Don't
be lured into installing free software or signing up for a free
service if it seems too good to be true. Research it - google it!
Read the privacy policy and/or Terms of Service or License Agreement
of any free software or free service you're considering. As a rule
of thumb, free products and free services which have extremely long,
difficult-to-understand agreements are most often deceptive in
nature. Be careful and stay informed - you'll be just fine. The
internet is the greatest source of information ever - and it's all
right at your fingertips. And despite all the nonsense and
misanthropes that hide in the shadows, the Web is a wonderful place.
Play it safe, use common sense, and enjoy all the internet has to
offer.

Visit Our Donation Station
Padded neoprene USB Flash Drive Holder Key Chain
Executive ballpoint pen + 2GB USB ReadyBoost Flash Drive in a
metal case
USB 2.0 Flash drive/Memory Card reader - supports 10 different
kinds of flash memory cards
HubbaMan 4-port USB hubs
USB Wristband Flash Drives
4GB ReadyBoost Flash Drives
6-pocket USB flash drive/SD card holders
Donate Any Amount - Donate any amount no matter how
small and choose a registered version of FolderMagic,
CalendarPal, or Smileycons. Any amount no matter how small helps
- and you can choose your gift just for helping us
If you can help us right now, we'd really appreciate
it. But we know that many of you are having problems as well with
the world economy being what it is. If you can't afford to help us
financially, you can help us by
using our Start Page.
Our Start Page now
has over 100 free games you can play, plus breaking news and daily
tips and tricks. It costs nothing to use our Start Page - and you
don't even have to register.
Use our Start Page
as your start page and you'll be helping us without spending a dime
InfoAve Daily
Tips & Tricks
We're offering something we think most of you will
enjoy. We're offering a daily tips and tricks summary newsletter
that is sent everyday. It's a summary of daily tips, freeware picks,
and site picks - so it's very brief and lightweight. If you'd like
to receive or daily tips and tricks newsletter (completely free, of
course) you
can subscribe here.
Don't forget... you can also help us by using our
Start Page. We have
added over 100 free games to our Start Page. It costs you nothing to
use our Start Page
--and helps us a lot.
Thank you very much for
subscribing to InfoAve Premium. We appreciate your help and your
support very much.
Have a great weekend!
Eightball & Thundercloud
Cloudeight InfoAve Premium Edition Issue # 412
Volume 8 Number 49
September 9, 2011
IMPORTANT DISCLAIMER
ABOUT SOFTWARE RECOMMENDED IN THIS NEWSLETTER
All software recommendations we make in this
newsletter are based on our own experience and testing of the
programs that we recommend. This does NOT guarantee they will
work on YOUR computer. We assume you will read the program
documentation and use the program according to the instructions.
We make no guarantees about any program recommended in this
newsletter or its suitability for any particular purpose. We
will not be responsible for any problems you may have. We do not
and cannot provide support for any products other than our own
Cloudeight products and we will not answer email concerning any
product which is not a Cloudeight product. We urge you to use
good judgment when downloading and installing software and to
use a program only after reading the program's documentation.
And, all Tips & Tricks in this newsletter have been tested by us
on several different computers and were found to work as
indicated. They may not work on yours. We make no guarantees.
Anything we recommend you try and use at your own risk. We will
not be responsible for any problems caused by any software
programs recommended in this newsletter or any of the tips and
tricks in this newsletter.
Readers' comments are their
own and Cloudeight Internet LLC is not responsible for comments
of our readers. All readers' comments, suggestions, questions,
and tips and tricks sent to us become the property of Cloudeight
Internet LLC. You understand that we may use your comments
without your explicit permission.
InfoAve Premium is published by:
Cloudeight Internet LLC
PO BOX 73
Middleville, Michigan
USA 49353-0073
This newsletter is sent from the address
infoave-premium/@/pr1.netatlantic.com . The IP address for
Netatlantic is 69.25.194.2. Netatlantic is a respected newsletter
hosting service. We have used their services for many years. All
content is copyright ©2011 by Cloudeight Internet LLC (all rights
reserved). |